LetMeSpy, a phone monitoring app, was breached, resulting in unauthorized access to website users’ data. Hacker has taken control of the messages, call history, and locations captured by the app.
The App is also called ‘stalkerware’ or ‘spouseware’, since these kinds of phone tracking applications are frequently set up by someone, such as partners or spouses. It is an Android-compatible mobile application.
.png
)
Calls, SMS, and GPS positions of the phone on which it is installed are all tracked while continuing to be “invisible to the user.”
The firm presents itself as a tool for employee or parental monitoring, but it doesn’t take much imagination to see that it may also be used for abuse.
“As a result of the attack, the criminals gained access to e-mail addresses, telephone numbers, and the content of messages collected on accounts,” according to a notice on the LetMeSpy login page.
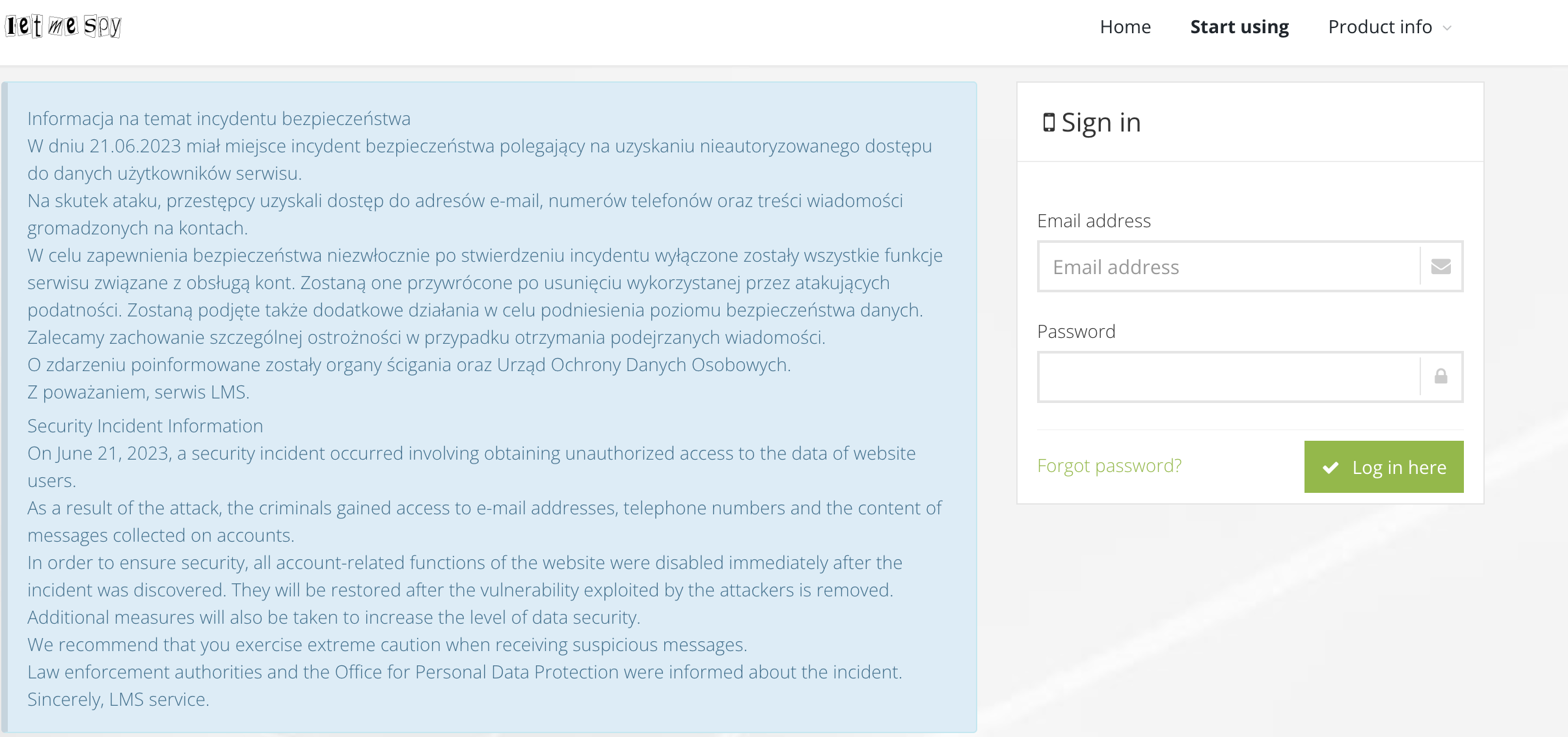
Niebezpiecznik, a Polish security research blog, was the first to reveal the incident. When the spyware creator approached for comment, a hacker who claimed to have full access to the spyware company’s website responded.
Details of the LetMeSpy Phone Tracking App
LetMeSpy is developed and managed by a Polish developer named Rafal Lidwin, who is situated in Krakow, according to information in the stolen database.
It is simpler to locate and remove LetMeSpy. The application is called “LMS,” and it has a unique icon.
The identity and motivation of the LetMeSpy hack’s perpetrators are unknown. The hacker hinted that they had removed the LetMeSpy databases from the server.
Later reports say a duplicate of the compromised database turned up online.
According to the report shared with Cyber Security News, an estimated 13,000 Android devices were reportedly affected by claims of hackers having access to all LetMeSpy logged data.
Notably, on the LetMeSpy website in January, the spyware was used to track over 236,000 devices and gathered tens of millions of call records, text messages, and location data points.
The spyware software and a large portion of the site’s functionality appear to be malfunctioning.
After examining the network data of the LetMeSpy mobile app, which revealed that the software looked to be nonfunctional.
Victim Location Detected
More than 13,400 location data points for several thousand victims were also present in the database.
Most of the location data points are concentrated across areas of high population density, which suggests that most victims are concentrated in Western Africa, the United States, and India.
The data also included the spyware’s master database, which included details on 26,000 users of the software who downloaded it for free as well as the email addresses of users who paid for subscriptions.
These surveillance applications are notoriously unstable and renowned for basic security flaws because of their high degree of access to a person’s phone.
Over the years, several spyware apps have been hacked or leaked and exposed to private phone data obtained from unaware users.
Therefore, if it hasn’t already, turn on Google Play Protect, one of the greatest protections against harmful Android applications. This may be done under Google Play’s settings menu.
“AI-based email security measures Protect your business From Email Threats!” – Request a Free Demo.
