A new Lazarus campaign considered part of “Operation DreamJob” has been discovered targeting Linux users with malware for the first time.
This new targeting was discovered by ESET’s researchers, who say it also helps confirm with high confidence that Lazarus conducted the recent supply-chain attack on VoIP provider 3CX.
The attack was discovered in March 2023, compromising multiple companies that used the trojanized version of the 3CX client with information-stealing trojans.
Lazarus was already suspected of being responsible for the attack, while multiple cybersecurity companies agreed with high confidence that the threat actor who trojanized 3CX was of North Korean nexus.
Today, Mandiant published the results of their investigation into the 3CX breach, further linking the attack to North Korean threat actors.
Mandiant says 3CX’s developer environment was compromised after an employee installed trading software from Trading Technologies, whose installer had been trojanized in another North Korean supply chain attack.
Operation DreamJob on Linux
Lazarus’ Operation DreamJob, also known as Nukesped, is an ongoing operation targeting people who work in software or DeFi platforms with fake job offers on LinkedIn or other social media and communication platforms.
These social engineering attacks attempt to trick victims into downloading malicious files masqueraded as documents that contain details about the offered position. However, these documents instead drop malware on the victim’s computer.
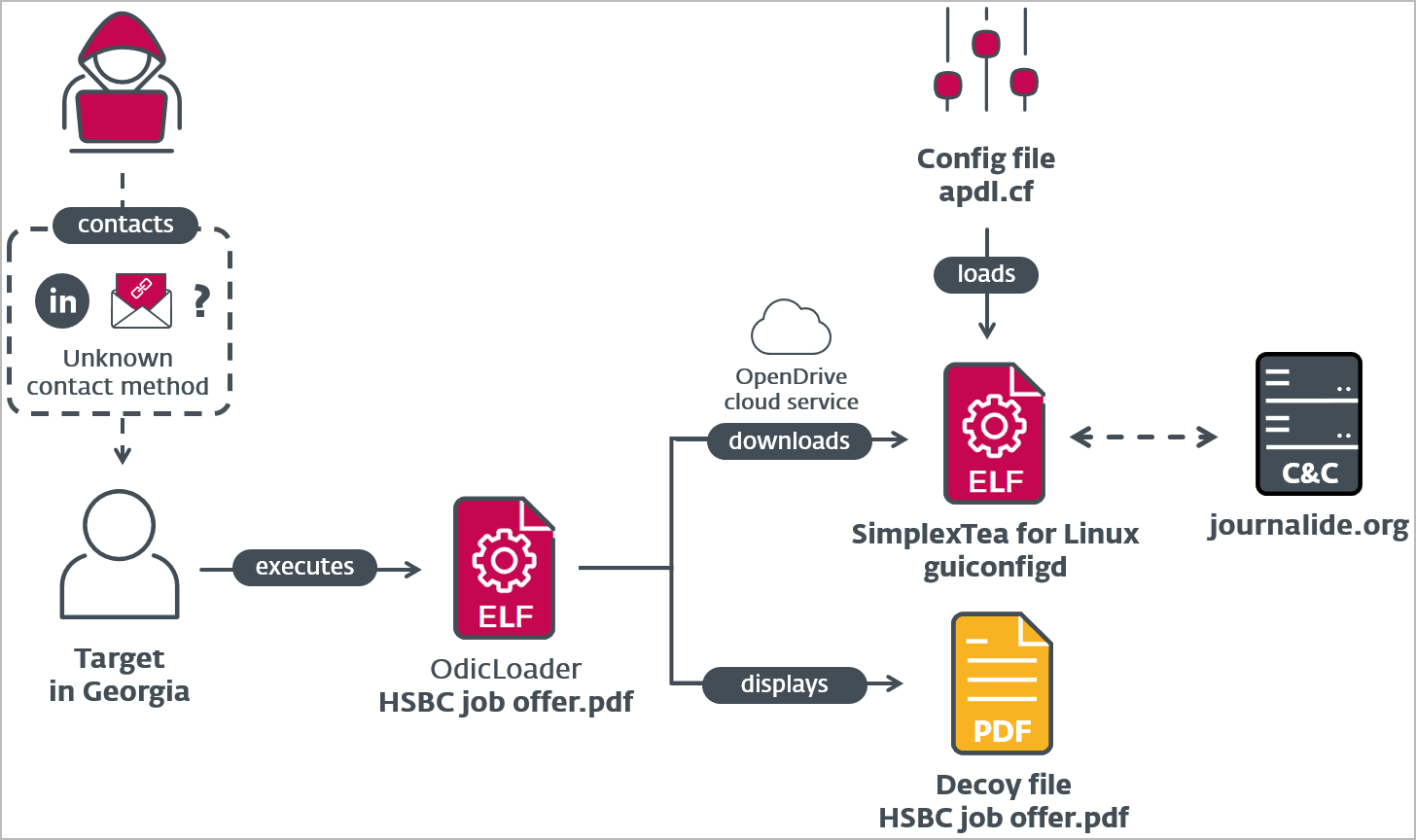
In the case discovered by ESET, Lazarus distributes a ZIP archive named “HSBC job offer.pdf.zip” through spearphishing or direct messages on LinkedIn.
Inside the archive hides a Go-written Linux binary that uses a Unicode character on its name to make it appear like a PDF.
“Interestingly, the file extension is not .pdf. This is because the apparent dot character in the filename is a leader dot represented by the U+2024 Unicode character,” explains ESET.
“The use of the leader dot in the filename was probably an attempt to trick the file manager into treating the file as an executable instead of a PDF.”
“This could cause the file to run when double-clicked instead of opening it with a PDF viewer.”
When the recipient double-clicks on the file to launch it, the malware, known as “OdicLoader,” displays a decoy PDF while simultaneously downloading a second-stage malware payload from a private repository hosted on the OpenDrive cloud service.
The second-stage payload is a C++ backdoor called “SimplexTea,” which is dropped at “~/.config/guiconfigd. SimplexTea.”
OdicLoader also modifies the user’s ~/.bash_profile to ensure that SimplexTea is launched with Bash and its output is muted whenever the user starts a new shell session.
The 3CX connection
Upon analysis of SimplexTea, ESET determined it is very similar in functionality, encryption techniques, and hardcoded infrastructure used with Lazarus’ Windows malware named “BadCall,” as well as the macOS variant called “SimpleSea.”
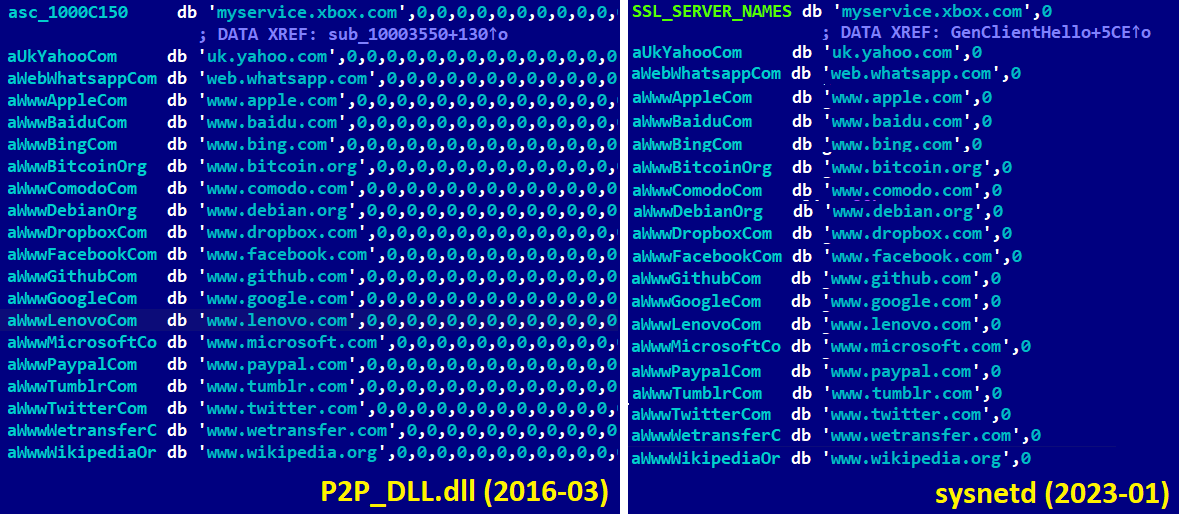
Also, ESET found an earlier variant of the SimplexTea malware on VirusTotal, named “sysnetd,” which is also similar to the mentioned backdoors but written in C.
That earlier variant loads its configuration from a file named /tmp/vgauthsvclog, which is used by the VMware Guest Authentication service. This suggests that the targeted system may be a Linux VMware virtual machine.
ESET analysts also found that the sysnetd backdoor uses an XOR key previously uncovered by the 3CX investigation to be used by the SimpleSea malware.
“Taking a look at the three 32-bit integers, 0xC2B45678, 0x90ABCDEF, and 0xFE268455 from Figure 5, which represent a key for a custom implementation of the A5/1 cipher, we realized that the same algorithm and the identical keys were used in Windows malware that dates back to the end of 2014 and was involved in one of the most notorious Lazarus cases: the cybersabotage of Sony Pictures Entertainment,” explained ESET.
The XOR key between SimplexTea and SimpleSea payloads differs; however, the configuration file uses the same name, “apdl.cf.”
Lazarus’ shift to Linux malware and the 3CX attack illustrates their ever-evolving tactics, now supporting all major operating systems, including Windows and macOS.
Similar Lazarus Operation DreamJob attacks have led to enormous success for the threat actors, allowing them to steal $620 million from Axie Infinity.
The FBI also confirmed Lazarus was behind the $100 million cryptocurrency theft from the Harmony Bridge.
Lazarus’ recent supply-chain attack on 3CX marks another high-profile success for the notorious cyber gang.




