Virginia-based company KLC Network Services, known for its IT, AV, and cyber solutions, has allegedly become the latest victim of a ransomware attack. Play ransomware group has claimed responsibility for the KLC Network Services cyber attack.
Founded in 2001, KLC Network Services is a Service Disabled Veteran Owned Small Business (SDVOSB) business in Herndon, Virginia and provides services to clients, including the Department of Defense (DOD) and the US Army.
Its workforce includes professional technologists, analysts, and engineers dedicated to US security, defense and intelligence missions worldwide.
The Cyber Express has contacted the company to verify the authenticity of the attack but has not received any official response from the company.
KLC Network Services cyber attack: Everything we know so far!
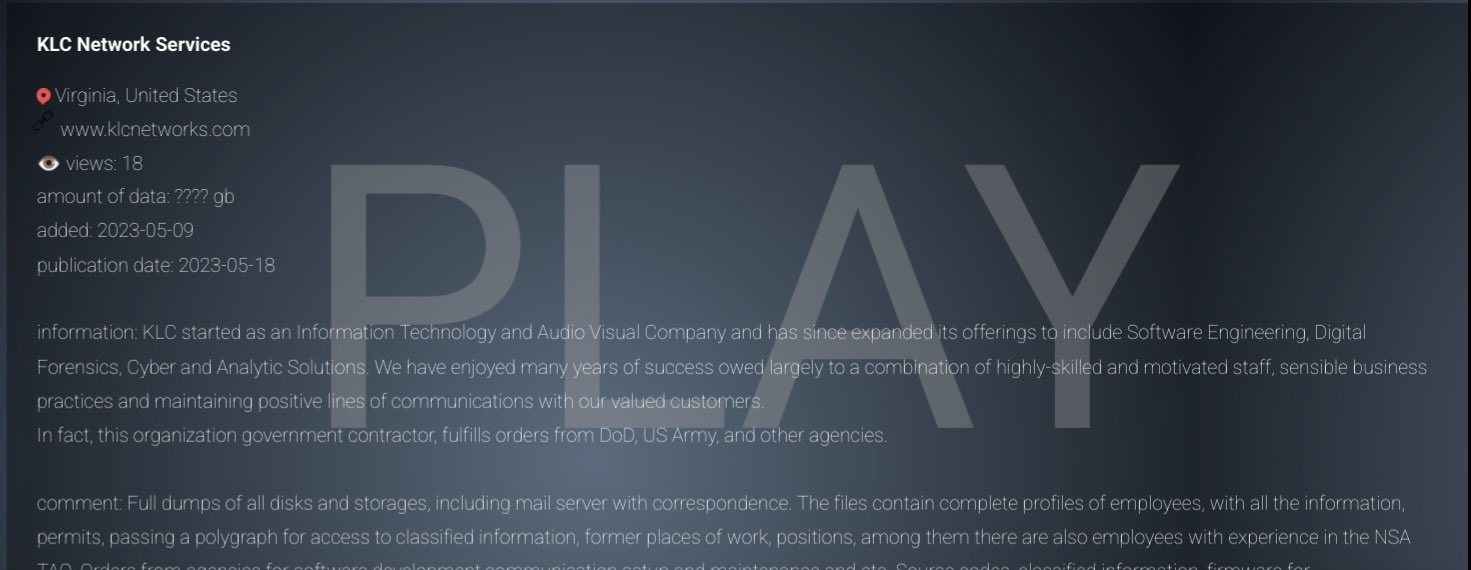
Cybersecurity analyst and security researcher Dominic Alvieri reported about the alleged KLC Network Services cyber attack.
He also posted screenshots related to the incident. Among the screenshots, one mentions the information and details the hackers have been able to steal from the company.
The files contain complete profiles of employees, with all the information, permits, passing a polygraph for access to classified information, former places of work, positions, among them there are also employees with experience in the NSA”, read the post by the hacker group, as highlighted in the image shared by Alvieri.
If true, the KLC Network Services cyber attack encompasses a lot of information as the attackers allegedly penetrated the company’s network, gaining access to sensitive data, including comprehensive employee profiles.
These profiles held personal information, permits, and details of employees who had undergone rigorous polygraph tests to access classified information.
Moreover, the attackers claimed to possess complete dumps of all disks and storage devices, even seizing the mail server and its entire correspondence.
KLC Network Services cyber attack: Why companies are failing against Play ransomware gang?
Over the years, KLC Network Services has expanded its repertoire, becoming a trusted government contractor and fulfilling critical orders from various agencies.
However, KLC Network Services cyber attack immediately puts the company’s information at risk because the ransomware gang in question has been reported attacking multiple companies and has been using two sets of tools to for doing so — Grixba (network-scanning tool) and VSS Copying tool (a .NET executable tool for manipulating shadow copies using APIs).
According to the Symantec Enterprise report on the ransomware gang, attackers have discovered ingenious methods to extract data that is usually inaccessible due to the operating system’s protective measures.
The notorious Play ransomware gang has recently devised a pair of novel, tailor-made tools to identify all users and computers within a breached network systematically.
Moreover, they have successfully bypassed the conventional restrictions imposed by the operating system by illicitly duplicating files from the Volume Shadow Copy Service (VSS).
This unprecedented breakthrough has granted them unrestricted access to valuable data previously out of their reach, thus amplifying the threat posed by their malicious activities.

