The LockBit ransomware group is making a comeback, with a new data leak site and seven new victims.
LockBit was once the most feared ransomware group, and it still vastly outnumbers other ransomware groups with more than 2,700 claimed victims over its six-year-history, but a series of international law enforcement actions that began in February 2024 severely disrupted the group, and it has struggled to mount a sustained comeback since.
LockBit 4.0, released in early 2025, failed to gain much traction and was never completely rolled out, and rivals like Qilin have done well attracting ransomware affiliates with favorable terms like profit sharing and enhanced features.
But LockBit 5.0, announced on the underground forum RAMP in September, may be helping the group gain some traction, as it has since launched a new dark web data leak site and claimed new victims, Cyble reported in a new note to clients.
LockBit ‘Fully Reactivated’
Despite a nearly two-year struggle to regain its footing, LockBit remains by far the most active ransomware group over its six-year history, its 2,757 victims more than double that of its nearest rivals, including Qilin, Akira, Play and CL0P (chart below from Cyble).
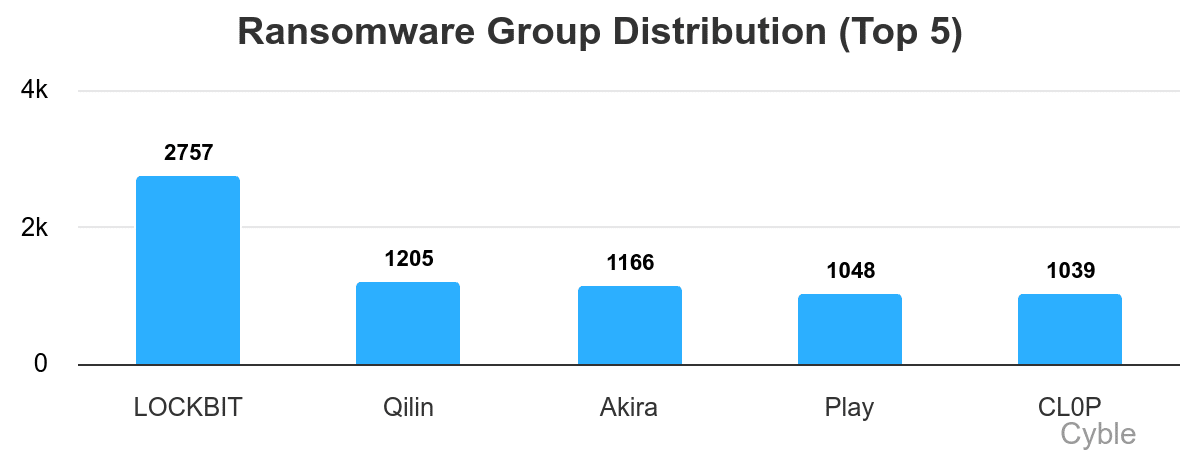
Despite its history and name, LockBit’s comeback route has been a steep one, as arrests, leaked source code and operational leaks have repeatedly hampered comeback attempts and given rivals an advantage.
But Cyble reported to clients today that LockBit has “fully reactivated its public ransomware operations.”
The new data leak site launched on November 5 and currently lists 23 victims, but Cyble reported that only seven of the victims are new and the rest had been previously claimed by the group.
The new LockBit 5.0 variant, internally codenamed “ChuongDong,” has been driving the group’s reemergence. The new ransomware variant includes a complete redevelopment of the ransomware panel and lockers, and the new malware is more modular and offers faster encryption and better evasion of security defenses. Obfuscation is a key feature of the new ransomware version, which targets Linux, Windows and VMware ESXi environments.
LockBit Victims, Sectors and Targeted Countries
One notable new victim claimed by LockBit is an Asian airline providing regional passenger transport and charter services. Another new listing is a major Caribbean real estate company.
Looking at the 42 victims claimed by LockBit thus far in 2025, what stands out are the sectors and countries targeted, which differ from other leading ransomware groups.
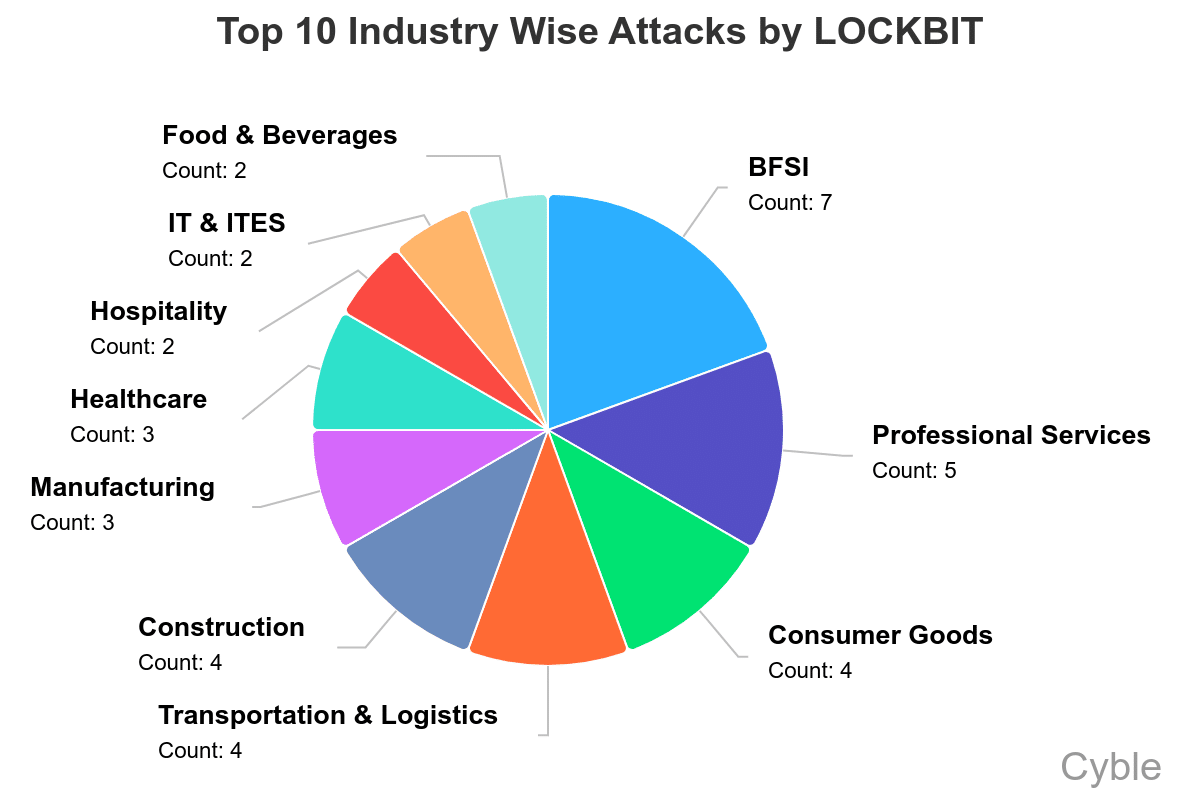
LockBit has had surprising success targeting financial services organizations. The group has claimed more victims in the Banking, Financial Services and Insurance (BFSI) sector in 2025 than in other industries (chart below). Overall, financial services isn’t among the top 10 sectors attacked by all ransomware groups, as the BFSI sector typically has stronger cybersecurity controls than other sectors.

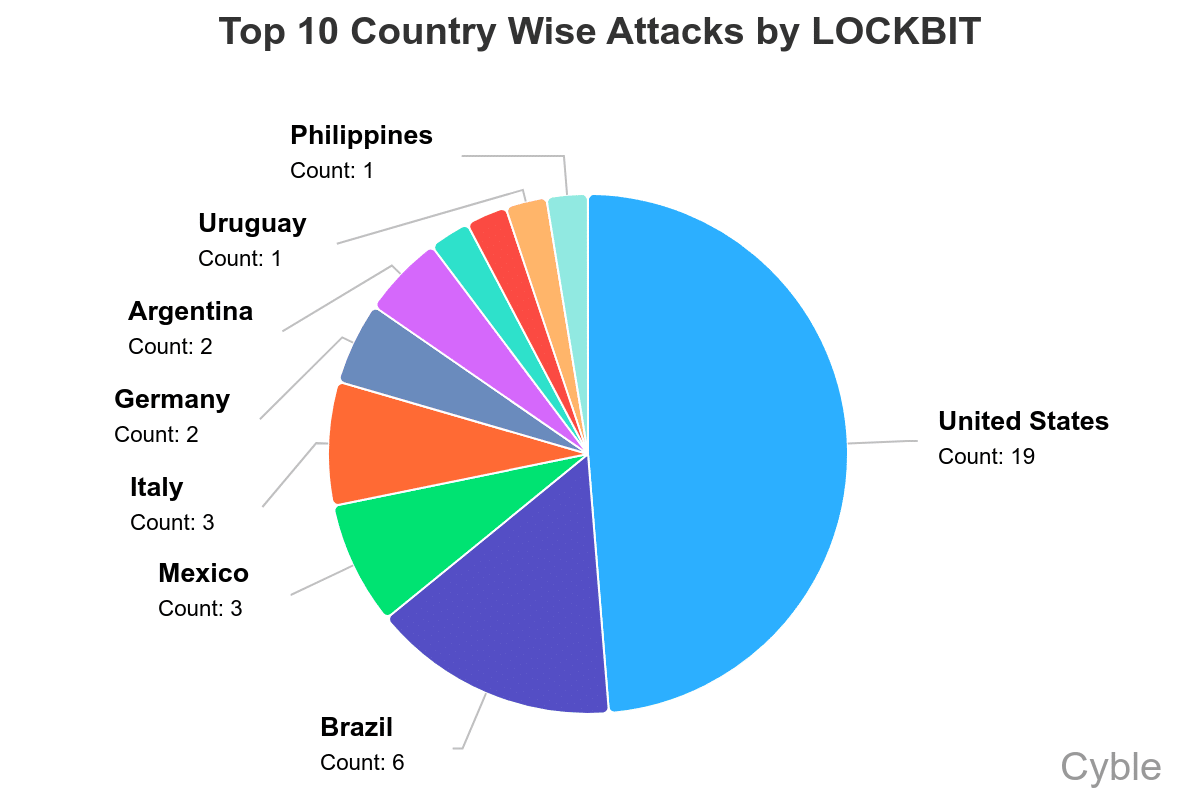
Also interesting is LockBit’s success targeting organizations in South America (chart below), which differs significantly from other ransomware groups, whose attacks are largely focused on the U.S., Canada and Europe.

It remains to be seen if LockBit can mount a sustained comeback this time, but the group has a uniquely interesting base to build on. Ransomware affiliates are opportunistic, however, and they tend to gravitate toward the ransomware groups that offer the best chance at profitability and success. LockBit’s comeback will depend on its ability to convince affiliates that it deserves to be back among the leaders.




