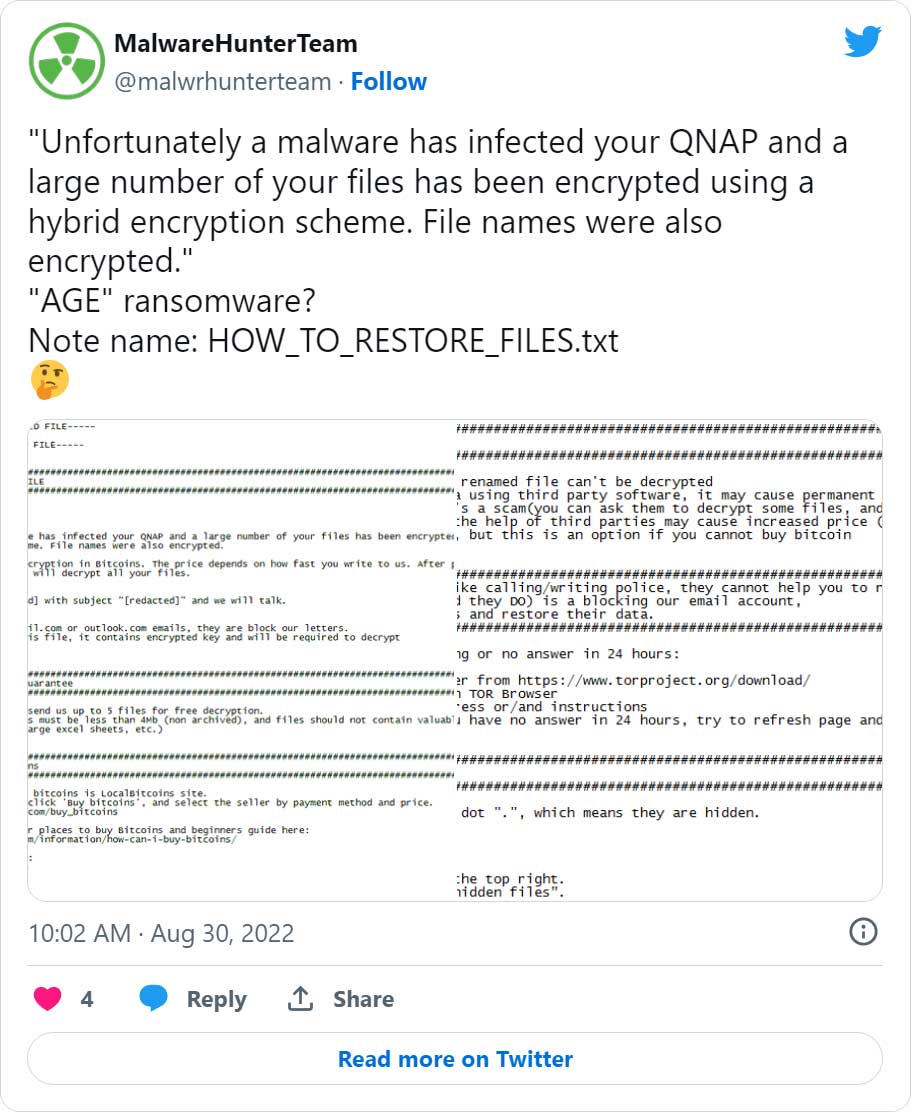
A new ransomware operation is hacking Zimbra servers to steal emails and encrypt files. However, instead of demanding a ransom payment, the threat actors claim to require a donation to charity to provide an encryptor and prevent data leaking.
The ransomware operation, dubbed MalasLocker by BleepingComputer, began encrypting Zimbra servers towards the end of March 2023, with victims reporting in both the BleepingComputer and Zimbra forums that their emails were encrypted.
Numerous victims in the Zimbra forums report finding suspicious JSP files uploaded to the /opt/zimbra/jetty_base/webapps/zimbra/ or /opt/zimbra/jetty/webapps/zimbra/public folders.
These files were found under different names, including info.jsp, noops.jsp, and heartbeat.jsp [VirusTotal]. Startup1_3.jsp [VirusTotal], which BleepingComputer found, is based on an open-source webshell.
Source: BleepingComputer.com
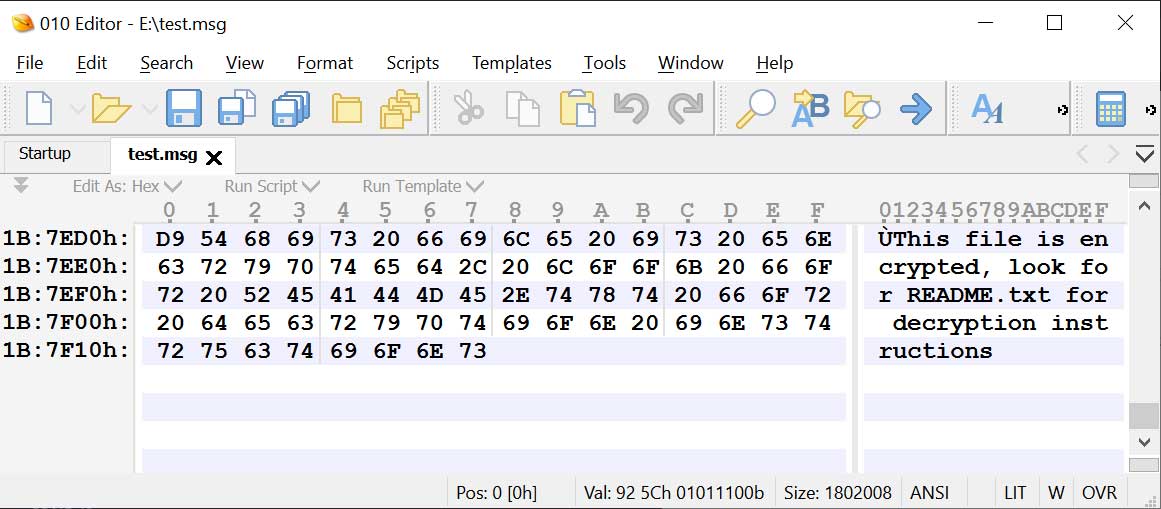
When encrypting email messages, no extra file extension is appended to the file’s name. However, security researcher MalwareHunterTeam told BleepingComputer that they append a “This file is encrypted, look for README.txt for decryption instructions” message at the end of every encrypted file.
Source: BleepingComputer
An unusual ransom demand
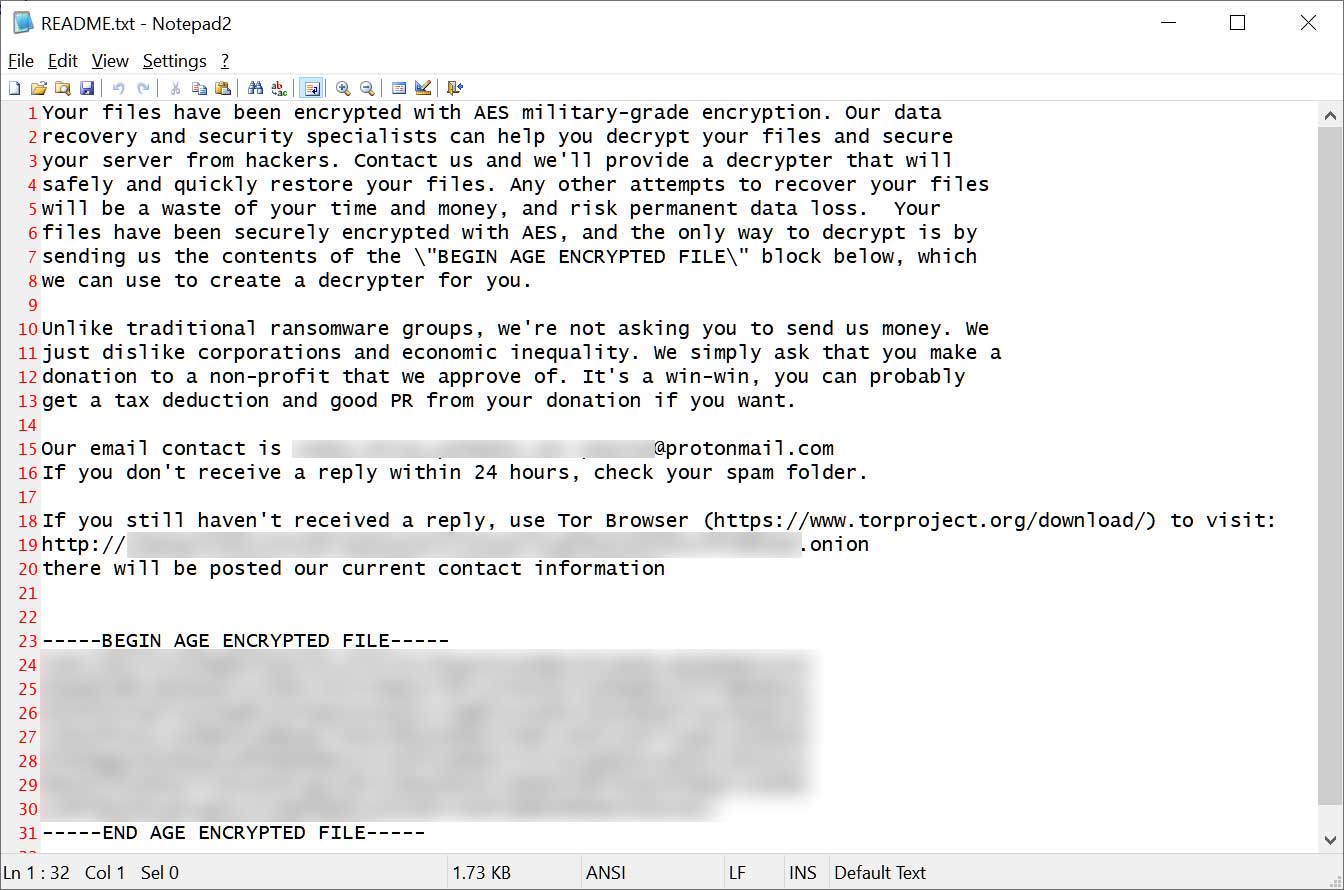
The encryptor will also create ransom notes named README.txt that come with an unusual ransom demand to receive a decryptor and prevent the leaking of stolen data: a donation to a non-profit charity that they “approve of.”
“Unlike traditional ransomware groups, we’re not asking you to send us money. We just dislike corporations and economic inequality,” reads the MalasLocker ransom note.
“We simply ask that you make a donation to a non-profit that we approve of. It’s a win-win, you can probably get a tax deduction and good PR from your donation if you want.”
Source: BleepingComputer
The ransom notes either contain an email address to contact the threat actors or a TOR URL that includes the most current email address for the group. The note also has a Base64 encoded text section at the bottom that is required to receive a decryptor, which we will go into more detail later in the article.
While the ransom notes do not contain a link to the ransomware gang’s data leak site, Emsisoft threat analyst Brett Callow found a link to their data leak site, having the title, “Somos malas… podemos ser peores,” translated to, “We are bad… we can be worse.”
The MalasLocker data leak site currently distributes the stolen data for three companies and the Zimbra configuration for 169 other victims.
The main page of the data leak site also contains a long emoji-filled message explaining what they stand for and the ransoms they require.
“We’re a new ransomware group that have been encrypting companies’ computers to ask they donate money to whoever they want,” reads the MalasLocker data leak site.
“We ask they make a donation to a nonprofit of their choice, and then save the email they get confirming the donation and send it to us so we can check the DKIM signature to make sure the email is real.”
|
|
|
This ransom demand is very unusual and, if honest, puts the operation more into the realm of hacktivism.
However, BleepingComputer has yet to determine if the threat actors are keeping their word when a victim donates money to a charity for a decryptor.
An uncommon Age encryption
BleepingComputer has not been able to find the encryptor for the MalasLocker operation. However, the Base64 encoded block in the ransom note decodes to an Age encryption tool header required to decrypt a victim’s private decryption key.
age-encryption.org/v1
-> X25519 GsrkJHxV7l4w2GPV56Ja/dtKGnqQFj/qUjnabYYqVWY
nkEmdfk4CojS5sTtDHR9OtzElaZ8B0+1iLtquHyh6Hg
-> .7PM/-grease {0DS )2D'y,c BA
l/tjxov1fa12V8Imj8SfQ27INLwEg+AC2lX3ou4N8HAjtmu9cPV6xLQ
--- 7bAeZFny0Xk7gqxscyeDGDbHjsCvAZ0aETUUhIsXnygThe Age encryption tool was developed by Filippo Valsorda, cryptographer and Go security lead at Google, and uses the X25519 (an ECDH curve), ChaChar20-Poly1305, and HMAC-SHA256 algorithms.
This is an uncommon encryption method, with only a few ransomware operations using it, and all of them not targeting Windows devices.
The first was AgeLocker, discovered in 2020 and the other was found by MalwareHunterTeam in August 2022, both targeting QNAP devices.
Furthermore, the ransom notes from the QNAP campaign and AgeLocker share similar language, further linking those two operations at least.
While this is a weak link at best, the targeting of non-Windows devices and using Age encryption by all of these ransomware operations could indicate that they are related.