Outpost24’s threat intelligence researchers have uncovered the operations of Lionishackers, a financially motivated cyber threat actor specializing in the exfiltration and illicit sale of corporate databases.
This group employs an opportunistic approach to target selection, with a notable preference for entities in Asian countries such as Thailand, Syria, and India.
While primarily driven by profit, Lionishackers exhibits secondary ideological motivations, potentially linked to professed Muslim affiliations, leading to limited involvement in hacktivist activities like coordinated Distributed Denial-of-Service (DDoS) attacks against Ukrainian and Israeli targets.
Unveiling the Threat Actor’s Modus Operandi
The actor maintains extensive collaborations, particularly with the pro-Palestine and pro-Russian group Hunt3r Kill3rs, where Lionishackers served as an administrator on their Telegram channel, facilitating database sales and joint DDoS campaigns.
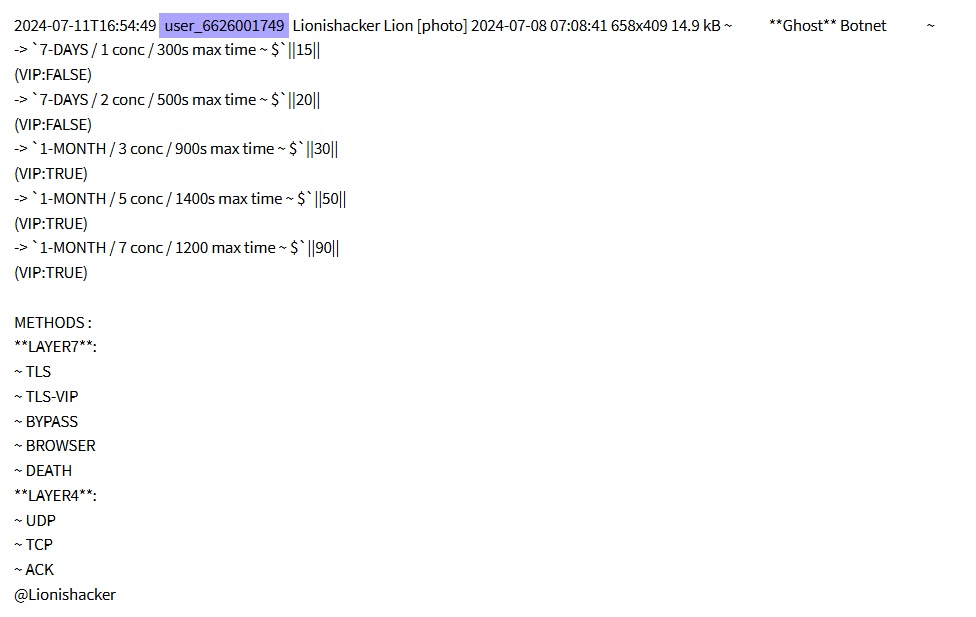
Beyond database exfiltration, the group diversifies its offerings, including penetration testing services, commercialization of the Ghost botnet for Layer 4 and Layer 7 attacks, and the short-lived Stressed Forums project launched in August 2024 amid disruptions to major underground platforms like Breach Forums.
Lionishackers likely leverage SQL injection vulnerabilities for initial access and data exfiltration, with observed references to automation tools like SQLMap in Telegram discussions.
This method enables the compromise of databases without deploying malware or encrypting data, simplifying attacks while maximizing profitability through direct sales.
The group targets a broad spectrum of sectors, including gambling sites as a stated preference, alongside government, pharmaceutical, telecommunications, education, and retail organizations.
Exploitation Techniques
Databases sold often include credentials from social media and email services, suggesting possible use of stolen valid credentials for unauthorized entry.
Commercialization occurs exclusively via Telegram for negotiations, with advertisements spread across multiple underground forums using transient aliases to evade attribution.
Since September 2024, Lionishackers has created numerous forum accounts, many of which have been banned due to scam accusations, though posts consistently include evidentiary images or links to validate compromises.
According to the report, Active participation in Telegram channels like AKULA and B F R e p o V 3 C h a t bolsters their reputation, enabling sales of leaked data for credential stuffing, fraud, corporate espionage, or social engineering exploits.
The real risk extends beyond immediate financial losses, encompassing reputational damage when leaks gain media traction, amplifying exposure to further malicious activities by buyers with access to sensitive Personal Identifiable Information (PII) or financial details.
The proliferation of such database exfiltration underscores broader cyber threats, where increasing data volumes and regulatory pressures create vulnerabilities that actors like Lionishackers exploit for high returns.
Monitoring these underground entities is crucial, as their seemingly low-sophistication operations can cascade into significant breaches, facilitating advanced persistent threats or ransomware precursors.
Indicators of Compromise (IOCs)
| Category | Indicator | Details |
|---|---|---|
| Forum Accounts | CypherX691 (Breached, BreachForums) | Registered various dates from September 2024 |
| Forum Accounts | ComplexData11 (BreachForums) | Registered various dates from September 2024 |
| Forum Accounts | Hacker82828, Sussyba17 (crackingx) | Registered September 3 and 23, 2024 |
| Forum Accounts | Sectornull101, Matadempo11 (Crackia) | Registered September 19 and 24, 2024 |
| Forum Accounts | Fen888 (Leakzone) | Registered April 2025 |
| Forum Accounts | datwkuvnj (Sinister) | Registered June 21, 2025 |
| Forum Accounts | Datcomon23, Sudsyba17, Datajsbdj, Datahellosui, PremiumDataOnly (Banned), Captainfen (Banned), OfficialSalesMan (Banned), foreman, Datasellonly (DarkForums) | Registered from September 22, 2024 to July 5, 2025 |
| Telegram Accounts (LION Alias) | t[.]me/Lionishacker (Unavailable), t[.]me/Lionishackers, t[.]me/Lionishackerrr | Various creation dates |
| Telegram Channels (LION Alias) | t[.]me/AboutTheLion (Jan 16), t[.]me/DataMarketZ (Apr 1), t[.]me/YourwaytoLion (Jul 5), t[.]me/DatabaseOnSell (Unavailable) | Various creation dates |
| Telegram Accounts (CAPTAIN FEN Alias) | t[.]me/CaptainFen | Various creation dates |
| Telegram Channels (CAPTAIN FEN Alias) | t[.]me/AboutCaptainFen (Mar 7), t[.]me/CaptainFenGroup (Unavailable) | Various creation dates |
| Associated Groups/Channels | Hunt3r Kill3rs Telegram Channel (Closed), AKULA, B F R e p o V 3 C h a t | Used for collaboration and sales |
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
