According to the application security provider Checkmarx, cybercriminals concealed malicious code, masquerading as Dependabot, within GitHub repositories as part of a supply chain attack.
Cybersecurity experts have uncovered a series of malicious code injections camouflaged as legitimate Dependabot contributions across hundreds of GitHub repositories. These incidents, which occurred in July 2023, have raised concerns about the security of personal access tokens (PATs) on GitHub and the growing sophistication of threat actors in supply chain attacks.
What is Dependabot in GitHub?
Dependabot is a GitHub-native tool for automating dependency updates in software projects hosted on GitHub. It helps developers keep their projects up to date by automatically monitoring the project’s dependencies (such as libraries and packages) for security vulnerabilities and outdated versions.
When Dependabot detects that an update is available or a security vulnerability has been patched, it generates pull requests with the necessary updates. This simplifies the process of maintaining dependencies and ensures that projects stay secure and up to date with the latest software components.
The Deceptive Attack
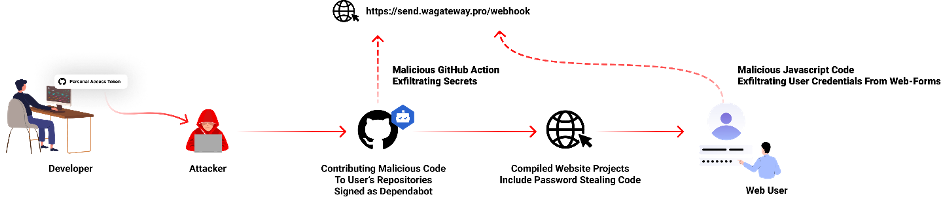
During the first half of July, threat actors targeted a wide range of GitHub repositories, affecting both public and private projects. The victims primarily consisted of Indonesian user accounts, making it a significant and potentially widespread issue. The attackers utilized a clever technique to mimic Dependabot’s commit messages, deceiving developers into believing these were authentic contributions.
The falsified commit messages often bore the name “dependabot,” effectively camouflaging their activities and evading suspicion. Within these repositories, experts discovered two distinct groups of code alterations, strongly suggesting automated script usage by the attackers.
Malicious Payload and Tactics
According to a blog post from Guy Nachshon of Checkmarx, the attackers introduced a new GitHub Action file named “hook.yml” into the repositories, creating a new workflow that triggered during code pushes. This action siphoned GitHub secrets and variables, sending them to a suspicious URL, (sendwagateway.pro/webhook). This maneuver was executed with every push event, compounding the potential damage.
Additionally, the malicious actors tampered with existing project files bearing the “.js” extension. An obfuscated line of code was appended to these files, designed to create a new script tag upon execution in a browser environment. This new code aimed to load an external script from (sendwagatewaypro/client.js?cache=ignore), with the sinister purpose of intercepting web-based password forms and transmitting user credentials to the same exfiltration endpoint.
Uncovering the Attack Vector
Initially, it remained unclear how the attackers gained access to the targeted accounts, given GitHub’s strengthened mandatory two-factor authentication (2FA) measures. To shed light on the situation, experts contacted some of the victims and discovered that the attackers had exploited compromised PATs (Personal Access Tokens).
These tokens, stored locally on developers’ machines, facilitate Git operations without requiring 2FA. Attackers seemingly extracted these tokens quietly from the victims’ development environments, potentially through a malicious open-source package that had infiltrated their systems.
Automated Scale of the Attack
Analyzing the scale of the attack indicated a high level of automation in the threat actor’s approach. The efficiency and sophistication of the attack underscored the need for increased vigilance among developers and software maintainers.
Lessons Learned and Moving Forward
This incident serves as a reminder of the importance of code source verification, even from trusted platforms like GitHub. It highlights that even well-established platforms can fall victim to such attacks, emphasizing the need for continuous online vigilance.
To enhance security, developers are urged to consider adopting GitHub’s fine-grained personal access tokens, reducing the risk associated with compromised tokens. However, it’s worth noting that access log activity for personal access tokens is currently visible only for enterprise accounts, leaving non-enterprise users less informed about potential breaches.
The attackers’ Tactics, Techniques, and Procedures (TTPs) demonstrate a growing sophistication in supply chain attacks. Their use of fake commits, credential theft, and Dependabot impersonation highlights the evolving threat landscape.
RELATED ARTICLES
- New backdoor malware hits Slack and Github platforms
- Hackers use GitHub bot to steal $1,200 in ETH within 100 seconds
- Hackers can spoof commit metadata to create false GitHub repositories



