Cryptocurrency thieves have found a new way to turn trusted software packages for Linux on the Snap Store into crypto-stealing malware, Ubuntu contributor and former Canonical developer Alan Pope warned.
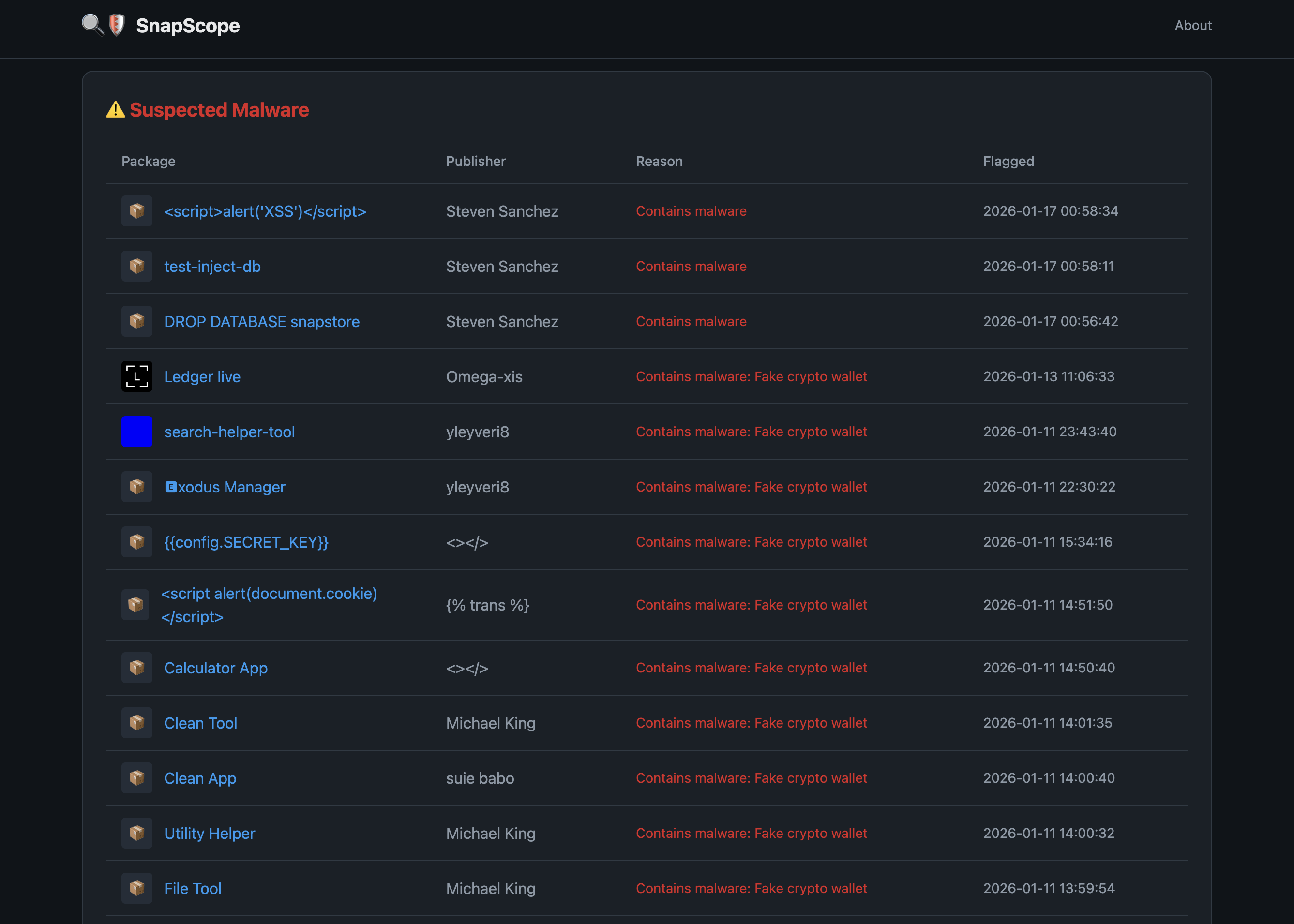
SnapScope web app identifies malicious snaps (Source: Alan Pope)
Instead of creating new accounts on this Canonical-run package repository, the attackers are taking over expired web domains and associated email servers tied to existing Snap Store publishers, and using that access to hijack their Snapcraft accounts and push malicious updates to previously benign packages.
Attackers’ newest approach
Like other popular software package repositories, the Snap Store has been targeted by malware peddlers for years.
Initially, the scammers simply created new Snap Store accounts and published authentic-looking but fake crypto wallet applications. After a while, they started evading text filters by using similar-looking characters from other alphabets for snap package names.
“More recently, they’ve adopted a bait-and-switch approach: Register an innocuous, unrelated snap name like lemon-throw, alpha-hub, or tenor-freeze, publish something harmless – often claiming to be a game, wait for approval, [and] push a second revision containing the fake crypto wallet app,” Pope explained.
But now they’ve also started taking over longstanding accounts by other developers, by searching for and registering expired domains.
“In at least two recent cases the attackers took over domains [storewise.tech and vagueentertainment.com] from genuine Snap publishers and used them to push wallet-stealing malware hidden in automatic app updates,” he found.
“The malicious snaps looked normal but were designed to harvest [crypto wallet] recovery phrases and send them to servers controlled by the attackers. By the time users realize something is wrong their cryptocurrency or other sensitive data is gone.”
Advice for users and developers
Canonical has removed the malicious snaps, but Pope says more thorough solutions are required to stem the flood of malicious packages.
“The domain takeover angle is particularly concerning because it undermines one of the few trust signals users had: publisher longevity. Canonical needs to address this, whether that’s monitoring for domain expiry on publisher accounts, requiring additional verification for accounts that have been dormant, implementing mandatory two-factor authentication, or something else entirely,” he opined.
He also noted that while he and other security professionals regularly report “bad” snaps, it occasionally takes days for Canonical to remove them from the Snap Store.
He advised users to be especially careful with cryptocurrency wallet snaps and consider obtaining such applications directly from official project sites rather than through any app store.
Pope also created SnapScope, a web app that users can leverage to check whether a snap is vulnerable, suspicious or malicious before they start using them.
Finally, he advised snap publishers to keep their domain registration current and enable two-factor authentication (2FA) for their email and Snapcraft accounts.
Hel Net Security has reached out to Canonical to ask whether they mean to implement additional safeguards around domain ownership and account recovery and additional checks to spot malicious updates to already published snaps. We’ll update this article when we have more information to share.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!

