A sophisticated malware strain known as KorPlug has emerged as a significant threat in the cybersecurity landscape, employing advanced obfuscation techniques to evade detection and complicate analysis efforts.
This malware represents a particularly concerning development due to its implementation of O-LLVM obfuscation mechanisms, which transform conventional program structures into highly complex control flow patterns that resist traditional reverse engineering approaches.
The KorPlug malware initiates its attack sequence through DLL side-loading techniques, targeting legitimate utilities to achieve initial code execution.
The malware’s payload, identified with SHA-256 hash b6b239fe0974cf09fe8ee9bc5d0502174836a79c53adccdbb1adeb1f15c6845c, operates as a 624 KB x86 PE file that circumvents standard Windows DLL loading procedures through shellcode-style execution via the EnumSystemGeoID API function call.
.webp)
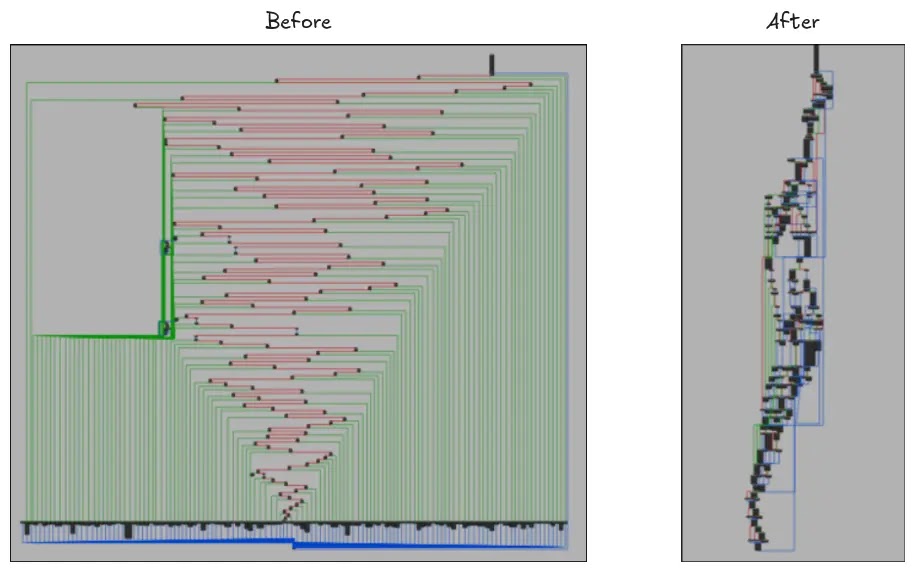
RevEng.AI researchers identified that the malware’s second-stage payload exhibits an anomalous Control Flow Graph structure within its Initialize function, presenting significant analytical challenges to both static disassembly and dynamic analysis methodologies.
The researchers discovered that KorPlug leverages O-LLVM compiler infrastructure modifications to implement three primary obfuscation strategies: control flow flattening, bogus control flow injection, and instruction substitution.
.webp)
The malware’s impact extends beyond typical evasion techniques, as it fundamentally alters the binary’s execution architecture to defeat signature-based detection mechanisms and substantially increase reverse-engineering difficulty.
Traditional deobfuscation tools, including publicly available solutions, demonstrated limited effectiveness against KorPlug’s sophisticated obfuscation implementation without significant modification.
Advanced Control Flow Obfuscation Analysis
The KorPlug malware’s most distinctive characteristic lies in its implementation of control flow flattening, which transforms conventional function structures into switch-based dispatch mechanisms.
This obfuscation technique creates a complex network of interconnected basic blocks that obscure the malware’s true operational logic.
.webp)
The obfuscated Control Flow Graph contains several critical components that researchers must identify for effective analysis.
The pre-dispatcher block serves as the primary entry point, characterized by an unusually high predecessor count relative to other basic blocks.
This component contains minimal operational logic, typically consisting of an unconditional jump instruction directing execution to the initial dispatcher block.
def identify_relevant_blocks(cfg):
relevant_blocks = []
for block in cfg.nodes():
if has_state_variable_assignment(block):
block_type = classify_assignment_type(block)
relevant_blocks.append((block, block_type))
return relevant_blocksThe dispatcher mechanism operates through manipulation of a designated state variable, with individual basic blocks assigning discrete values to control subsequent execution paths.
Backbone blocks contain the core transition logic, utilizing JMP, MOV, SUB, and JZ operations to evaluate state variable contents and facilitate calculated jumps to appropriate successor blocks.
RevEng.AI’s analysis revealed that effective deobfuscation requires systematic mapping of state variable values across all relevant blocks, followed by correlation with backbone block comparison operations to reconstruct the original execution sequence.
.webp)
The deobfuscation process involves binary patching operations that redirect execution flow directly to intended successor blocks, effectively restoring the function’s original control flow structure while bypassing the obfuscated dispatcher mechanism entirely.
Boost your SOC and help your team protect your business with free top-notch threat intelligence: Request TI Lookup Premium Trial.




