The notorious ransomware group LockBit has re-emerged on the dark web, signaling a swift comeback less than a week after a significant disruption by international law enforcement agencies.
This resurgence underscores the persistent and adaptable nature of cybercriminal organizations in the face of legal pressures and cybersecurity efforts.
Law Enforcement’s Ongoing Battle
Despite the recent arrest of three men linked to LockBit activities, the primary administrator known as LockBitSupp remains at large.
The U.S. State Department has offered rewards of up to $15 million for information leading to the identification or arrest of the group’s members, highlighting the high stakes in dismantling such networks.
You can analyze a malware file, network, module, and registry activity with the ANY.RUN malware sandbox, and the Threat Intelligence Lookup that will let you interact with the OS directly from the browser.
LockBit’s comeback is marked by listing more than two dozen servers containing victim data and using a new blog to communicate with their affiliates and victims.
Lockbit admin released a statement saying that penetration occurred through a PHP flaw, and now the PHP version has been updated.
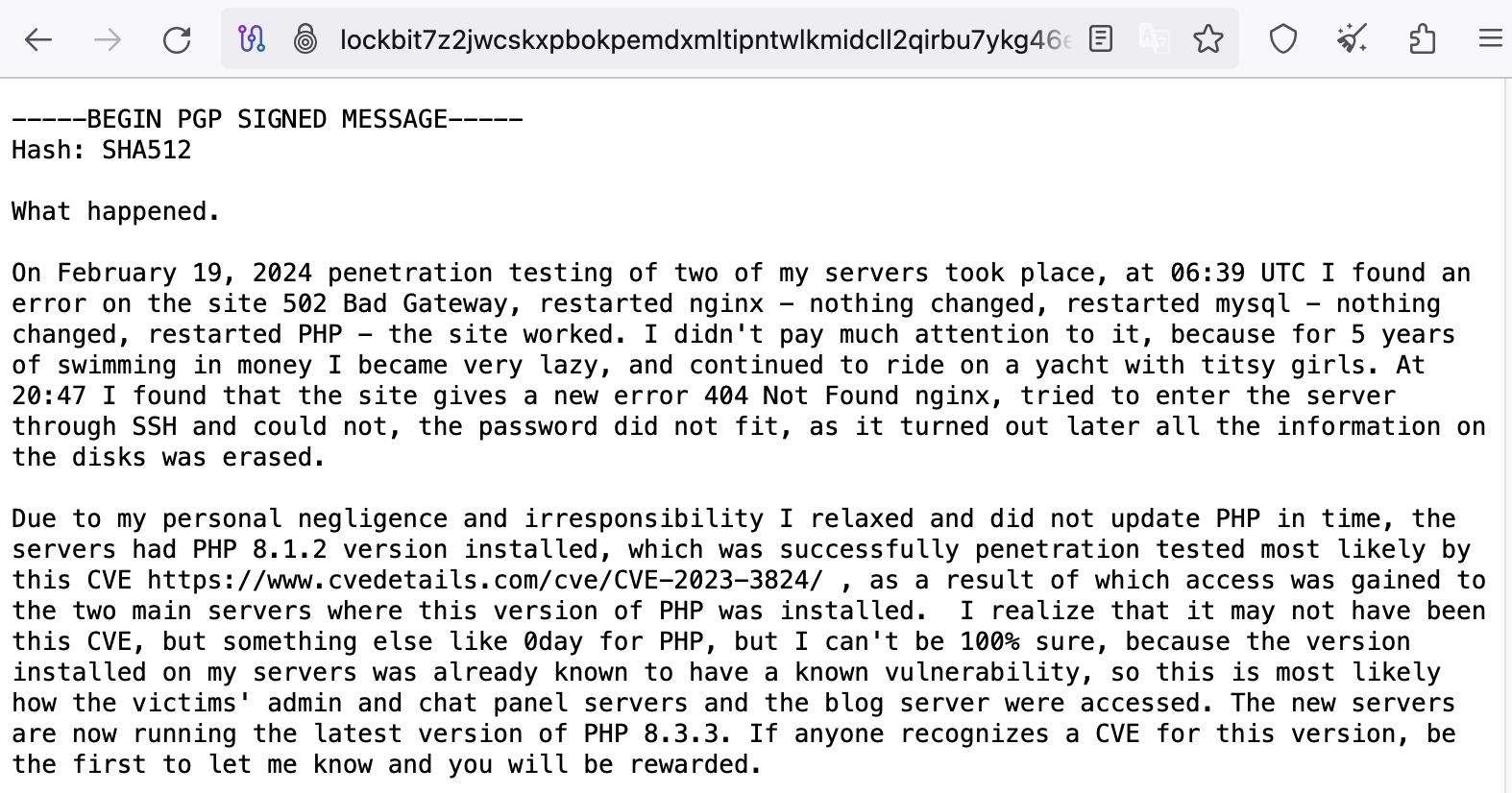
Lockbit has restored its servers (new Tor domains) and is planning on making a statement to the FBI regarding last week’s takedown.
The group has also been exploiting the CitrixBleed vulnerability, which affects Citrix load balancing and networking equipment, to gain access to networks and deploy ransomware.
This tactic demonstrates LockBit’s ability to adapt and exploit new vulnerabilities in enterprise systems.
The Challenge Of Cybersecurity
The LockBit incident highlights the complex obstacles that law enforcement and cybersecurity experts encounter in their endeavors.
The group’s ability to quickly restore operations from backup servers and establish a new dark web presence after their site’s takedown by the FBI and international partners shows the resilience of such criminal enterprises.
The LockBit group’s rapid recovery from a coordinated international crackdown raises concerns about the effectiveness of law enforcement actions against ransomware operations.
As per the reports published by WithSecure, it has been found that the Lockbit gang is accountable for around 21% of all the ransomware attacks that took place in the year 2023.
Today, Lockbit claims that they have compromised Prattindustries.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are extremely harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
