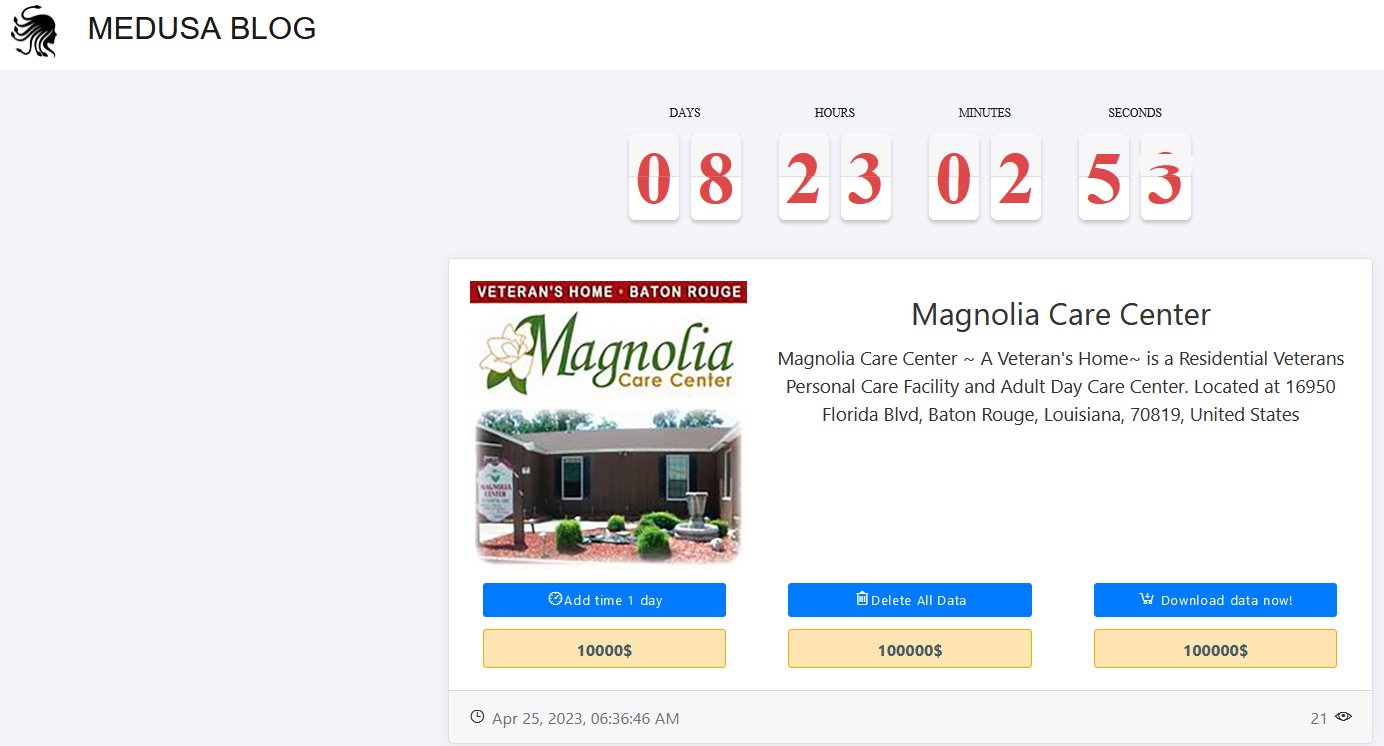
Veterans Home cyberattack: Medusa ransomware group posted Magnolia Care Center Veteran’s Home in Baton Rouge, United States. The Magnolia Care Center data breach post made by the Medusa group claimed that all the stolen data will be leaked after nearly 8 days and 23 hours of posting about it.
Cybersecurity analyst and researcher Dominic Alvieri confirmed the veterans home cyberattack, Magnolia Care Center data breach and shared details of the incident with The Cyber Express team.
Veterans Home Cyberattack: Magnolia Care Center Data Breach
The Cyber Express found medical documents of patients with their full names, health records, email addresses, residential addresses, and contact numbers among other data.

The leak site post of the Medusa ransomware group had a sum of $100,000 mentioned on it suggesting the amount of ransom demanded by the group for veterans home cyberattack. The post was made on April 25th.

The amount of ransom demanded to add a day to the ransom payment deadline was $10,000.
The amount demanded either deletion or downloading of the stolen data from the Magnolia Care Center data breach was $100,000 each.
(Photo: FalconFeedsio)
Other ransomware attacks by the Medusa ransomware group
Medusa is not among the most active ransomware group in the past few years. And yet is extorting money from Veteran’s home and other entities including India’s Gujarat Mineral Development Corporation.
The ransomware group made a demand of $500,000 for an attack launched on April 1, according to reports.
The cyberattack on the Open University of Cyprus was claimed by Medusa. The remote learning platform announced discovering a cyberattack impacting the systems going offline. A ransom of $100,000 was demanded by Medusa to the university.
Medusa ransomware group
The double extortion Medusa ransomware group targets Windows devices with spam emails. The group usually deletes all the shadow copies, maintains persistence, and disables recovery options on attacked systems.
It runs in Safe Mode before encrypting the files and steals financial and sensitive information from the systems. The ransom note of Medusa ransomware, not to be confused with the MedusaLocker ransomware which is different says, “!!!READ_ME_MEDUSA!!!.txt.”
It can terminate over 280 Windows services to hinder the encryption of files. The encryption of files by the Medusa ransomware is done using an AES-256 + RSA-2048 BCrypt library.
The group started a blog called Medusa Blog to publicize their cybercrimes in 2023. Medusa is often misunderstood with malware of similar names including Mirai-based botnet. They negotiate with the targeted entities using Tor website found at medusacegu2ufmc3kx2kkqicrlcxdettsjcenhjena6uannk5f4ffuyd.onion.