In a new turn of events, two major corporations of Italian and Canadian origin are facing the MEDUSA cyber attack.
In their latest claims, the MEDUSA ransomware group has claimed two major entities, Landstar Power Ontario Inc. and Acoustic Center, adding them to their dark web portal.
The cybercriminals posted ominous countdowns on their portal, heightening the tension for the affected companies.
The attack was announced via their dark web portal, where they have also shared a tight deadline before the stolen data gets published.
MEDUSA Cyber Attack Claimed Two New Victims
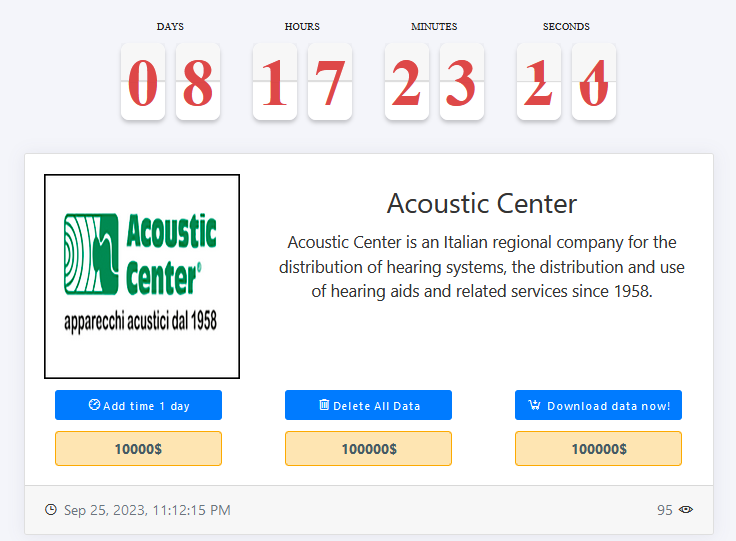
The first victim of this MEDUSA cyber attack is the Acoustic Center. This esteemed Italian regional company has been dedicated to the distribution of hearing systems, as well as the provision of hearing aids and related services since 1958.
The MEDUSA ransomware group has demanded a hefty ransom for the release of their data, threatening to delete it if their demands are not met within a stipulated time frame.
The deadline given is 1 day, with a ransom of $10,000, which escalates to $100,000 after the deadline. The attack occurred on September 25, 2023, at 11:12:15 PM.

The second victim listed claimed in the MEDUSA cyber attack is Landstar Power Ontario Inc, a Canadian enterprise specializing in the purchase of used batteries and assorted scrap metal for resale, which now finds itself trapped in the attack.
The ransomware group has issued a similar request, demanding a substantial ransom for the safe release of their data. The deadline given is 1 day, with a ransom of $10,000, which escalates to $100,000 after the deadline. The attack occurred on September 26, 2023, at 11:14:54 PM.
Medusa Ransomware group: A formidable attacker!
Despite these distressing developments, The Cyber Express sought to verify the situation by reaching out to the Acoustic Center. Unfortunately, at the time of writing, no official statement or response has been received, leaving the claims of the MEDUSA ransomware attack still unverified.
Attempts to reach out to the second victim in the MEDUSA attack have gone in vain as well because the victim doesn’t seem to have any official website or a contact page.
As for the threat actor in this cyber attack, much like the mythological namesake, the Medusa ransomware group uses the same technique as the mythological character — holding the victim’s data hostage and rendering the digital systems unusable.
Since its emergence in June 2021, the Medusa ransomware group has remained a prominent concern for cybersecurity experts. Operating through the Ransomware-as-a-Service (RaaS) model, the MEDUSA ransomware group collaborates with global affiliates, expanding its reach and impact.
Medusa Ransomware distinguishes itself with a multifaceted approach, akin to the myriad serpentine locks of the Gorgon’s hair. Each encrypted file bears various extensions, reminiscent of the many snakes adorning Medusa’s head. Foremost among them is the unmistakable “.MEDUSA” extension, a hallmark of this ransomware’s iconic touch.
Earlier this year, the Minneapolis Public School (MPS) District faced a MEDUSA cyber attack. Initially refusing to pay a $1 million ransom, the district claimed to have successfully restored its encrypted systems from backups.
However, the MEDUSA ransomware group, not content with mere encryption, exfiltrated their copy of the data, ultimately publishing it on the internet and promoting it via a Telegram channel.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
