Morphisec Threat Labs uncovers sophisticated Lua malware targeting student gamers and educational institutions. Learn how these attacks work and how to stay protected.
The cybersecurity researchers at Morphisec Threat Labs have uncovered and thwarted multiple variants of Lua malware specifically targeting the educational sector. These attacks exploit the popularity of Lua-based gaming engine supplements, which are widely used by student gamers. Even more concerning, the malware campaigns were observed targeting unsuspecting users globally including across North America, South America, Europe, Asia, and Australia.
The malware strain was first reported in March 2024 (do not confuse Lua malware with the infamous Luabot DDoS malware identified in 2016). Over the past months, the delivery methods of Lua malware have changed to become simpler, possibly to evade detection mechanisms. Instead of using compiled Lua bytecode, which can easily raise suspicion, the malware is now frequently delivered through obfuscated Lua scripts.
Malicious ZIP Files
The malware is typically distributed in the form of an installer or a ZIP archive and often disguised as game cheats or other gaming-related tools, making it particularly lucrative to students who are searching for ways to enhance their gaming experience.
According to Morphisec Threat Labs’ detailed technical blog post shared with Hackread.com ahead of publishing on Tuesday, when a user downloads the infected file, typically from platforms like GitHub, they receive a ZIP archive containing four key components: Lua51.dll: A runtime interpreter for Lua, Compiler.exe: A lightweight loader, Obfuscated Lua Script: The malicious code and Launcher.bat: A batch file that executes the Lua script.
Upon execution, the batch file runs the Compiler.exe, which loads the Lua51.dll and interprets the obfuscated Lua script. This script then establishes communication with a Command and Control (C2) server, sending detailed information about the infected machine. The C2 server responds with tasks, which can be categorized into two types: Lua Loader Tasks: Actions such as maintaining persistence or hiding processes. Task Payloads: Instructions to download and configure new payloads.
Lua Malware and SEO Poisoning
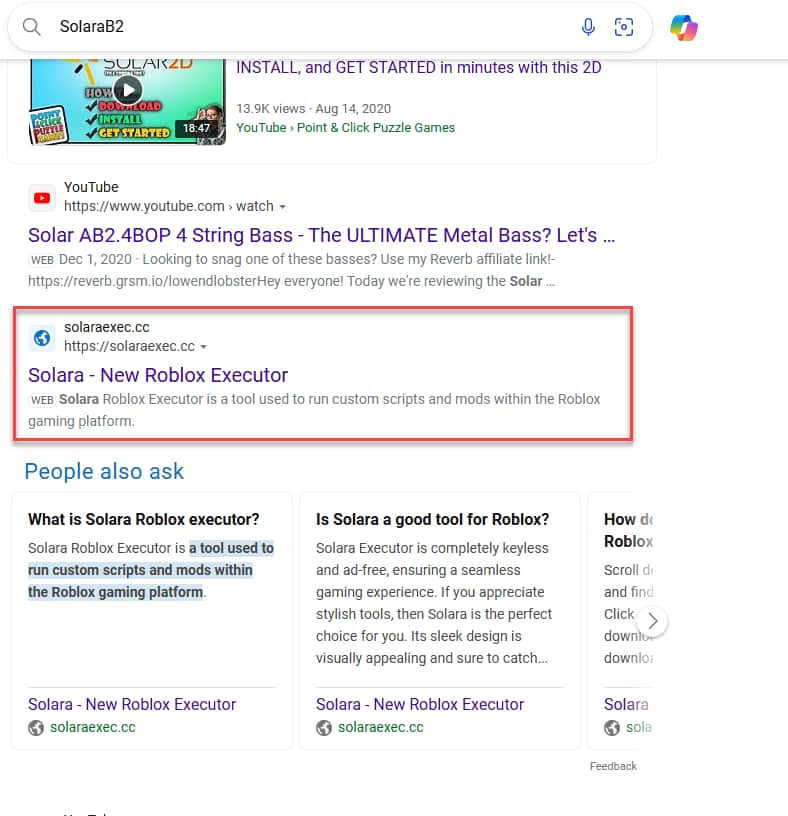
The delivery techniques used in these attacks include SEO poisoning, where search engine results are manipulated to lead users to malicious websites. For instance, advertisements for popular cheating script engines like Solara and Electron, often associated with Roblox, have been found to direct users to GitHub repositories hosting various Lua malware variants. These repositories frequently use github.com/user-attachments push requests to distribute the malware.
Additional InfoStealer Like Redline
The infection chain does not end with Lua malware infection. The malware ultimately leads to the deployment of infostealers, notably Redline Infostealers. For your information, infostealers like Redline, Vidar and Formbook are gaining prominence as the harvested credentials are sold on the dark web especially ChatGPT credentials, opening the door to more attacks in the future.
Watch Out Students and Gamers
Gamers, educational institutions, and students should be cautious of Lua and other malware threats by avoiding downloads from untrustworthy sources. Keeping security software up to date and informing users about the cybersecurity risks of downloading game cheats and unverified content can help reduce the chances of these attacks.
RELATED TOPICS
- Fake League of Legends Download Ads Drop Lumma Stealer
- Global malspam targets hotels, spreading Redline, Vidar stealers
- Fake Windows site dropped Redline malware as Windows 11 upgrade
- Fake CAPTCHA Verification Pages Spreading Lumma Stealer Malware
- Ransomware Hidden as a Game: Kransom’s Attack Via DLL Side-Loading
