A newly devised “polymorphic” attack allows malicious Chrome extensions to morph into browser extensions, including password managers, crypto wallets, and banking apps, to steal sensitive information.
The attack was devised by SquareX Labs, which warns of its practicality and feasibility on the latest version of Chrome. The researchers have responsibly disclosed the attack to Google.
Shape-shifting Chrome extensions
The attack begins with the submission of the malicious polymorphic extension on Chrome’s Web Store.
SquareX uses an AI marketing tool as an example, which offers the promised functionality, tricking victims into installing and pinning the extension on their browser.
To get a list of other installed extension, the malicious extension abuses the the ‘chrome.management’ API, which it was given access to during installation.
If the malicious extension doesn’t have this permission, SquareX says there’s a second, stealthier way to achieve the same, involving resource injection onto web pages the victim visits.
The malicious script attempts to load a specific file or URL unique to targetted extensions, and if it loads, it can be concluded that the extension is installed.
The list of installed extensions is sent back to an attacker-controlled server, and if a targeted one is found, the attackers command the malicious extension to morph into the targeted one.
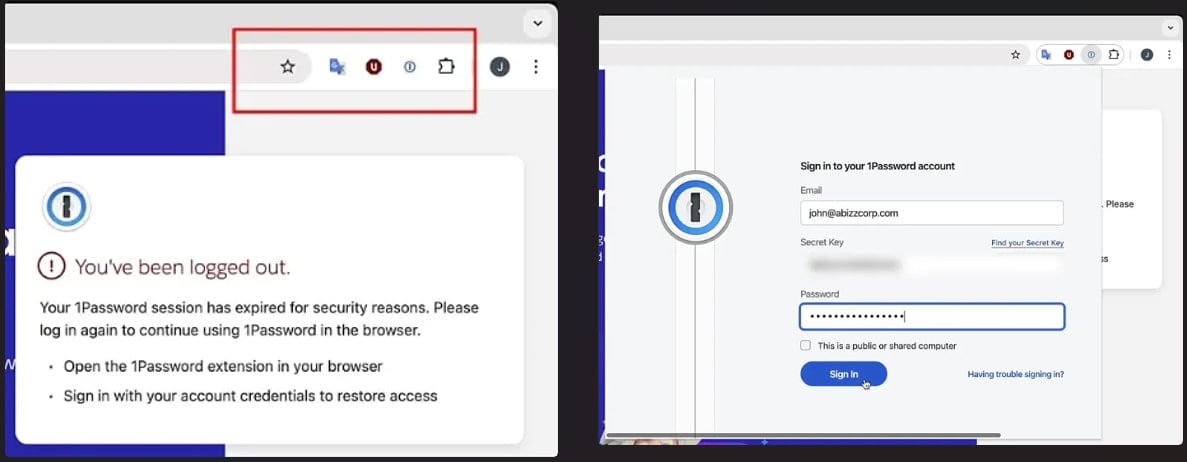
In SquareX’s demonstration, the attackers impersonate the 1Password password manager extension by first disabling the legitimate one using the ‘chrome.management’ API, or if the permissions aren’t available, user interface manipulation tactics to hide it from the user.
Simultaneously, the malicious extension switches its icon to mimic that of 1Password, changes its name accordingly, and displays a fake login popup that matches the appearance of the real one.
To force the user into entering their credentials, when attempting to log in to a site, a fake “Session Expired” prompt is served, making the victim think they were logged out.
This will prompt the user to log back into 1Password through a phishing form that sends inputted credentials back to the attackers.
Source: SquareX
Once the sensitive information is sent to the attackers, the malicious extension reverts to its original appearance, and the real extension is re-enabled, so everything appears normal again.
A demonstration of this attack can be seen below, where the malicious extension impersonates 1Password.
Mitigation measures
SquareX recommends that Google implement specific defenses against this attack, such as blocking abrupt extension icons and HTML changes on installed extensions or at least notifying users when this happens.
However, at the time of writing, there are no measures to prevent this kind of deceptive impersonation.
SquareX researchers also noted that Google wrongfully classifies the ‘chrome.management’ API as “medium risk,” and it is extensively accessed by popular extensions such as page stylers, ad blockers, and password managers.
BleepingComputer has contacted Google to request a comment on the topic, and we will update this post as soon as we hear back.
