The Medusa ransomware group has added the International Civil Defense Organization (ICDO) to its list of targeted victims.
The hacker collective has set a deadline of nine days and 15 hours for their ransom demand following the ICDO cyber attack announcement.
ICDO cyber attack post by Medusa
The ICDO ransomware attack claim was made on August 19, according to the screenshot tweeted by Ransomfeed, an international ransomware monitoring service.

The post claiming the ICDO cyber attack had the ransom amounts noted on it and was viewed by 110 people on the dark web when captured by researchers.

Moreover, they stipulated a sum of $100,000 for the complete deletion of exfiltrated data resulting from the ICDO ransomware attack.
Additionally, they threatened with a ransom demand of $100,000 to have ICDO download all their stolen data from the hackers.
The website of ICDO was accessible at the time of writing. The Cyber Express has emailed ICDO requesting a statement regarding the cyber attack claim. We will update this report based on its response.
The Medusa ransomware group also claimed cyber attacks on two more organizations besides the International Civil Defense Organization. They were –
- Novi Pazar-Put
- Sartrouville France
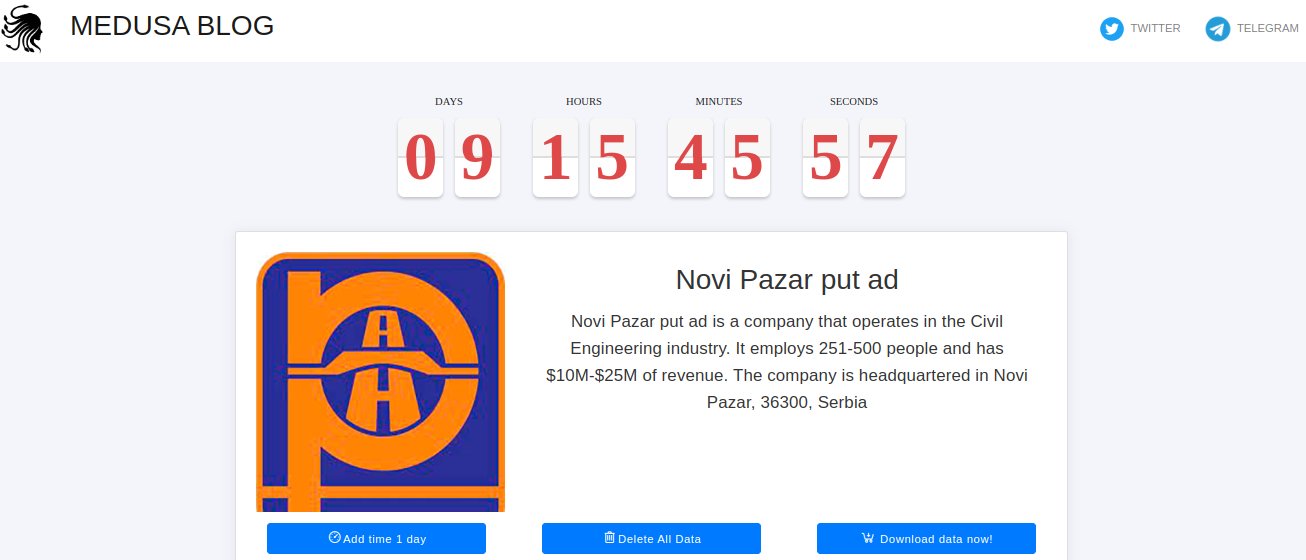
The deadline placed on the Novi Pazar-Put cyber attack claim was also nine days and 15 hours similar to ICDO.
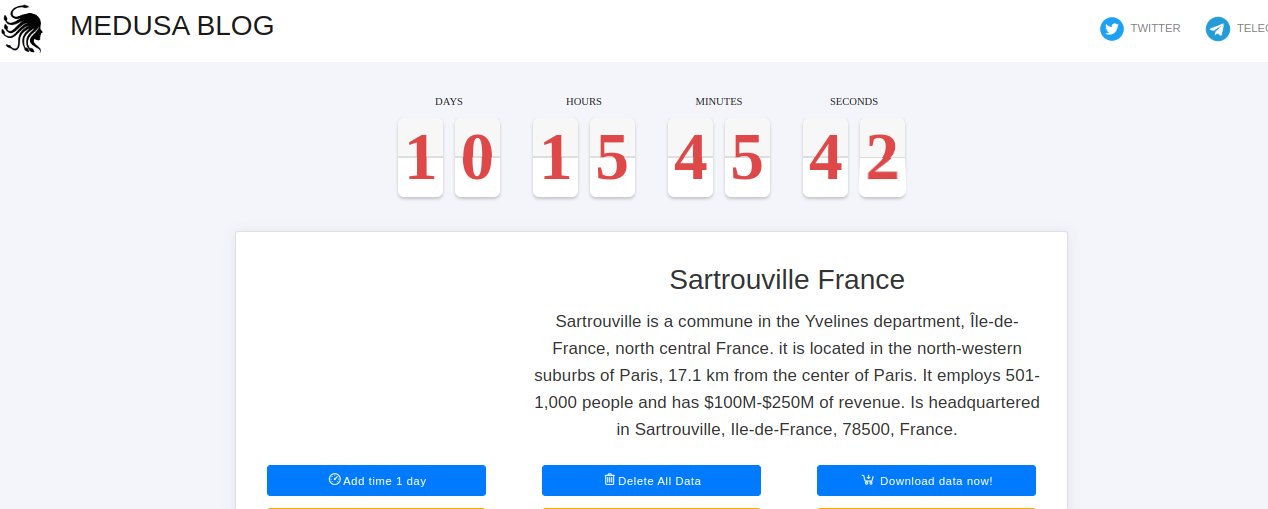
However, the deadline for ransom payment for Sartrouville France was 10 days and 15 hours, at the time of posting the same on the dark web portal by Medusa.
Details about the organizations listed by Medusa
The International Civil Defense Organization is based in Switzerland and it is an intergovernmental organization that works toward the development of its states and people.
Novi Pazar-Put is based in Serbia and is part of the civil engineering industry.
Sartrouville is a commune that is a part of north-central France. In the post, tweeted by threat Intelligence Platform Falcon Feeds, Medusa claimed that Sartrouville had a revenue of nearly $250 million.
Targets of the Medusa ransomware group
The Medusa ransomware group found active since June 2021 demands a ransom close to $1 million in exchange for the decryption key. However, a Tech Radar report added that there were other cybercriminal groups with the same name.
An example was the MedusaLocker ransomware group which was discovered in 2019. MedusaLocker’s ransom note leaves a .HTML file named How_to_back_files.
While the Medusa ransomware group leaves a note named !!!READ_ME_MEDUSA!!!. in the .TXT format.
Medusa encrypts files with the .MEDUSA extension while MedusaLocker has been known to change extensions.

Medusa ransomware group named Borets International Limited to its victim list last week. Borets is headquartered in Texas, United States and has its international headquarter in Dubai.
The hackers claimed to have 1TB of data from the alleged Borets cyber attack.
Borets (Levare.com) specializes in the engineering, manufacturing, and service of electric submersible pump systems.
In the dark web post made on August 14, the deadline of nine days and 21 hours was given to the targeted organization.
Among its other recent posts, the ransomware group named the Italy-based company Postel SpA to its victim list.
The software products and management services company was given a deadline of eight days in a post published on August 15, 2023.
It remains to be seen how the threats take effect after the deadlines given to the respective companies pass.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
