Security researchers from zLabs have discovered a more advanced version of the Konfety Android malware, which uses complex ZIP-level changes to avoid detection and mimic genuine apps on the Google Play Store, marking a dramatic increase in mobile dangers.
This malware employs an “evil-twin” strategy, where malicious versions distributed through third-party sources share identical package names with benign apps available on official stores, thereby enhancing its stealth and deceptive capabilities.
Advanced Evasion Tactics
By tampering with the APK’s ZIP structure such as enabling the general purpose flag (bit 00) to falsely indicate encryption and declaring an unsupported BZIP compression method (0x000C) for critical files like AndroidManifest.xml Konfety disrupts common reverse engineering tools.
These alterations cause utilities like APKTool and JADX to either prompt for non-existent passwords or crash outright, preventing extraction and analysis.
Interestingly, Android’s installation process gracefully handles these malformed packages by falling back to treating files as stored rather than compressed, ensuring seamless deployment without alerting users or the system.
The malware’s adaptability is further evident in its dynamic code loading mechanism, where encrypted assets within the APK conceal a secondary Dalvik Executable (DEX) file.
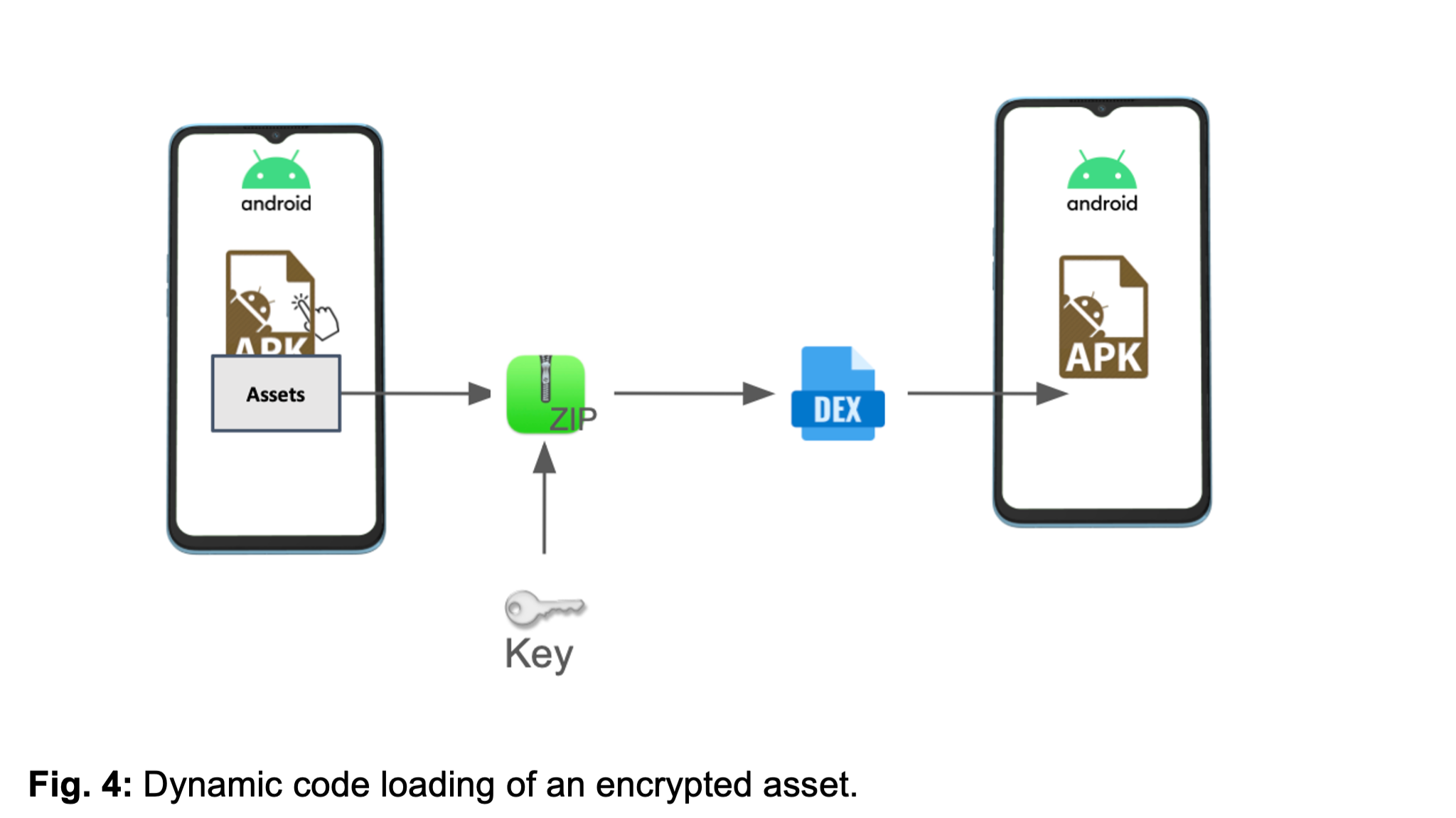
This hidden DEX, decrypted and executed only at runtime, contains undeclared components such as activities, services, and receivers that are referenced in the manifest but absent from the primary codebase.
This obfuscation technique not only shields malicious logic during static scans but also integrates with the CaramelAds SDK for ad fraud operations.
Although the SDK itself is not malicious, Konfety exploits it to fetch advertisements, sideload payloads, and maintain covert communications with attacker-controlled servers, all while mimicking legitimate app behaviors through geofencing and icon hiding.
User Exploitation Revealed
Analysis confirms Konfety’s ties to prior campaigns, including those reported by Human, through distinctive markers like a User Agreement popup and a regular expression pattern (@injseq) embedded in the code.
Decoy applications on the Play Store, bearing the same package names but lacking any malicious functionality, serve as perfect camouflage, allowing the malware to blend in without replicating genuine features.
Upon execution, Konfety redirects users to fraudulent websites via browser instances, initiating connections to domains like hxxp://push.razkondronging.com/register?uid=XXXXXX, which cascade through redirects to sites that coerce installations of unauthorized apps or enable persistent browser notifications.
This results in spam-like alerts and unwanted app sideloads, severely impacting user privacy and device integrity.
The threat actors demonstrate high adaptability, frequently updating targeted ad networks and evasion methods to outpace detection systems.
By combining ZIP tampering with runtime decryption and deceptive manifest declarations, Konfety exemplifies the evolving sophistication of Android malware, posing challenges for security professionals and underscoring the need for advanced analytical tools resilient to such low-level manipulations.
Users are advised to scrutinize app sources, enable Play Protect, and monitor for unusual network activity to mitigate risks from this persistent threat.
Stay Updated on Daily Cybersecurity News. Follow us on Google News, LinkedIn, and X.
