Hamas hacked into video streams from private security cameras in Israeli homes to gather intelligence before fighters descended on Israeli settlements near the Gaza strip on 7 October 2023, according to the Israel National Cyber Directorate (INCD).
For Gaby Portnoy, director general of the INCD, the hacking was no surprise: “But it went deeper than we thought. We saw that they collected very intimate intelligence from those cameras.”
Exploiting weak and default passwords, Hamas hackers succeeded in tapping into smart devices in Israeli homes and were able to change the displays on smart billboards on the roadside.
The hacking attacks may not have caused serious physical damage, but they had a significant psychological impact. “They were very easy attacks, but their influence was very big,” said Portnoy.
Israel has now passed a law that gives the government powers to turn-off vulnerable security cameras for the duration of the conflict. The country is also stepping up its efforts to educate people about the security risks of smart devices as it seeks to learn lessons from the cyber attacks that have since hit the country.
Portnoy has been in his current role for nearly two and a half years. A former Brigadier General in the Israel Defence Forces (IDF), his 31-year career includes head of operations in the Intelligence Corps and commander of unit 9900, a military unit that recruits people on the autism spectrum with special abilities to interpret and analyse satellite images and maps.
He describes running Israel’s National Cyber Directorate as a much “bigger challenge than I thought…like playing chess with six players”.
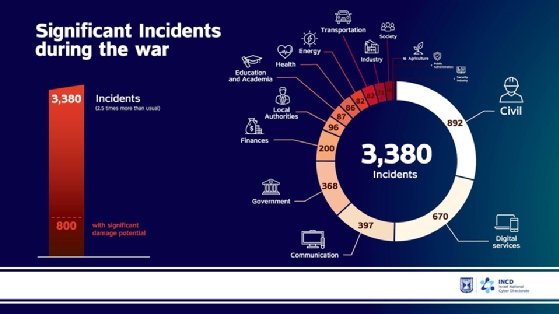
Since the start of the Gaza conflict, the volume of cyber attacks directed against Israel has tripled. Hacking groups have switched to targeting critical infrastructure, with most of Israel’s hospitals subject to hacking or ransomware attacks. The cost to the Israel economy is estimated at more than $3bn a year and rising.
Iran and the Iranian-backed group Hezbollah, operating from Lebanon, have been mounting “round the clock” hacking operations, said Portnoy, adding: “They worked together before the war. Now they are working very closely.”
Israel has tracked flights, indicating that the two groups are holding face-to-face meetings in Beirut. “They exchange targets, they exchange capabilities.”
Some of the hacking attempts have been more personal, with Portnoy saying the attacks have stolen the identities of people who were killed or kidnapped by Hamas, attempted to access their bank accounts, as well as access WhatsApp groups of the families affected.
“The Iranians are giving suicide UAVs to Russia. And we are very concerned that Russia will pass on cyber attack capabilities to Iran”
Gaby Portnoy, INCD
Israel is concerned that Russia’s close ties with Iran could lead to Russia supplying the Islamic Republic with offensive cyber capabilities. “The Iranians are giving suicide UAVs to Russia. And we are very concerned that Russia will pass on cyber attack capabilities to Iran,” said Portnoy.
Last month, he called for countries to work together in a “joint front” to tackle Iranian state-backed hacking. Iranian-backed hacking groups have attacked the UK, Germany and Austria, Saudi Arabia, Oman, Canada, and the UAE, among others.
“This makes Iran’s aggression a regional and international one, not only an Israeli one,” added Portnoy.
Cyber-Dome
Part of Israel’s response is its construction of a Cyber-Dome to protect critical national infrastructure from cyber-attacks. Named after Israel’s Iron Dome air defence system, which has seen active service during the conflict against rockets from Gaza and drones and missiles launched by Iran.
First announced in 2022, Cyber-Dome sets out to reduce the impact of large scale cyber attacks by using artificial intelligence (AI) and big data to enable the real-time detection and mitigation of threats.
Among the big tech companies involved in Cyber-Dome, Google is providing its Cybershield system to monitor cyber incidents. It is currently protecting 32 organisations in six sectors of the economy.
The INCD is working with The Cyber Security Council in the United Arab Emirates and Microsoft Israel to build a threat intelligence system to protect against Ransomware. Known as Crystal Ball, the project has 55 member countries.
Palantir is providing AI capabilities to Cyber-Dome, and Amazon is supplying secure cloud infrastructure and self-service protection services to small and medium companies.
Supply chain and intelligence sharing
Protecting supply chains is a priority for the National Cyber Directorate. Cyber attacks frequently target managed service providers (MSPs) that provide IT services to multiple organisations and companies in Israel.
“They are becoming more accurate,” Portnoy said. “They know more about Israel sometimes than we know about Israel.”
The IDF, for example, operates inside a closed network, but there have been attempts to attack the IDF through its suppliers. “We are as weak as the weakest link in our supply chain,” said Portnoy.
Portnoy describes the “secret sauce” of cyber defence operations as the willingness of intelligence agencies and other government departments to collaborate rather than to compete.
Rather than engage in turf-wars, Israel’s intelligence agencies, Mossad, Shin Bet and the IDF’s signals intelligence unit 8200 – roughly the equivalent of GCHQ – meet in person to share and discuss intelligence on threats to the country.
“We are sitting in the same round table, all the intel is in the middle of the table, and we are using it for protecting Israel. We are now sitting 24/7 physically together, and I think it gives results,” said Portnoy.
Israel claims to have stopped almost all of the serious cyber attacks launched against the country during the Gaza conflict.
Cyber terrorism and influence attacks
The biggest threat, though, comes not from cyber attacks, but the spread of disinformation and deep fakes, says Portnoy.
“They put videos on social media everywhere of the brutal terror attack,” he says. “We call it cyber terrorism. It is disinformation, it’s pictures and videos.”
Since the start of the war, Israel has made 48,000 requests to remove content from social media companies – of which, 86% have been accepted. The take-down system is voluntary, although Israel is considering whether to introduce regulations, perhaps along the lines of the UK’s Online Safety Act.
The Ministry of Justice takes the lead, but deciding what should be removed is not straight forward. For example, disinformation put out by Russia could be echoed by a political party within Israel. So, separating attempts at external influence campaigns by nation states from internal political campaigns is not easy.
“We don’t want to be the truth police,” said Portnoy.
Israel has also realised through the conflict that it needs to build state-like relationships with technology companies. Amazon, Microsoft and Google, for example, can choose sides like a nation state, said Portnoy.
“We need to deal with [tech companies] like nation states. Since last year, we try to build strategic relationships with those giants,” he said. “The better we talk with these big giants, the more difficult it will be for our enemies to put their infrastructure there.”
Portnoy argued that the conflict has shown the need for more international and global efforts to secure cyber space – a concept he refers to as “working together 2.0”. Israel has scrutiny agreements with 90 countries, but more important than number of countries is how closely they talk.
“There are more than 20 countries that we have a very close relationship [with for] sharing information, [with] almost every day a connection,” said Portnoy.
But he believes there is a need for countries to go further by building international defensive shields against cyber attacks, adding: “Imagine a world where cyber attacks are detected and blocked by international-level ecosystems and platforms.”




