A large-scale brute force password attack using almost 2.8 million IP addresses is underway, attempting to guess the credentials for a wide range of networking devices, including those from Palo Alto Networks, Ivanti, and SonicWall.
A brute force attack is when threat actors attempt to repeatedly log into an account or device using many usernames and passwords until the correct combination is found. Once they have access to the correct credentials, the threat actors can then use them to hijack a device or gain access to a network.
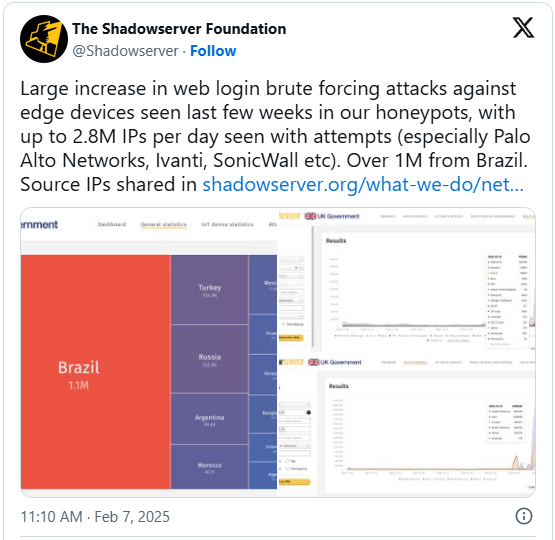
According to the threat monitoring platform The Shadowserver Foundation, a brute force attack has been ongoing since last month, employing almost 2.8 million source IP addresses daily to perform these attacks.
Most of these (1.1 million) are from Brazil, followed by Turkey, Russia, Argentina, Morocco, and Mexico, but there’s generally a very large number of countries of origin participating in the activity.
These are edge security devices like firewalls, VPNs, gateways, and other security appliances, often exposed to the internet to facilitate remote access.
The devices conducting these attacks are mostly MikroTik, Huawei, Cisco, Boa, and ZTE routers and IoTs, which are commonly compromised by large malware botnets.
In a statement to BleepingComputer, The Shadowserver Foundation confirmed that the activity has been ongoing for a while but recently increased to a much larger scale.
ShadowServer also said that the attacking IP addresses are spread across many networks and Autonomous Systems and are likely a botnet or some operation associated with residential proxy networks.
Residential proxies are IP addresses assigned to consumer customers of Internet Service Providers (ISPs), making them highly sought after for use in cybercrime, scraping, geo-restriction bypasses, ad verification, sneaker/ticket scalping, and more.
These proxies route internet traffic through residential networks, making it appear that the user is a regular home user rather than a bot, data scraper, or hacker.
Gateway devices such as those targeted by this activity could be used as proxy exit nodes in residential proxying operations, routing malicious traffic through an organization’s enterprise network.
These nodes are considered “high-quality” as organizations have a good reputation, and the attacks are harder to detect and stop.
Steps to protect edge devices from brute-forcing attacks include changing the default admin password to a strong and unique one, enforcing multi-factor authentication (MFA), using an allowlist of trusted IPs, and disabling web admin interfaces if they’re not needed.
Ultimately, applying the latest firmware and security updates on those devices is crucial in eliminating vulnerabilities that threat actors can leverage to gain initial access.
Last April, Cisco warned about a large-scale credential brute-forcing campaign targeting Cisco, CheckPoint, Fortinet, SonicWall, and Ubiquiti devices worldwide.
In December, Citrix also warned about password spray attacks targeting Citrix Netscaler devices worlwide.
