It’s not every day that you discover a new Russian hacking group complete with a song and dance routine (performed live), a sleek user interface (with dark mode!) and a clearly thought-out business model. But that is exactly what our security research team discovered with “AlphaLock,” a “pentesting training organization” that trains hackers and then monetizes their services through a dedicated affiliate program.
We originally discovered their group through a public Telegram channel that has since become private. This post will serve as a detailed investigation and description of one of the most brazen, strange, and best marketed cybercrime groups to appear in 2023.
AlphaLock’s Business Model and Launch
One of the most poignant cybercrime trends in 2023 has been the diversification and role specialization that has occurred among criminals. There are detailed and complex supply chains that exist, creating economies of scale for cybercriminals.
AlphaLock serves as one of the first and interesting examples we’ve seen of a threat group trying to create their own end to end pipeline to generate revenue.
Their business model seems to be split into two parts: Bazooka Code Pentest Training and the ALPentest Hacking Marketplace.
AlphaLock Business Model Part One: Bazooka Code Pentest Training
Nobody wants to believe that they are the bad guy, even for threat actors. AlphaLock takes measures to claim that they are simply training “pentesters,” a phenomenon that is familiar to any security researchers familiar with ransomware group messaging and their claims of “pentesting after the fact.”
AlphaLock’s business model seems to be split into two parts. The first part involves training an “army” of hackers through customized online courses.
The threat actors explain in detail on their Telegram channel:
“Today, to a greater extent, the first stream got their money back. The best immediately got to work; we are waiting for the rest to improve their skills.
In two months, we have gathered a very strong staff and trained them for ourselves.
The time will come when this era will end, and the best will simply disappear, and you will no longer hear about them; they will quietly earn a living for their grandchildren and great-grandchildren.
Most likely, I was able to prove to people that we take entry money not to earn, but for other reasons. Our team, consisting of almost 100 people, exceeds the age limit of many Telegram chats.
Most likely, someday we will go white and will work on the analysis and protection of large corporations. All the best go through a dark past, and that’s a fact.
To all our colleagues, I recommend showing patience and applying efforts to study PenTesting.
PenTesting is the future.
With love, AlphaLock”
But maybe after reading this you still have reservations.
Can the Bazooka Code course really help you earn a living and justify a $185 dollar expense? AlphaLock has done the math.
“Education prices at Lomonosov Moscow State University vary from 383,550 rubles to 540,000 rubles per year. On average, the cost of education is about 395,375 rubles per year or 197,687 rubles per semester. You will study there for 4 to 6 years – mathematics, physics, cybernetics, chemistry, biology, soil science, geology, geography, medicine, history, philology, philosophy, economics, jurisprudence, journalism, psychology, area studies, sociology, management, politics, and political science, etc.
Let’s take the worst option that is considered good in Russia – 395,475*4 = 1,581,660 rubles to graduate as a journalist. According to GorodRabot, the average salary of a journalist in Russia for the year 2023 is 46,161 rubles. In a month, the salary has changed by 11.4% – from 40,915 to 46,161 rubles. Most often, job vacancies offer a salary of 30,000 rubles (modal).
1,581,660 rubles divided by 40,915 rubles = 38 months, or for 3 years you will be paying back your education at the unfortunate university, without eating anything, owning any property, etc.
The bazookacode course now costs $185 and the training lasts 2 months, you get a team, knowledge, and tools for work, they advise and help you, you learn at speeds, as if in euphoria. The average poor carder in the worst-case scenario earns from $1,000 per month, I’m not even talking about networks and established work, let’s calculate how much time you need to pay back the education if you still managed to set up your own business and work?”
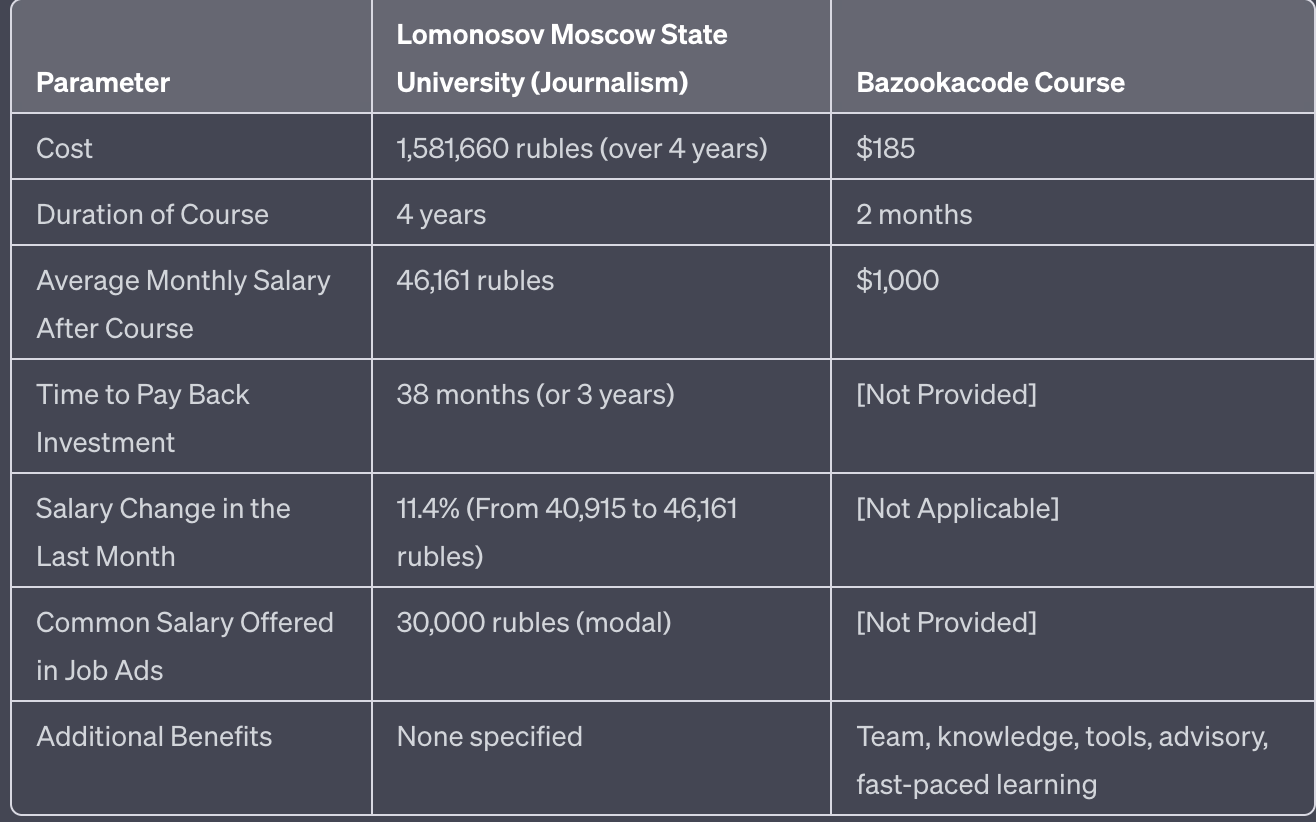
with the journalism degree at Lomonosov Moscow State University
As we said at the top, unique only begins to describe this group.
If the business model only involved selling pentesting courses at $185 though this would be fairly par for the course. However, this represents only stage one of AlphaLock’s plans.
The next step involves the dark web forum XSS, and an affiliate program where we suspect they plan to make the majority of their profits.
AlphaLock Business Model Part Two: The ALPentest Hacking Marketplace
The second part of this business scheme is a direct corollary to the first – use the newly trained hackers to create a marketplace where threat actors can purchase “pentesting services” targeted at a specific organization.
Below is a screenshot from their recently released dance video announcing the creation of the AlphaLock affiliate program:
Bazooka Code explains:
“We are preparing the world’s first platform where a client, in online mode, can monitor the performer’s process of implementation and resolution of the client’s issues, using an encrypted key.
Convenient for the client
Financially beneficial for the performer
On this platform, the performer will be able to conduct various penetration tests, including in the Red-team format. Classic external and internal penetration tests.”
Bazooka Code shared screenshots of the “beta” version of the new hacking marketplace. Threat actors will be able to list targets that they want to “pentest” and other threat actors can then attack the companies, post proof, and collect the reward money.
Presumably the hackers conducting the attacks will be staffed by the very same individuals that take part in the Bazooka Code course.
Unfortunately for Bazooka Code though, they appear to have attracted too much attention recently.
A few days ago they posted this long missive and announced that the entire program was moving to a new, lesser known and decentralized chat application, Matrix.
Dear friends, colleagues, and our readers, I will be making a lengthy statement and ask you to read it to the end. With the influx of the audience, we face a lot of negativity. We understand this means we are heading in the right direction, and it’s impossible to please everyone. Our team has never tried and will never try to justify ourselves if the situation doesn’t match reality; our time is more valuable than clarifying relations with people trying to impose their “incorrect, in our opinion, position”. At the same time, we always try to find an alternative for each of you, and our members who are already part of AL and in training sessions will confirm the quality of the information they receive. We ask not to comment on this message, and members of AL should refrain from doing so in the future. Word of mouth is welcome, but please avoid comments. We’ve realized that today. Several attempts have been made to access the account owner’s profile from different IPs, which means we are likely being watched by someone with an unhealthy interest. Let’s discuss the pressing issue: Those who take our courses have already learned to exploit vulnerabilities and are beginning to grasp the breadth of this direction. Most likely, we value these individuals more than those who have never been with us, and I hope you understand us correctly. Evidence of our loyalty includes:
- Deposit on the forum
- Opinions of AL members
- And that’s enough
Quality content on Telegram has fostered our growth, but from this moment, we are forced to leave this platform and move to Matrix, as we previously announced.
Telegram will now be used solely for accepting new membership requests and for news updates, with all inquiries addressed exclusively through support.
Many posts from this channel will be deleted due to their irrelevance.
However, we’re pleased to announce that we’re looking for a content creator, a designer with beautiful handwriting, someone who can manage not only Telegram but also other social boards.
We’ll soon launch a YouTube channel where you can invest your time and gain substantial experience.
If you are ready to engage in this activity, “write here” – “Immediately send your portfolio.”
Would you like more context or assistance related to this?
What Does all of this Mean?
AlphaLock appears to be at least relatively sophisticated and active across Telegram, Matrix, and the dark web forum XSS.
There are a few interesting insights we can gain into the broader cybercrime ecosystem from AlphaLock.
- Cybercrime sophistication and commoditization continues to grow: We now have a real life example of a threat group that seeks to create its own talent pool through a training program, goes to extensive lengths to market itself, and plans to monetize this through a hacker-for-hire scheme. The level of technical sophistication required to do this isn’t very high, but the level of organizational sophistication and business acumen is quite interesting.
- Ransomware isn’t the only game in town: Cybercriminals typically choose the path of least resistance that is most likely to prove profitable, this has been increasingly the case as the cybercrime ecosystem has evolved into a functional market economy. However AlphaLock represents another potential method to both monetize and democratize cybercrime. This could be a particularly interesting model alternative for ransomware groups if the U.S. follows through with the proposal of banning ransomware payments.
- A Technical Threat Actor Supply Shortage? One of the most fascinating things about AlphaLock is they want to create a pipeline of talent to populate their hacker marketplace. This suggests that there may be limitations on the supply of talented threat actors that have the required degree of sophistication to the point where they have tried to build their own pipeline of actors.
- The Brand: Our researchers have noted an increasing focus on group “brand” and identity among financially motivated threat groups. AlphaLock has clearly made significant investments in time to create a brand and reputation for itself. Notice in the final post they even advertise that they are looking to hire someone to market themselves on Telegram and social media.
- Blurred Lines: Many security practitioners have often assumed that threat actors primarily operate on the dark web. In most cases today this isn’t the case. There are increasingly blurred lines between clear web sites, Tor, and social media applications such as Telegram that create easy avenues for threat actors to congregate and communicate.
Monitor Illegal Telegram Groups & Other Sources with Flare
Flare delivers high-value, tailored continuous threat exposure management to organizations across industries.
Our SaaS platform detects threats across hundreds of dark web markets & forums, thousands of illicit Telegram channels, and clear web sources of risk.
Flare integrates into your existing security program in 30 minutes with native integrations that enable you to build a threat led cybersecurity program.
Sign up for a free trial to learn more.
Sponsored and written by Flare.
