A Brazilian cybercriminal group has refined its long-running malware distribution campaign by incorporating innovative social engineering techniques and multi-stage infection chains to deliver the Lampion banking trojan.
The campaign, which has operated continuously since at least June 2024 following its initial discovery in 2019, demonstrates the threat actor’s commitment to operational stealth and evasion.
The Lampion stealer specifically targets Portuguese banks and uses a complex infection chain designed to evade detection at multiple stages while maintaining persistence on victim systems.
Security researchers have documented significant tactical evolution in the threat actor’s approach, revealing the use of ClickFix lures, compromised email accounts, and sophisticated infrastructure that has maintained active infections in the hundreds while generating dozens of new daily compromises.
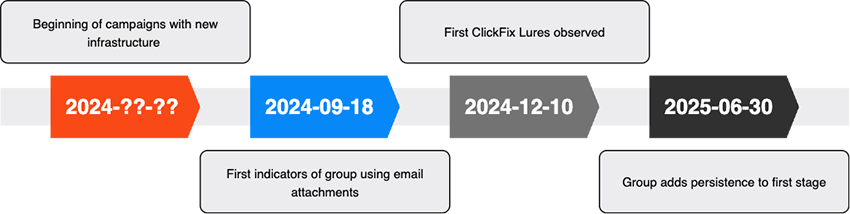
The threat actors introduced three major tactical shifts during the campaign’s recent evolution.
In mid-September 2024, they transitioned from distributing ZIP files via direct links to embedding them as email attachments. This change appeared designed to increase victim trust by eliminating external URLs.
Subsequently, in mid-December 2024, the actors introduced ClickFix social engineering lures, a technique that convinces victims to paste malicious commands directly into Windows Run dialog boxes.
The final significant update arrived in late June 2025, when the threat actors implemented new persistence mechanisms in their initial payload stages.
The phishing emails themselves employ convincing templates centered around banking themes, particularly transfer receipts and payment confirmations.
Researchers identified compromised email accounts actively sending these phishing messages, suggesting the actors obtain access to legitimate organizational mailboxes before launching campaigns.
Email subjects include variations like “Transfer receipt follows” and “Payment receipt and documents follow,” prepended with timestamps and document numbers to enhance authenticity.
Multi-Stage Infection Architecture
The infection chain comprises multiple obfuscated Visual Basic script stages, each with distinct purposes and infrastructure components.
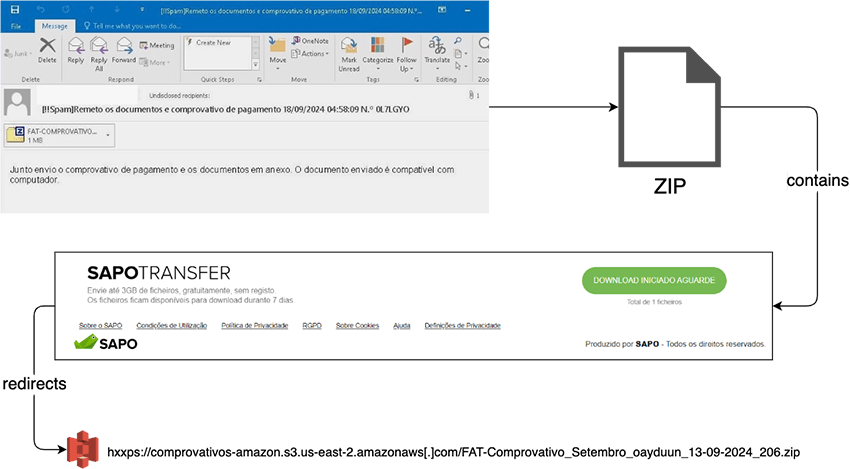

In late September 2024, the threat actors (TAs) started experimenting with using their own domains to host the second ZIP file instead of relying on third-party services like AWS S3 or WeTransfer.
The first stage, delivered through ZIP attachments containing deceptive HTML files, now includes persistence mechanisms by creating scheduled tasks that copy itself into the Windows Startup folder.
This stage’s primary function is fetching the second-stage payload while employing file bloating techniques that expand the 35KB script to 3-5MB through garbage variables and obfuscated strings.
The second stage downloads the final VBS component from redirected cloud storage buckets, while the third stage handles the actual payload delivery.
This final VBS stage removes evidence of previous infection stages, establishes persistence through CMD files in Startup folders, and communicates with command-and-control servers to receive the Lampion DLL payload.
Notably, the third stage removes all browser processes, including Edge, Firefox, Opera, Chrome, and Brave, likely to prevent victims from accessing banking websites outside the malware’s controlled environment.
Updated Lampion Stealer
The Lampion stealer itself has evolved into a single DLL file approximately 700MB in size, incorporating two encrypted ZIP files within its resource section. This represents a departure from previous variants that distributed multiple separate files.


The massive file size employs deliberate bloating to exceed file submission limits on automated analysis platforms, hindering detection.
The stealer communicates with hardcoded C2 infrastructure and sends telemetry including machine identifiers, operating system information, antivirus detection status, and hardware serial numbers.
VMProtect obfuscation further protects the malware’s code, enabling code virtualization, mutation, and anti-debugging capabilities that complicate reverse engineering efforts.
The threat actors maintain sophisticated, distributed infrastructure segmented by purpose, utilizing multiple cloud providers, web hosting services, and VPS hosts.
Critical components feature IP blacklisting capabilities that prevent security researchers from analyzing the infection chain while simultaneously serving as redirection points to legitimate cloud storage buckets, granting the actors precise control over payload delivery.
The campaign’s persistence, operational sophistication, and continuous tactical adaptation indicate a well-resourced threat group dedicated to maintaining successful operations against Portuguese-speaking targets while systematically improving evasion capabilities.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
