A Russian-linked campaign delivers the StealC V2 information stealer malware through malicious Blender files uploaded to 3D model marketplaces like CGTrader.
Blender is a powerful open-source 3D creation suite that can execute Python scripts for automation, custom user interface panels, add-ons, rendering processes, rigging tools, and pipeline integration.
If the Auto Run feature is enabled, when a user opens a character rig, a Python script can automatically load the facial controls and custom UI panels with the required buttons and sliders.

Despite the potential for abuse, users often activate the Auto Run option for convenience.
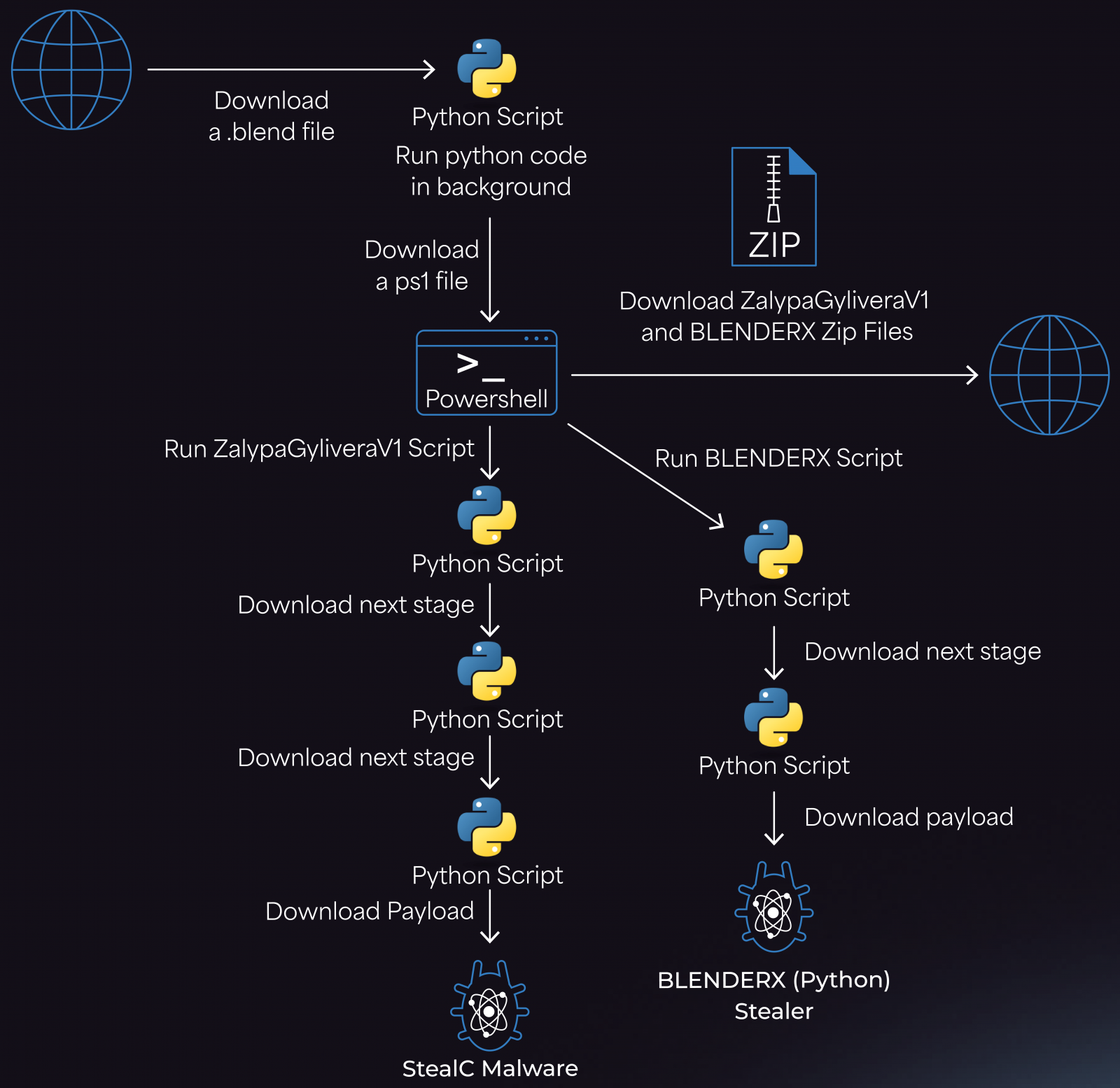
Researchers at cybersecurity company Morphisec observed attacks using malicious .blend files with embedded Python code that fetches a malware loader from a Cloudflare Workers domain.
Source: Morphisec
The loader then fetches a PowerShell script that retrieves two ZIP archives, ZalypaGyliveraV1 and BLENDERX, from attacker-controlled IPs.
The archives unpack into the %TEMP% folder and drop LNK files in the Startup directory for persistence. Next, they deploy two payloads, the StealC infostealer and an auxiliary Python stealer, likely used for redundancy.
Source: Morphisec
Morphisec researchers report that the StealC malware used in this campaign was the latest variant of the second major version of the malware that was analyzed by Zscaler researchers earlier this year.
The latest StealC has expanded its data-stealing capabilities and supports exfiltration from:
- 23+ browsers, with server-side credential decryption and compatibility with Chrome 132+
- 100+ cryptocurrency wallet browser extensions and 15+ cryptocurrency wallet apps
- Telegram, Discord, Tox, Pidgin, VPN clients (ProtonVPN, OpenVPN), and mail clients (Thunderbird)
- Updated UAC bypass mechanism
Despite the malware being documented since 2023, subsequent releases appear to remain elusive for anti-virus products. Morphisec comments that no security engine on VirusTotal detected the StealC variant they analyzed.
Given that 3D model marketplaces cannot scrutinize the code in user-submitted files, Blender users are advised to exercise caution when using files sourced from such platforms and should consider disabling the auto-execution of code.
You can do this from Blender > Edit > Preferences > uncheck the ‘Auto Run Python Scripts’ option.
3D assets should be treated like executable files, and users should only trust publishers with a proven record. For everything else, it is recommended to use sandboxed environments for testing.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
