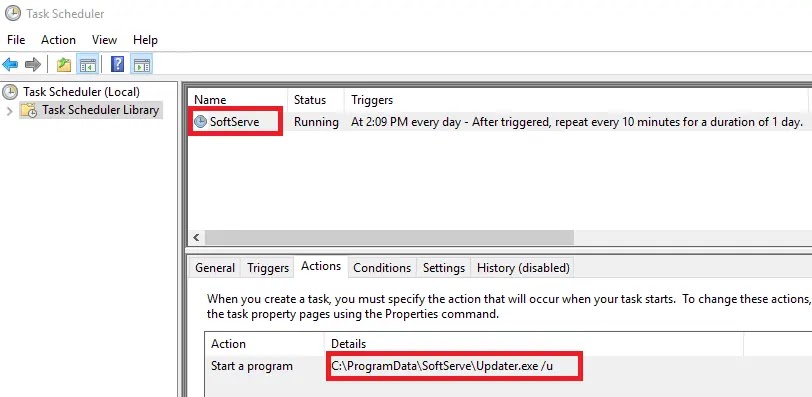
The AhnLab Security Emergency Response Center (ASEC) confirmed recent attacks on Windows IIS web servers by the nationally supported Lazarus group.
Typically, threat actors exploit vulnerable web server versions to install web shells or execute malicious commands during their scans.
Lazarus, a financially motivated hacking group, is believed to fund North Korea’s weapons development programs while also engaging in espionage operations.
Lazarus Targets IIS Servers
Organizations, regardless of their size, employ Windows IIS web servers to host various web content, including websites, applications, and services like Outlook on the Web from Microsoft Exchange.
Since the release of Windows NT, this has been one of the most flexible solutions on the market, supporting protocols such as:-
- HTTP
- HTTPS
- FTP
- FTPS
- SMTP
- NNTP
In the event of inadequate management or outdated configurations, servers have the potential to serve as vulnerable access points for hackers to infiltrate a network.
Symantec previously reported hackers using malware on IIS to execute commands undetected, while a separate report uncovered the hacking group ‘Cranfly’ using IIS web server logs for unknown malware control.
The ASD log indicates that Windows server systems are under attack, with malicious activities occurring through the w3wp.exe process of the IIS web server.
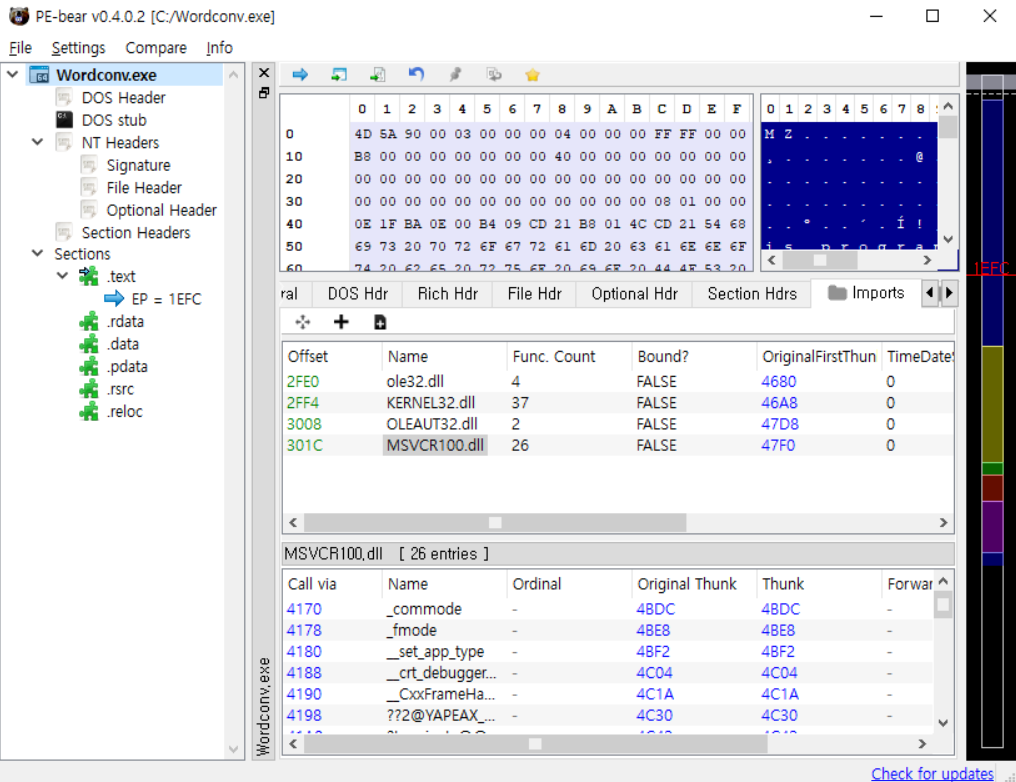
Lazarus exploits IIS servers through vulnerabilities or misconfigurations, leveraging the w3wp.exe process to create files, including a legitimate ‘Wordconv.exe,’ a malicious DLL (‘msvcr100.dll’), and an encoded file called ‘msvcr100.dat’ within the same folder.
After initiating ‘Wordconv.exe,’ the DLL’s malicious code decrypts the Salsa20-encoded executable from msvcr100.dat, executing it in memory to evade detection by antivirus tools.
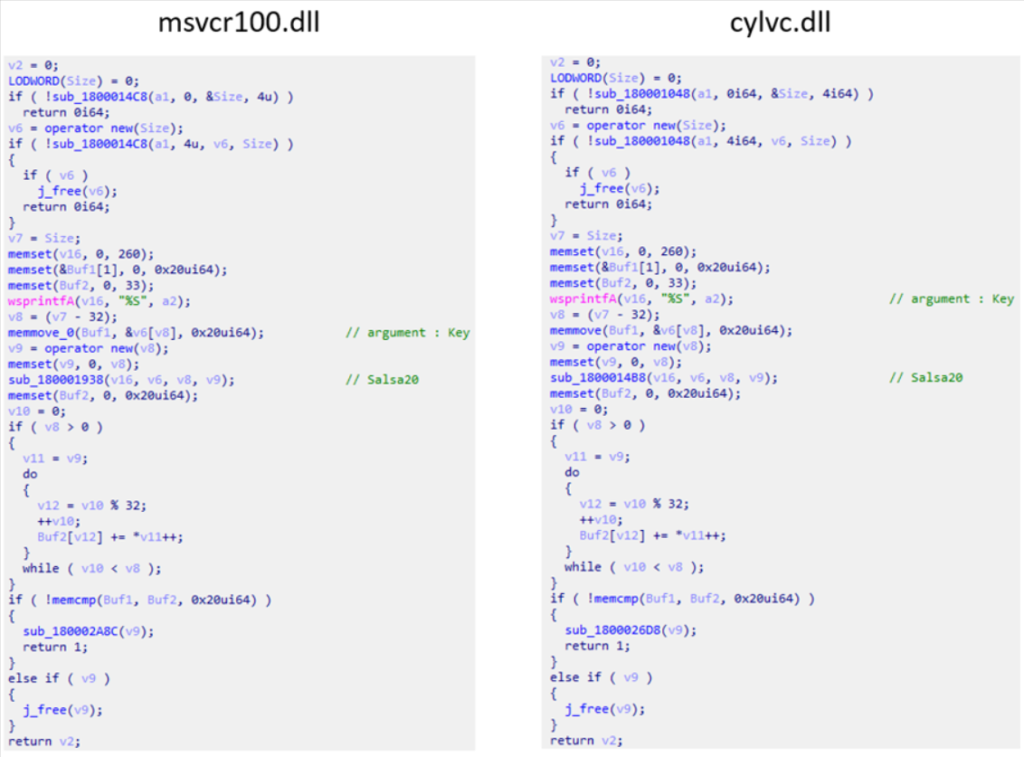
During the second phase, Lazarus exploits a Notepad++ plugin to generate a second malware (‘diagn.dll’), which then decodes a new payload using a fixed key and executes it in memory to avoid detection.
The LSASS dumping indicates potential credential theft activity, although the exact purpose of the payload remains unknown to ASEC.
After obtaining presumably stolen valid user credentials, the final phase of the Lazarus attack involved network reconnaissance and lateral movement through port 3389 (Remote Desktop).
However, ASEC has not detected any subsequent malicious actions following the attackers’ lateral spread within the network.
ASEC advises organizations to monitor for abnormal process execution due to Lazarus’ extensive use of DLL sideloading in their attacks.
Due to their active global attack campaigns, this highly dangerous group highlights the importance for corporate security managers to employ attack surface management, identifying vulnerable assets and prioritizing the application of the latest security patches whenever feasible.
To prevent the threat group from engaging in activities like information exfiltration and lateral movement, companies should proactively monitor abnormal process execution relationships, especially considering the threat group’s predominant use of the DLL side-loading technique during initial infiltrations, and take preemptive measures accordingly.
Common Security Challenges Facing CISOs? – Download Free CISO’s Guide