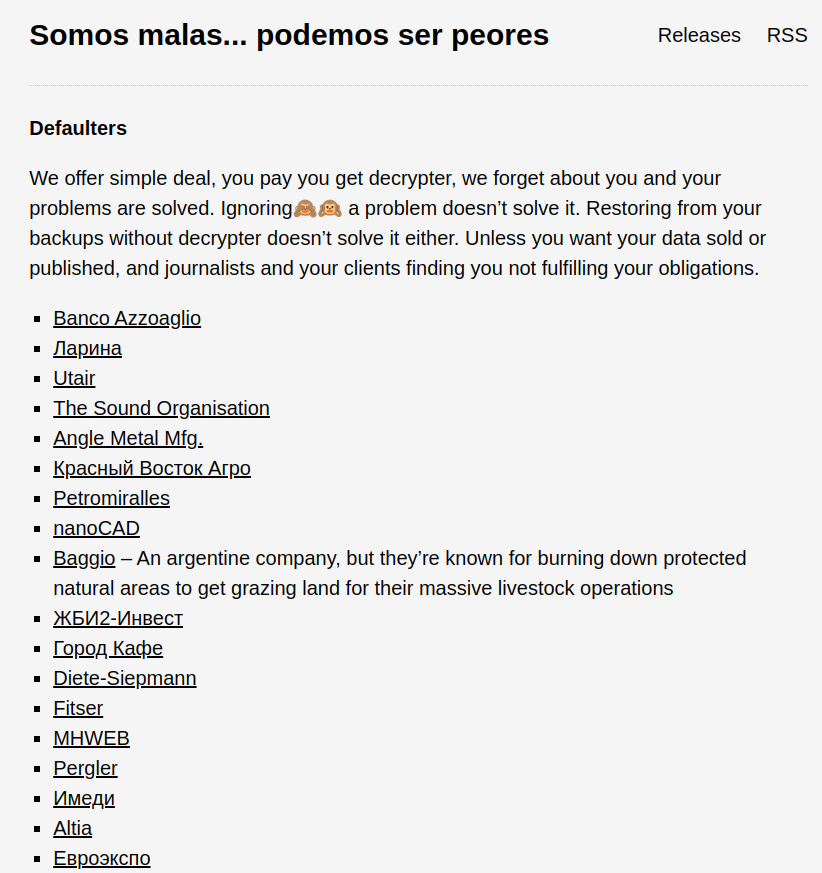
Days after being spotted exploiting Zimbra servers for ransomware attacks, MalasLocker ransomware gang has compiled a list of 169 victims whom they categorized as “Defaulters.” The group further left a message for the said “defaulters,” offering them a “simple deal.”
The names were posted on the group’s dark web channel, indicating they had attacked the listed victims.
Along with the list was also a message for the victims that read: “We offer a simple deal, you pay, you get decrypter, we forget about you, and your problems are solved,” read the message.
“Ignoring a problem doesn’t solve it. Restoring from your backups without decrypter doesn’t solve it either.”
“Unless you want your data sold or published, and journalists and your clients find you are not fulfilling your obligations,” the message concluded with a threat to leak the data if the demands are not met.
Moreover, the MalasLocker ransomware gang reportedly asks for ransom payments to be credited to charities, deviating from the standard ransomware procedures.
The threat actor has also been linked to a ransomware campaign called “MalasVault,” where it has been relentlessly targeting Zimbra servers since end of March 2023.
The MalasLocker ransomware gang is reportedly aiming to exfiltrate sensitive emails and encrypt files and has been distributing the data of three more companies, along with compromising the Zimbra configurations of 69 additional victims.
MalasLocker ransomware gang ransom demand techniques
The MalasLocker ransomware gang seems to have a unique modus operandi. Instead of going the traditional way of demanding a ransom, MalasLocker forces its victims to donate the amount to charities.
The group’s approach was first recorded in March 2023 when several victims found suspicious JSP files in specific folders of their Zimbra servers, including /opt/zimbra/jetty_base/webapps/zimbra/ and /opt/zimbra/jetty/webapps/zimbra/public. These files were identified under various names, such as info.jsp, loops.jsp, and heartbeat.jsp.
Upon analyzing the ransom note, users found that one of the text files, named README.txt, contained a unique demand from the threat actors: instead of a monetary payment, victims were requested to donate to a non-profit charity of their choice.
MalasLocker ransomware gang: Modus operandi
The encryption method employed by MalasLocker utilizes Age encryption, developed by Filippo Valsorda, a renowned cryptographer and Go security lead at Google.
Age encryption uses advanced algorithms such as X25519 (ECDH curve), ChaChar20-Poly1305, and HMAC-SHA256.
This encryption method is rarely utilized by ransomware operations, and it is worth mentioning that MalasLocker specifically targets non-Windows systems.
The ransom notes left by MalasLocker do not include a link to a data leak site, which is a common practice among many ransomware groups.
However, cybersecurity analyst Brett Callow from Emsisoft managed to uncover a link titled “Somos malas… podemos ser peores” (translation: “We are bad… we can be worse”).
The ransom note indicates that the threat actor could have access to more data than it possesses and can expose it if its charity demands are not met.
The Cyber Express team has reached out to the companies listed by the threat actor. However, at the time of writing, we had received any official response.
However, most of the websites of the alleged victims seem to be working fine and show no sign of a cyber attack, which means the threat could have access to the data but has not attacked their website’s operations yet.
The MalasLocker ransomware gang and their approach to cyber-attacks highlight the vast world of cybersecurity and threat actors.
With each threat actor with a philosophy of its own, businesses and companies need to strengthen their cyber skills and prepare themselves to battle ransomware groups and disruptions caused by ransomware attacks.
