LockBit ransomware group has allegedly breached private equity firm Nautic.
Cybersecurity researchers shared details regarding the alleged Nautic cyberattack stating that the LockBit ransomware group had added the company to its victim list and threatened to post the company’s stolen data on April 26, 2023.
The official website of the private equity firm https://nautic.com/ was accessible at the time of writing.
Beyond Nautic Cyberattack: LockBit breaches, threats, and leaks
In the recent past, the LockBit ransomware group has targeted multiple sectors and posted the list of its victims.
On April 1, LockBit alleged leaked data stolen from the South Korean National Tax Service on its leak site.

On April 5, the LockBit ransomware group allegedly leaked the stolen data from two of Malaysia-based TF AMD.
TF AMD manufactures computer processing devices and offers test services for computing and communication devices among others.
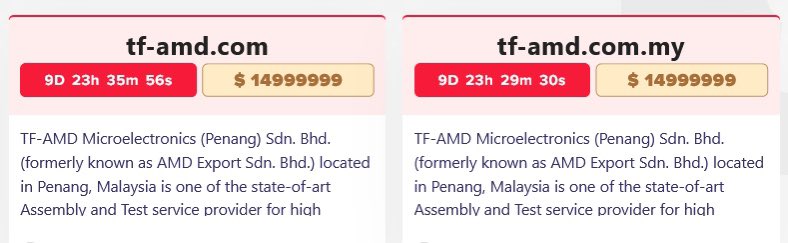
A ransom of $14,999,999 was demanded with a deadline of nearly 10 days of making the leak site post.
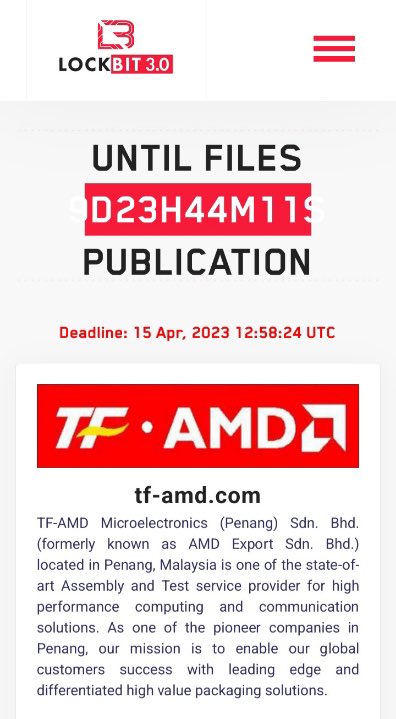
The LockBit ransomware group gave a deadline of 15 April midnight to the company to pay the ransom failing which the stolen data was threatened to be leaked. A ransom of $15 million was demanded by LockBit.
Several educational institutions have also been targeted by the LockBit ransomware group in the recent past including the Olympia Community Unified School District.
The Russia-based ransomware gang
Jon DiMaggio, chief security strategist at Analyst1 studied the ransomware group and said, “They are the most notorious ransomware group because of the sheer volume.”
DiMaggio further said that the success of LockBit can be attributed to its leader who is a “good businessman,” according to a Wired report.
Some common traits observed among the LockBit group members, Jon pointed out was that they constantly develop their point-and-click ransomware and seek user feedback which helps them make changes accordingly for better cyberattacks.
Changing colors of LockBit affiliates
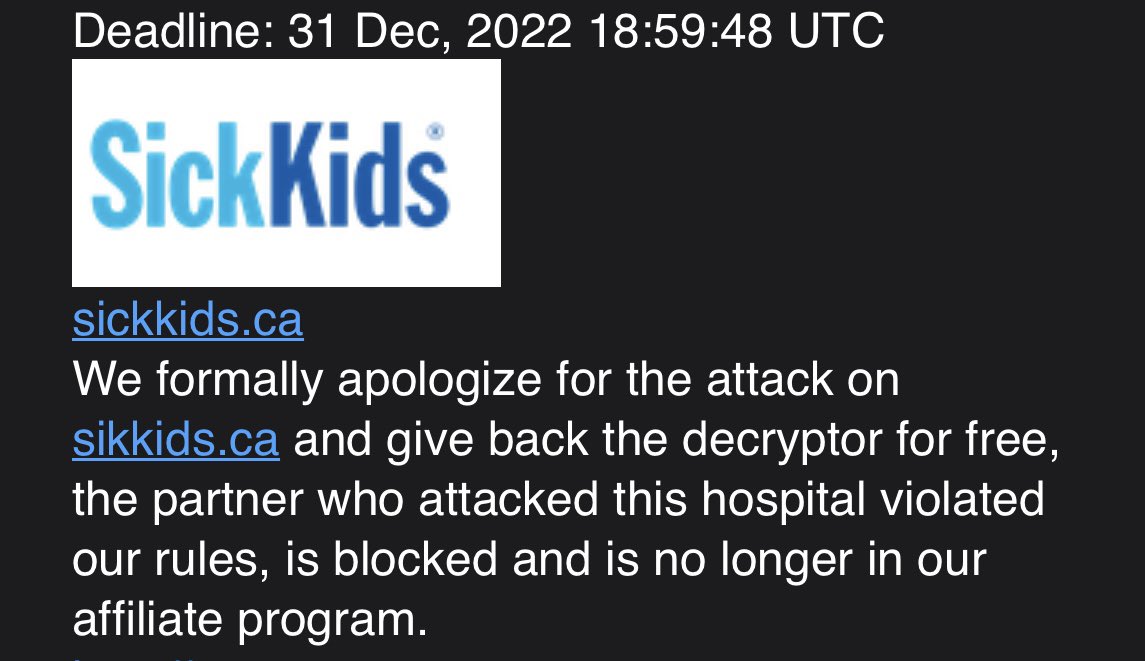
The group allegedly dismissed an affiliate who launched a cyberattack against a Canada-based children’s hospital that delayed services for patients. LockBit released an apology for going outside its policy of sparing healthcare from cyberattacks.
(Photo: Dominic Alvieri/ Twitter)
The SickKids hospital in Toronto was attacked last year by the group following which it gave decryptor for encrypted files for free.
Contrary to that, there were reports that pointed to LockBit launching cyberattacks on healthcare entities.
The group had several warnings issued against them by the United States federal authorities for applying triple-extortion threats on health sector organizations.