The Lumma infostealer malware operation is gradually resuming activities following a massive law enforcement operation in May, which resulted in the seizure of 2,300 domains and parts of its infrastructure.
Although the Lumma malware-as-a-service (MaaS) platform suffered significant disruption from the law enforcement action, as confirmed by early June reports on infostealer activity, it didn’t shut down.
The operators immediately acknowledged the situation on XSS forums, but claimed that their central server had not been seized (although it had been remotely wiped), and restoration efforts were already underway.
Source: Trend Micro
Gradually, the MaaS built up again and regained trust within the cybercrime community, and is now facilitating infostealing operations on multiple platforms again.
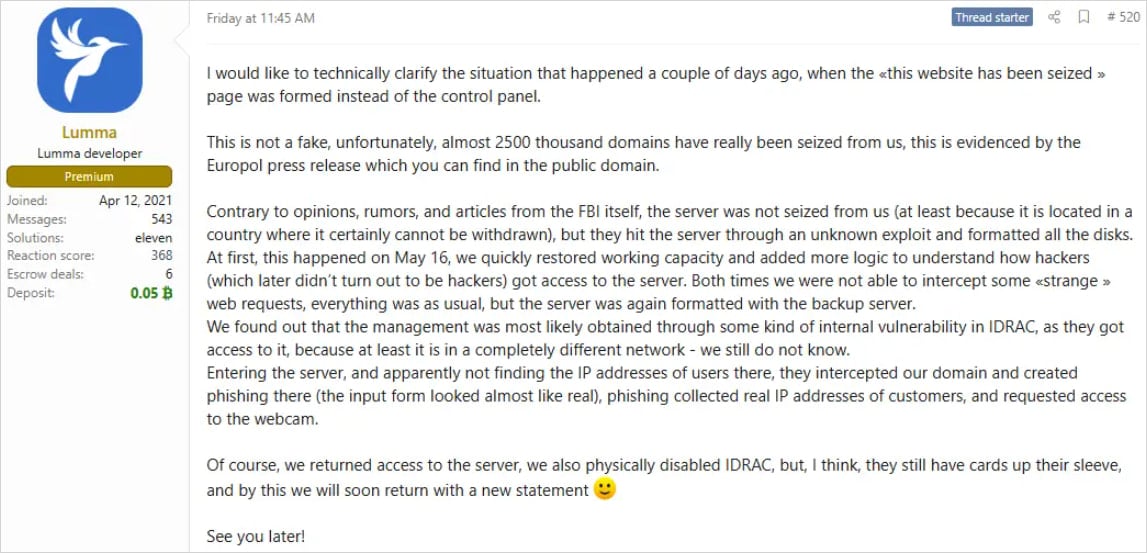
According to Trend Micro analysts, Lumma has almost returned to pre-takedown activity levels, with the cybersecurity firm’s telemetry indicating a rapid rebuilding of infrastructure.
“Following the law enforcement action against Lumma Stealer and its associated infrastructure, our team has observed clear signs of a resurgence in Lumma’s operations,” reads the Trend Micro report.
“Network telemetry indicates that Lumma’s infrastructure began ramping up again within weeks of the takedown.”
Source: Trend Micro
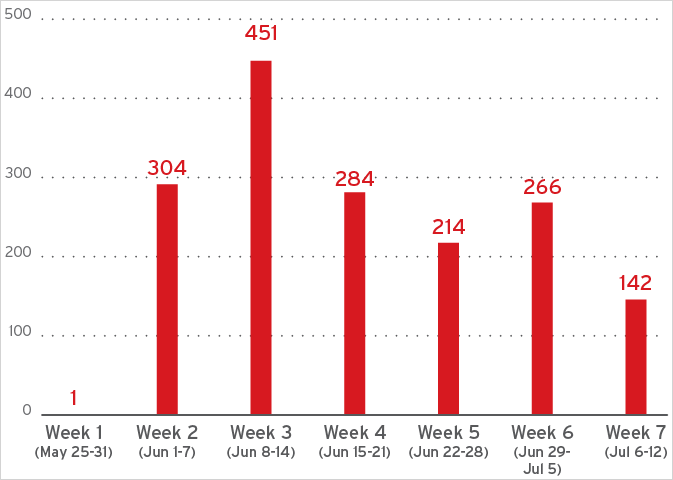
Trend Micro reports that Lumma still uses legitimate cloud infrastructure to mask malicious traffic, but has now shifted from Cloudflare to alternative providers, most notably the Russian-based Selectel, to avoid takedowns.
The researchers have highlighted four distribution channels that Lumma currently uses to achieve new infections, indicating a full-on return to multifaceted targeting.
- Fake cracks/keygens: Fake software cracks and keygens are promoted via malvertising and manipulated search results. Victims are directed to deceptive websites that fingerprint their system using Traffic Detection Systems (TDS) before serving the Lumma Downloader.
- ClickFix: Compromised websites display fake CAPTCHA pages that trick users into running PowerShell commands. These commands load Lumma directly into memory, helping it evade file-based detection mechanisms.
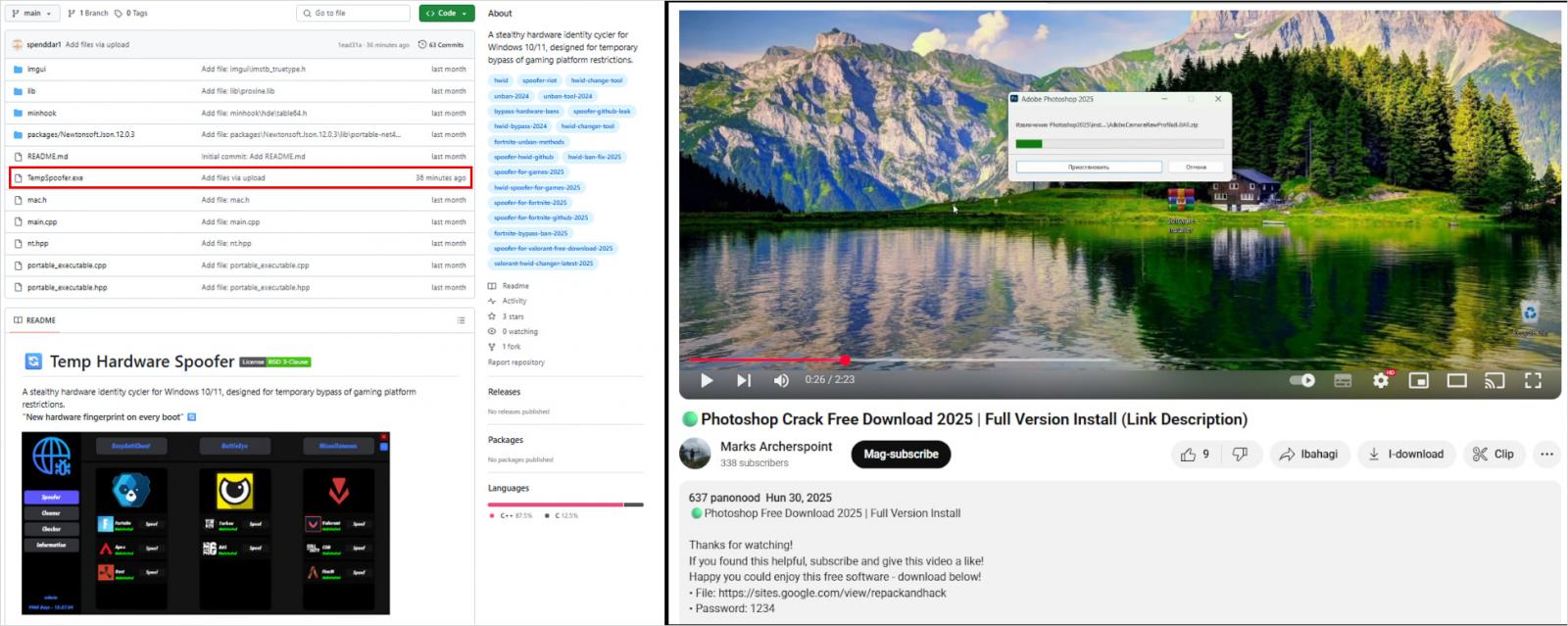
- GitHub: Attackers are actively creating GitHub repositories with AI-generated content advertising fake game cheats. These repos host Lumma payloads, like “TempSpoofer.exe,” either as executables or in ZIP files.
- YouTube/Facebook: Current Lumma distribution also involves YouTube videos and Facebook posts promoting cracked software. These links lead to external sites hosting Lumma malware, which sometimes abuses trusted services like sites.google.com to appear credible.
Source: Trend Micro
The re-emergence of Lumma as a significant threat demonstrates that law enforcement action, devoid of arrests or at least indictments, is ineffective in stopping these determined threat actors.
MaaS operations, such as Lumma, are incredibly profitable, and the leading operators behind them likely view law enforcement action as routine obstacles they merely have to navigate.

Contain emerging threats in real time – before they impact your business.
Learn how cloud detection and response (CDR) gives security teams the edge they need in this practical, no-nonsense guide.
