A new phishing campaign targeting Amazon Web Services (AWS) logins is abusing Google ads to sneak phishing sites into Google Search to steal your login credentials.
The campaign was discovered by Sentinel Labs, whose analysts observed the malicious search results on January 30, 2023. The bad ads ranked second when searching for “aws,” right behind Amazon’s own promoted search result.
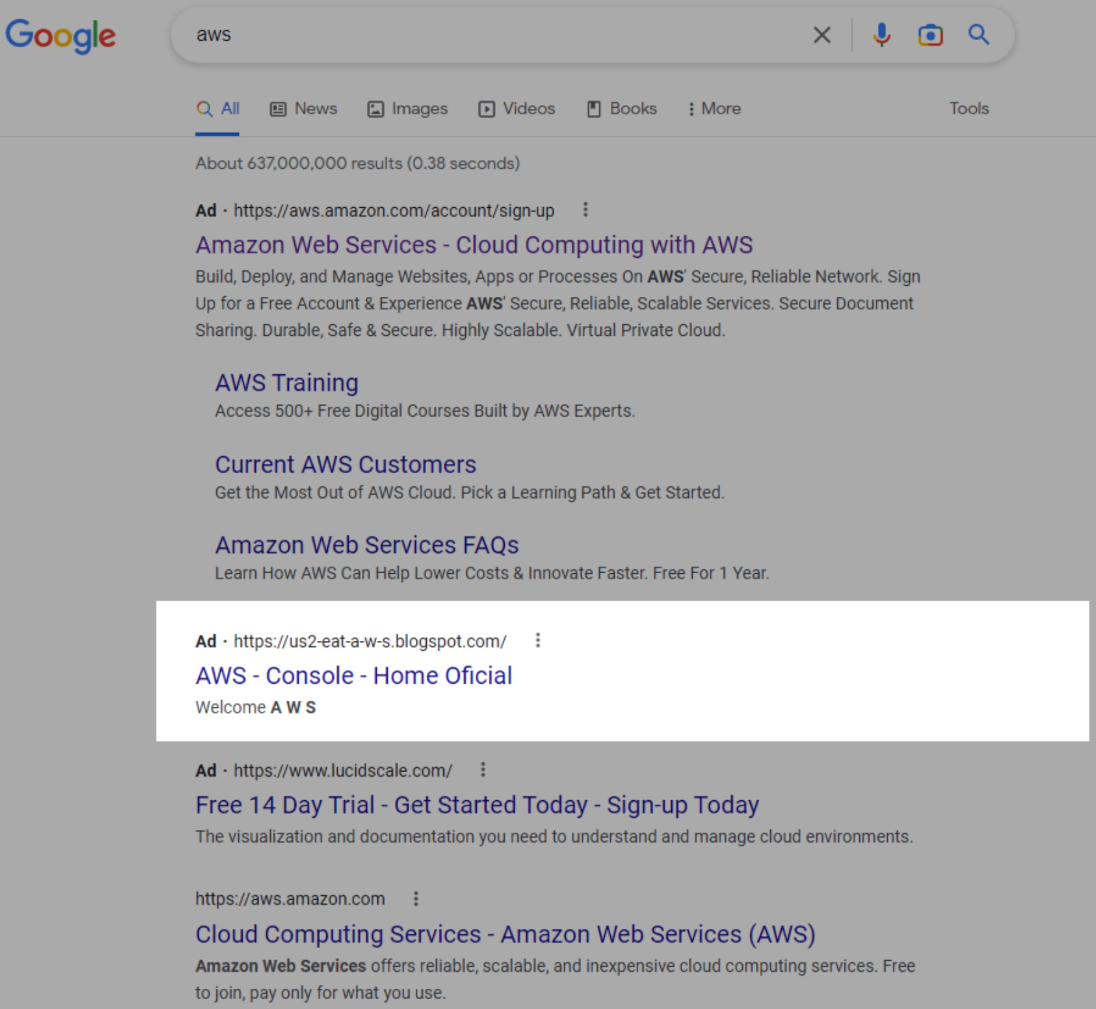
Initially, the threat actors linked the ad directly to the phishing page. However, at a later phase, they added a redirection step, likely to evade detection by Google’s ad fraud detection systems.
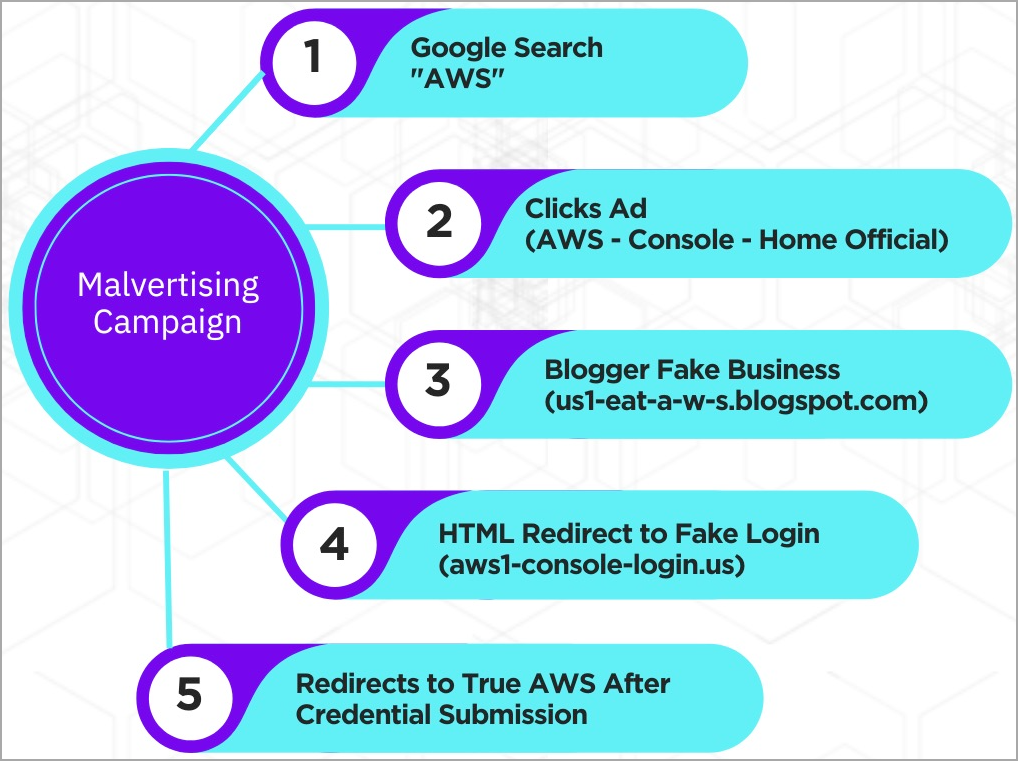
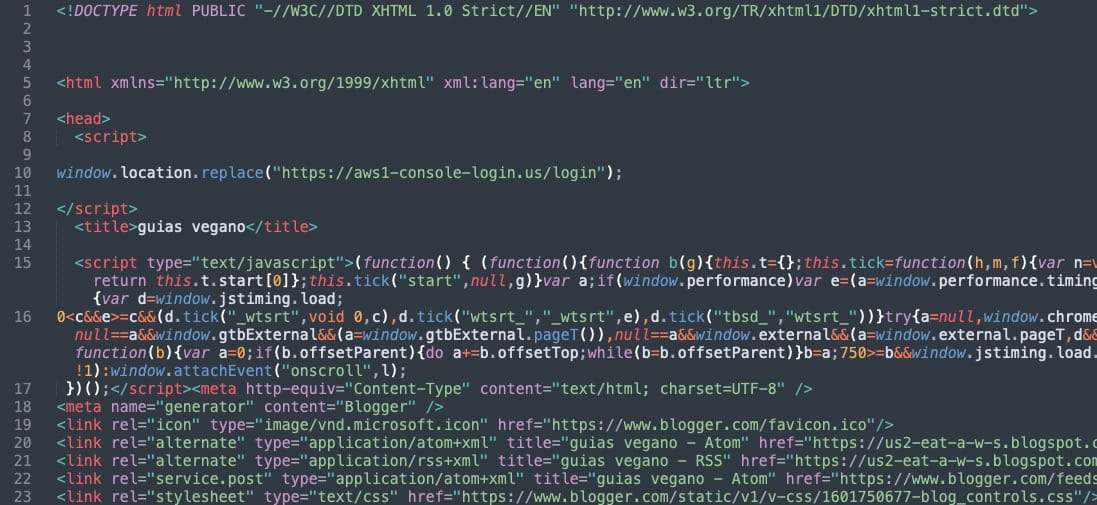
The malicious Google ads take the victim to a blogger website (“us1-eat-a-w-s.blogspot[.]com”) under the attackers’ control, which is a copy of a legitimate vegan food blog.
The site uses ‘window.location.replace’ to automatically redirect the victim to a new website that hosts the fake AWS login page, made to appear authentic.
The victim is prompted to select if they are a root or IAM user and then enter their email address and password. This option helps the threat actors categorize the stolen data into two categories of value and utility.
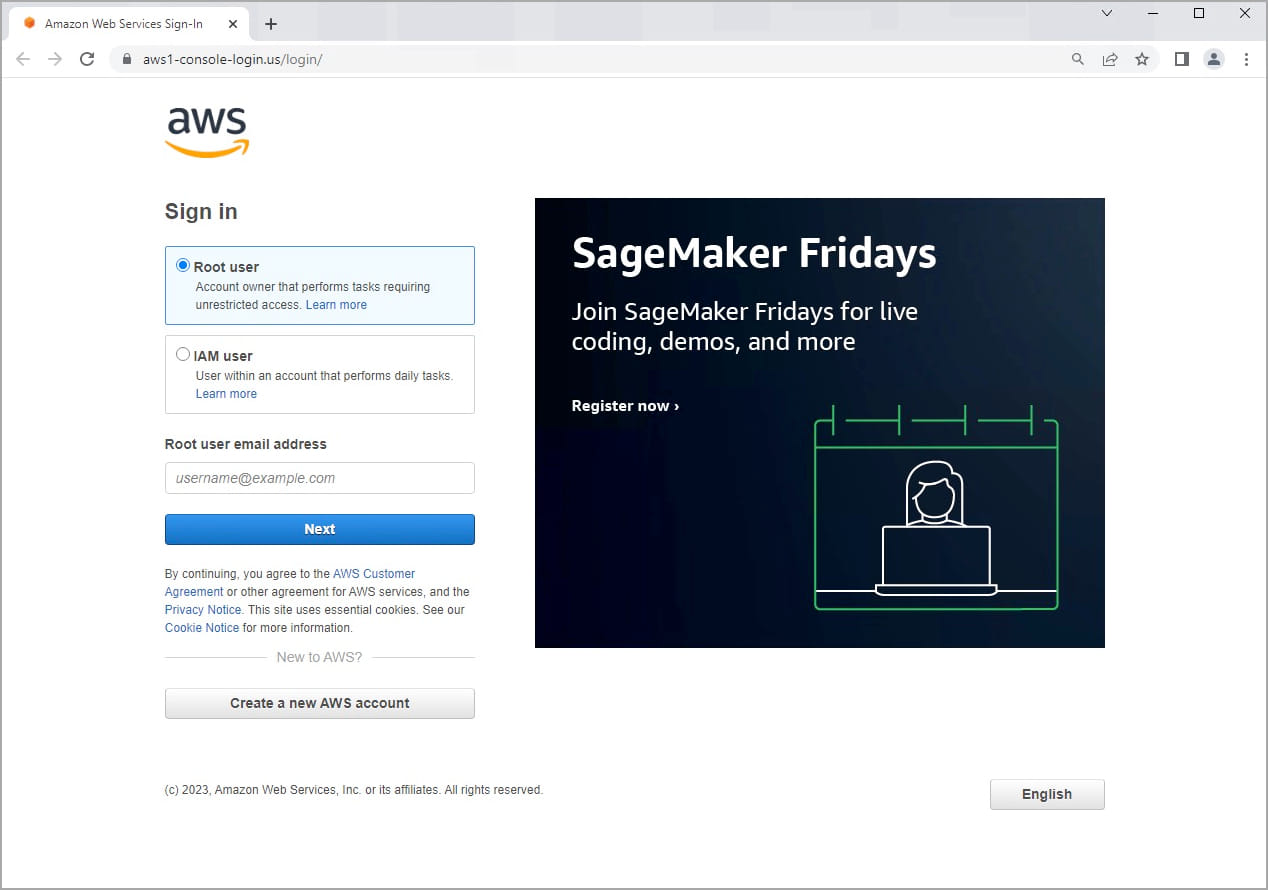
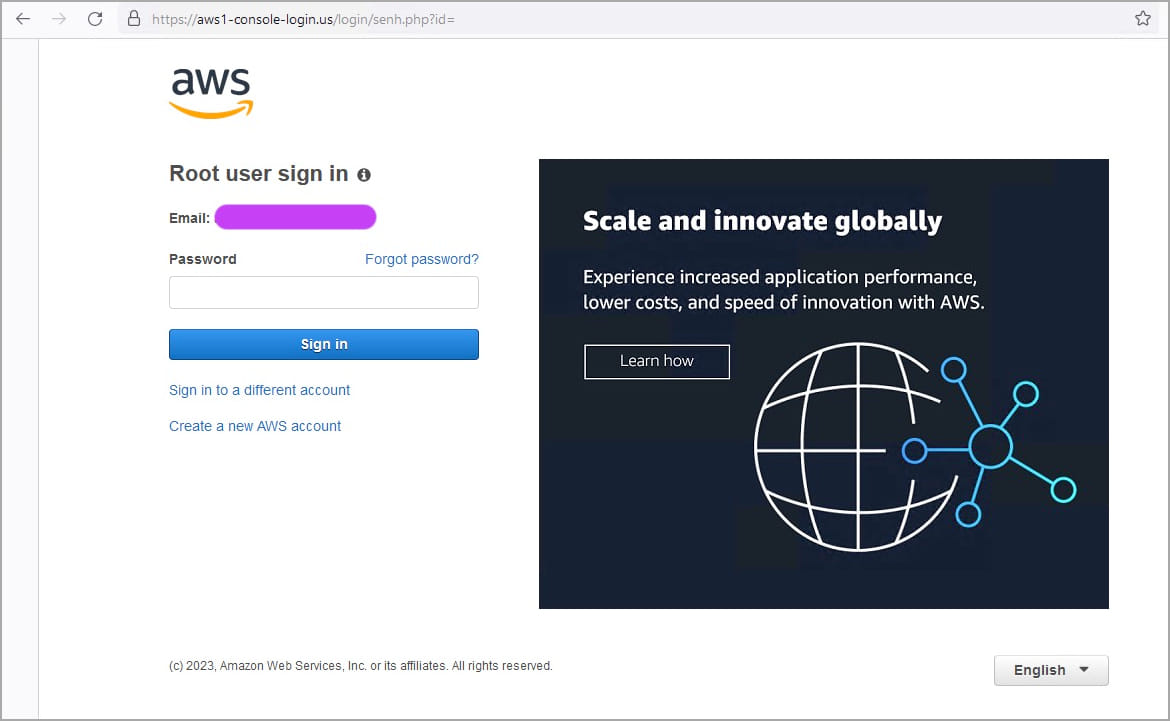
The phishing domains seen by Sentinel Labs are:
- aws1-console-login[.]us
- aws2-console-login[.]xyz
- aws1-ec2-console[.]com
- aws1-us-west[.]info
An interesting feature of the phishing pages is that their author has included a JavaScript function to disable right clicks, middle mouse buttons, or keyboard shortcuts.
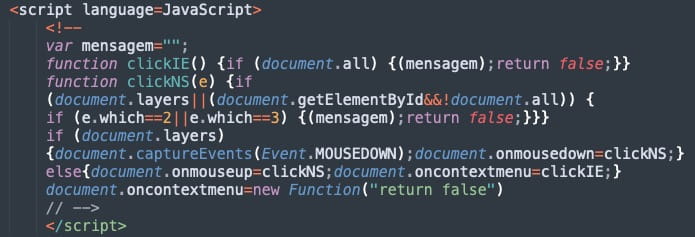
Sentinel Labs says this is likely a mechanism to prevent users from navigating away from the page, either purposefully or by mistake.
The security firm reports seeing Portuguese used as a language in the JavaScript code comments and variables, while the root page of the blogger domain mimics a Brazilian dessert business. Finally, the Whois details used for registering the domains point to a Brazilian person.
Sentinel Labs reported the abuse to CloudFlare, which protected the phishing sites, and the internet company quickly shut down the account. However, the malicious Google Ads remain, even if the sites they link to are no longer online.
Google Ads have been under massive abuse from cybercriminals of all kinds lately, serving as an alternative method to reach potential victims.
These ads have been used lately for phishing password manager accounts, achieving initial network compromise for ransomware deployment, and malware distribution masquerading legitimate software tools.
Last week, Sentinel Labs discovered a campaign that uses virtualization technology together with Google Ads to spread malware that makes it harder to detect by antivirus tools.
