Two botnets tracked as ‘Ficora’ and ‘Capsaicin’ have recorded increased activity in targeting D-Link routers that have reached end of life or are running outdated firmware versions.
The list of targets includes popular D-Link devices used by individuals and organizations such as DIR-645, DIR-806, GO-RT-AC750, and DIR-845L.
For initial access, the two pieces of malware use known exploits for CVE-2015-2051, CVE-2019-10891, CVE-2022-37056, and CVE-2024-33112.
Once a device is compromised, attackers leverage weaknesses in in D-Link’s management interface (HNAP) and execute malicious commands through a GetDeviceSettings action.
The botnets can steal data and execute shell scripts. Attackers appear to compromise the devices for distributed denial-of-service (DDoS) purposes.
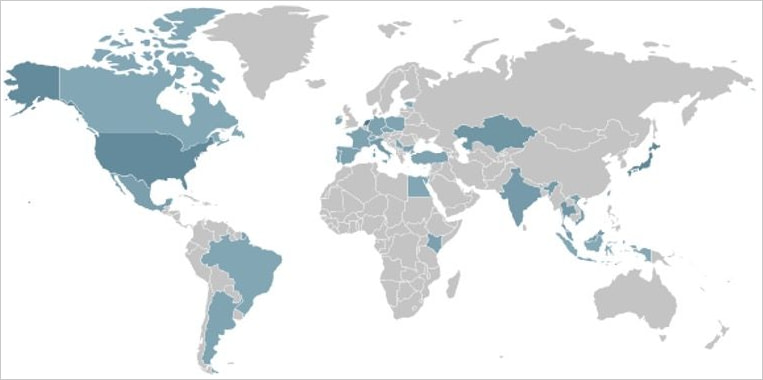
Ficora has a widespread geographic distribution with some focus on Japan and the United States. Capsaicin appears to be targeting mostly devices in East Asian countries and increased its activity for just two days, starting on October 21.
Ficora botnet
Ficora is a newer variant of the Mirai botnet, adapted to exploit flaws in D-Link devices specifically.
According to Fortinet’s telemetry data, the botnet shows random targeting, with two notable surges in its activity during October and November.
Source: Fortinet
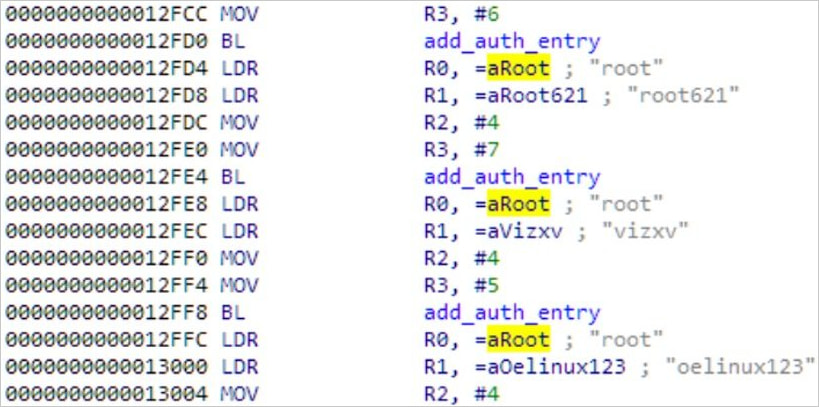
After gaining initial access on D-Link devices, Ficora uses a shell script named ‘multi’ to download and execute its payload through multiple methods like wget, curl, ftpget, and tftp.
The malware includes a built-in brute force component with hard-coded credentials to infect additional Linux-based devices, while it supports multiple hardware architectures.
Source: Fortinet
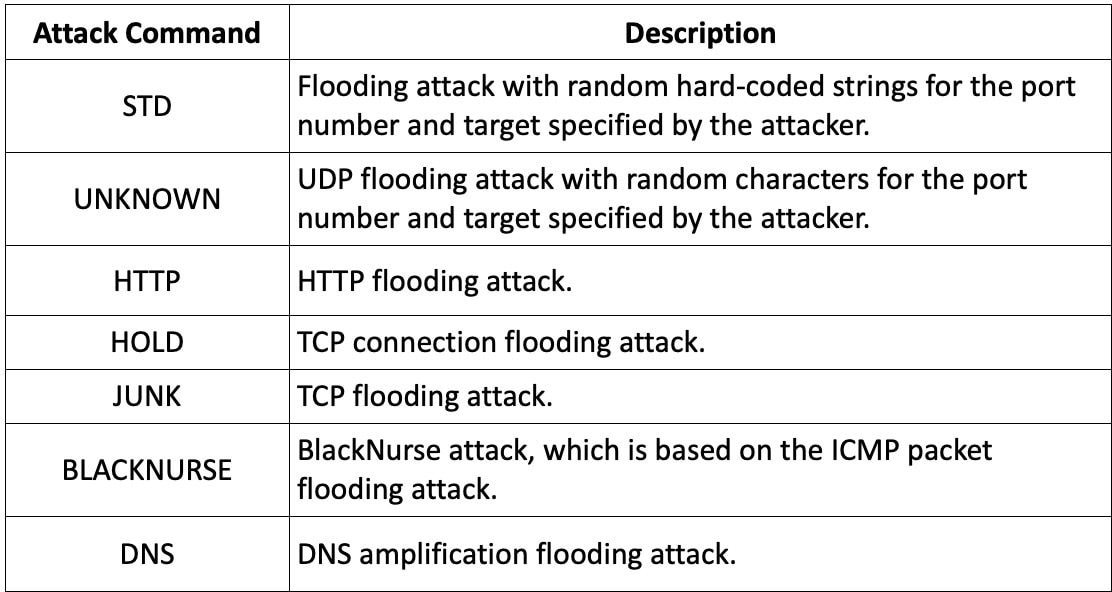
Regarding its DDoS capabilities, it supports UDP flooding, TCP flooding, and DNS amplification to maximize the power of its attacks.
Capsaicin botnet
Capsaicin is a variant of the Kaiten botnet and is believed to be malware developed by the Keksec group, known for ‘EnemyBot’ and other malware families targeting Linux devices.
Fortinet only observed it in a burst of attacks between October 21 and 22, targeting primarily East Asian countries.
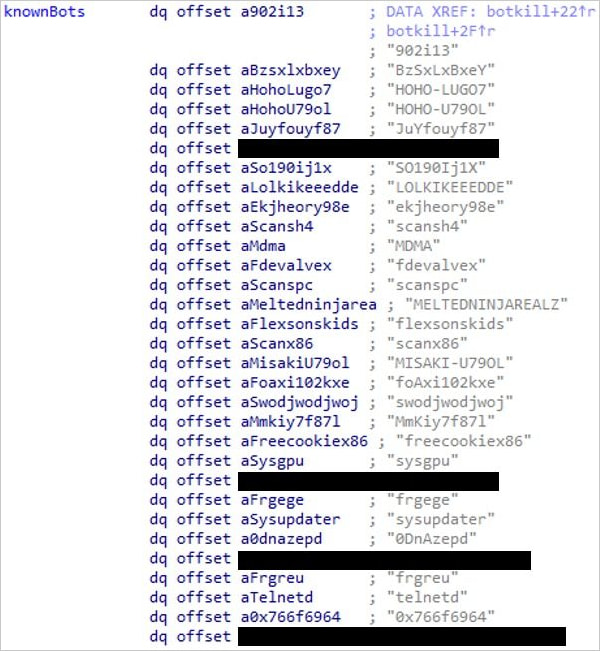
The infection occurs through a downloader script (“bins.sh”), which fetches binaries with the prefix ‘yakuza’ for different architectures, including arm, mips, sparc, and x86.
The malware actively looks for other botnet payloads that are active on the same host, and disable them.
Source: Fortinet
Apart from its DDoS capabilities, which mirror those of Ficora, Capsaicin can also gather host information and exfiltrate it to the command and control (C2) server for tracking.
Source: Fortinet
Defending against botnets
One way to prevent botnet malware infections on routers and IoT devices is to ensure that they’re running the latest firmware version, which should addresses known vulnerabilities.
If the device has reached end-of-life and no longer receives security updates, it should be replaced with a new model.
A a general advice, you should replace default admin credentials with unique and strong passwords and disable remote access interfaces if not needed.




