Just days after we uncovered a campaign targeting Google Ads accounts, a similar attack has surfaced, this time aimed at Microsoft advertisers. These malicious ads, appearing on Google Search, are designed to steal the login information of users trying to access Microsoft’s advertising platform.
Microsoft does purchase ad space on its rival’s dominant search engine; however, we found Google sponsored results for “Microsoft Ads” (formerly known as Bing Ads) that contained malicious links created by impostors.
Through shared artifacts, we were able to identify additional phishing infrastructure targeting Microsoft accounts going back to a couple of years at least. We have reported these incidents to Google.
Fake Microsoft Ads caught on Google Search
Microsoft made an estimated $12.2 billion in search and news advertising revenues (including Bing) in 2023, which pales in comparison to its rival, Google, holding a much larger share of the search engine market.
Since the advertising ecosystem allows for an open competition between brands, Microsoft is trying to get traffic and earn clicks from Google searches. During our investigation, we saw sponsored results for Microsoft Ads and Bing Ads that managed to slip through Google’s security checks:
Redirection, cloaking and Cloudflare
The threat actors are using different techniques to evade detection and drop traffic from bots, security scanners and crawlers. Unwanted IP addresses (e.g. VPNs) are immediately redirected to a bogus marketing website (Figure 2). This is also known as a “white page”, meaning it looks innocent and hides its maliciousness.
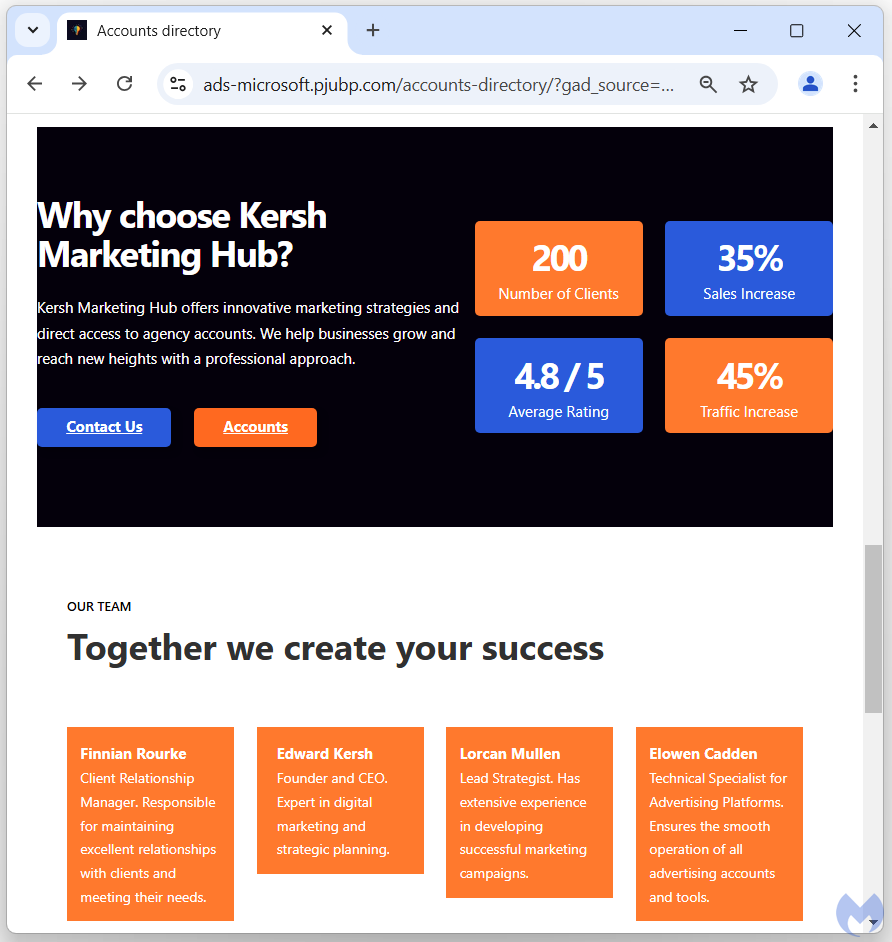
Users that appear to be genuine are presented with a Cloudflare challenge to verify they are human. This is a legitimate instance of Cloudflare, unlike the “ClickFix” type-of-attacks that have become very common place and trick people into pasting and executing malicious code.

Rickroll for the cheaters
After a successful Cloudflare check, users are redirected to the final phishing page via a special URL, that acts as some sort of entry point for the malicious domain ads[.]mcrosoftt[.]com. You can see the network requests related to this redirection chain in Figure 4 below.
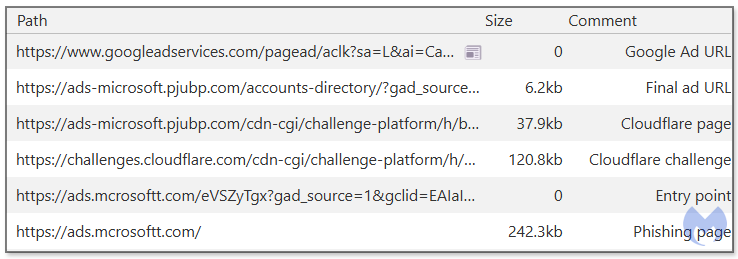
If you were to visit that domain directly instead of going through the proper ad click you’d be greeted with a rickroll, an internet meme designed to make fun of someone. The sandbox for the web urlscan.io has several examples of crawl requests for URLs on that server (37.120.222[.]165) that all went to the rickroll.
Phishing page
After much subversion, real victims finally see the phishing page for the Microsoft Advertising platform. The full URL in the address bar is meant to imitate the legitimate one (ads.microsoft.com).
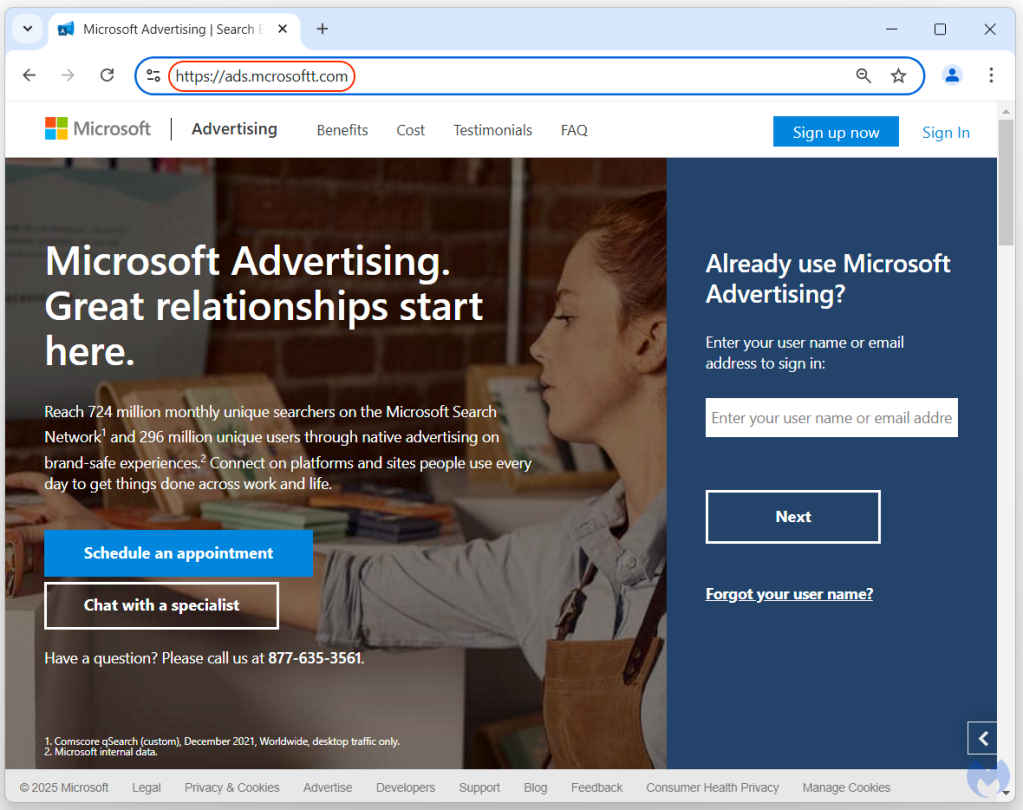
The phishing page gives user a fake error message enticing them to reset their password and seemingly tries to get past 2-Step verification as well. Handling 2FA has become a standard feature in most phishing kits, due to the rise in user adoption of this additional security layer.

Larger campaign
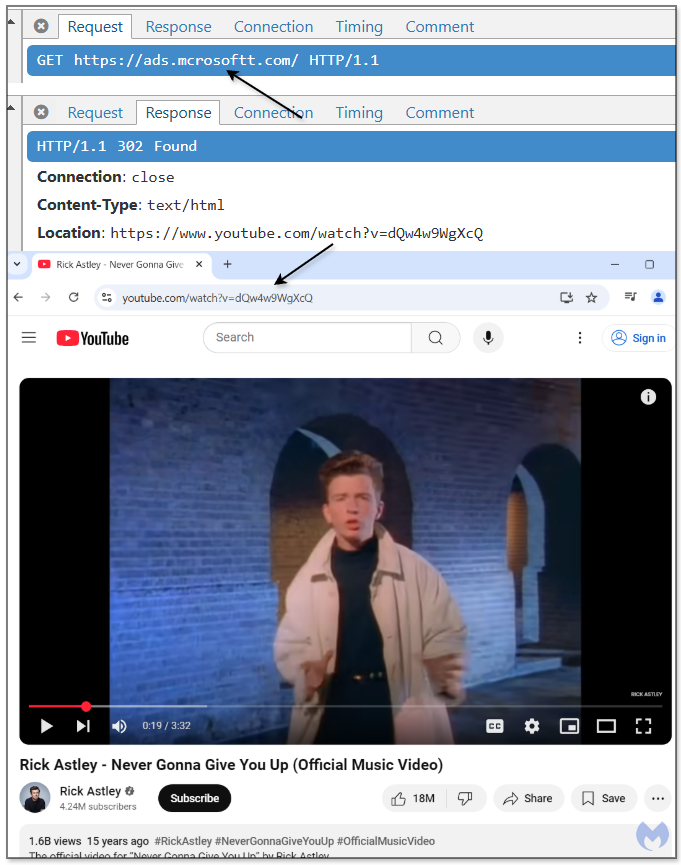
Going back to urlscanio, we fed it the special entry URL and it was able to navigate to the phishing page. From there, we can look at the various web requests and find something to pivot on in order to identify additional infrastructure.
The favicon.ico file is one starting point and we can query for any scans that match its hash, excluding the official Microsoft domain. The results show that in the past week, there were several other domains that appear to be related to the theft of Microsoft Ads accounts.
But this campaign appears to go back further at least a couple of years and maybe more, although it becomes somewhat tricky to know if the malicious infrastructure is tied to the same threat actors. It’s worth noting that several of the domains are either hosted in Brazil or have the ‘.com.br‘ Brazilian top-level domain.
What we discovered may only be the tip of the iceberg; by starting to investigate compromised advertiser accounts we may very well have opened Pandora’s box. This isn’t only Google or Microsoft ad accounts we are talking about, but potentially for Facebook, and many others. Of course, our scope so far has been Google Search, but we know that other platforms are rife with such phishing attacks.
These recent malvertising campaigns highlight the ongoing threat of phishing through online advertising. While tech companies like Google work to combat these issues, users must remain vigilant. Here are some key steps you can take to protect yourself:
- Verify URLs: Always carefully examine the URL in your browser’s address bar before entering any credentials. Scrutinize URLs for inconsistencies or misspellings.
- Use 2-Step verification wisely: it adds an extra layer of security to your accounts, but you still need to pay attention to requests before granting them access.
- Regularly monitor your accounts: Check your advertising accounts for any suspicious activity such as changes in administrator accounts.
- Report Ads: If you encounter a suspicious ad, report it to for the benefit of other users.
We don’t just report on threats—we block them
Malwarebytes Browser Guard offers traditional ad-blocking augmented with advanced heuristic detection. Download it today.
Indicators of Compromise
The following IOCs are comprised of domains that shared attributes with our initial phishing page, including the favicon and images. Some of them go back further but are provided for threat hunters who may wish to further investigate these campaigns.
30yp[.]com
aboutadvertselive[.]com
aboutblngmicro[.]cloud
account-microsoft[.]online
account-microsoft[.]site
account-mircrosoft-ads[.]com
account[.]colndcx-app[.]com
accounts-ads[.]site
accounts-mircrosoft-ads[.]online
acount-exchang[.]store
admicrosoft[.]com
admicrsdft[.]com
ads-adversitingb[.]com
ads-dsas[.]site
ads-microsoft[.]click
ads-microsoft[.]coachb-learning[.]com
ads-microsoft[.]live
ads-microsoft[.]lubrine[.]com[.]br
ads-microsoft[.]online
ads-microsoft[.]shop
ads-microsoftz[.]online
ads-miicrosoft[.]com
ads-mlcrosft[.]com
ads-mlcrosoft-com[.]blokchaln[.]com
ads[.]microsoft[.]com[.]euroinvest[.]ge
ads[.]mlcr0soft[.]com
ads[.]mlcrosoft[.]com[.]ciree[.]com[.]br
ads[.]mlcrosoft[.]com[.]poezija[.]com[.]hr
ads[.]rnlcrosoft[.]com[.]euroinvest[.]ge
adslbing[.]com
adsmicro[.]exchangefastex[.]cloud
adsmicrosoft[.]shop
adsverstoni[.]com
advertiseliveonline[.]com
advertising-bing[.]site
advertising-mlcrosoft[.]org
adverts2023[.]online
advertsingsinginbing[.]com
agency-wasabi[.]com
app[.]beefylswap[.]top
bîlkub[.]com
bing-ads[.]com
bing[.]login-acount[.]me
bitmax-us[.]com
blngad[.]online
blseaccount[.]cloud
bltrue[.]colnhouse-fr[.]us
côinlíst[.]online
colneex-plalform[.]cloud
connec-exchan[.]site
digitechmedia[.]agency
forteautomobile[.]com
global-verifications[.]com
global-verify[.]com
homee-acount[.]com
itlinks[.]com[.]cn
krakeri-login[.]com
login-adsmicrosoft[.]helpexellent[.]com
login[.]adsadvertising[.]online
login[.]microsofttclicks[.]live
micrasofit[.]xyz
microosft[.]accounts-ads[.]site
microsoft-ads[.]website
microsoftadss[.]com
microsoftadversiting[.]cloud
microsoftbingads[.]com
microsofyt[.]adversing-publicidade[.]pro
mictrest[.]mnws[.]ru
mlcrosoft-bing-acces[.]click
mlcrosoftadvertlsing[.]online
mudinhox[.]site
ndnet[.]shop
phlyd[.]com
portfoliokrakenus[.]com
portfoliolkraken[.]com
portfoliopro-us[.]com
portfolioskranen[.]com
portofolioprospots[.]com
potfoliokeiolenen[.]com
potfoliokelaken[.]com
potfoliokelaneken[.]com
potfoliokenaiken[.]com
potfoliokenkren[.]com
potfolioketonelen[.]com
potfolioskaneken[.]com
potfolioskenaken[.]com
potfolioskraineken[.]com
potfolioskranaken[.]com
potfolioskraneken[.]com
pro-digitalus[.]com
prokrakenportfolio[.]com
rnlcrosoft[.]smartlabor[.]it
sig-in-mlcrosoft-advertisings[.]site
uiiadvertise[.]online
wvvw-microsoft[.]xyz
www-bingads[.]com
www-microsoftsads[.]com
www-v[.]userads[.]digital
www34[.]con-webs[.]com
www55[.]con-webs[.]com
