A dangerous shift in phishing tactics, with threat actors increasingly hosting malicious infrastructure on trusted cloud platforms like Microsoft Azure, Google Firebase, and AWS CloudFront.
Unlike traditional phishing campaigns that rely on newly registered suspicious domains, these attacks leverage legitimate cloud services to bypass security defenses and target enterprise users globally.
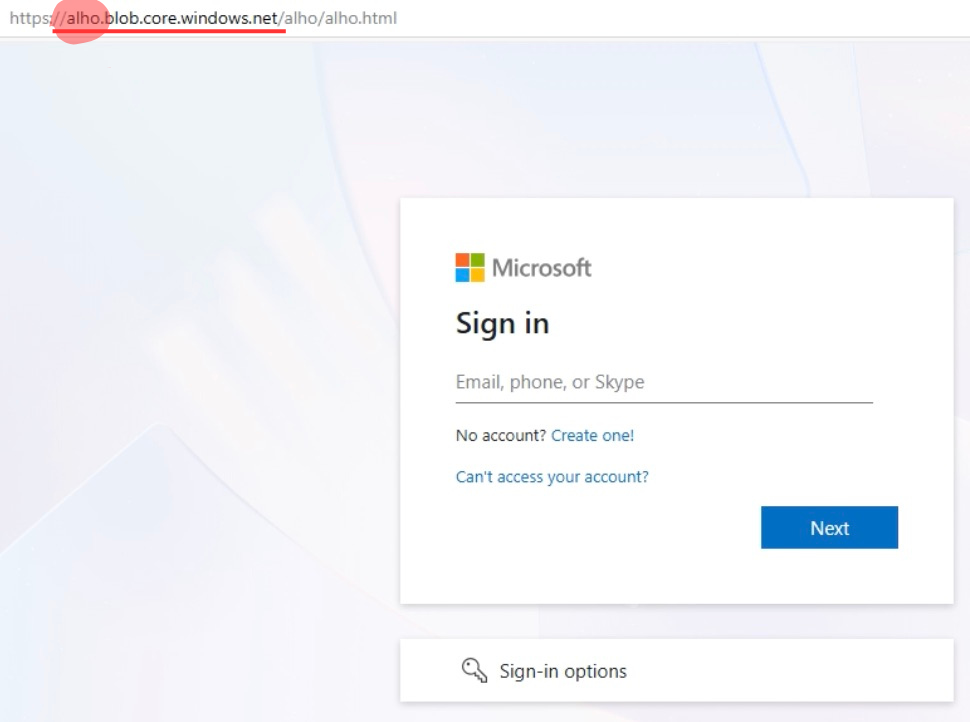
When malicious content is hosted on domains like blob.core.windows.net or firebasestorage.googleapis.com, traditional security indicators become unreliable. The attacks appear to originate from trusted sources, making detection extremely difficult.
The most sophisticated phishing campaigns today use Adversary-in-the-Middle (AiTM) kits that act as proxies between victims and legitimate services.
Modern phishing campaigns have evolved beyond easily detectable fake domains. Threat actors now abuse reputable cloud infrastructure to host their phishing kits, creating significant challenges for security teams.
These toolsets enable threat actors to intercept credentials and session tokens in real-time, even bypassing multi-factor authentication. Three phishing kits dominate the enterprise threat landscape: Tycoon2FA, Sneaky2FA, and EvilProxy.
Tycoon2FA operates as a Phishing-as-a-Service platform specifically designed to defeat MFA protections.
Sneaky2FA focuses exclusively on corporate accounts, filtering out personal email addresses from providers like Gmail and Yahoo.
EvilProxy uses reverse-proxy techniques to target high-ranking executives for account takeover attacks. All three kits increasingly rely on trusted cloud infrastructure rather than disposable domains.
Cloudflare and Cloud Platforms
Threat actors choose Cloudflare CDN and major cloud platforms for specific tactical advantages. Cloudflare’s reverse proxy architecture hides the actual origin servers behind trusted IP addresses, making it nearly impossible for security teams to block or trace malicious infrastructure.
Attackers increasingly rely on trusted platforms to evade detection, reflecting cloud-based phishing growth to a mainstream technique.

When analysts investigate suspicious activity, they only see legitimate Cloudflare network traffic with valid HTTPS certificates.
Cloud platforms like Microsoft Azure Blob Storage, Google Firebase, and AWS CloudFront provide similar benefits.
These services offer built-in anti-analysis features, including CAPTCHA challenges, geographic filtering, and user-agent validation that block automated security scanners.
If one malicious domain gets taken down, attackers register another and hide it behind the same trusted infrastructure within minutes.
Traditional security indicators have become ineffective against cloud-hosted phishing. IP addresses, TLS fingerprints, and SSL certificates no longer reliably identify malicious activity when campaigns run on shared cloud infrastructure.
A credential theft page hosted on Microsoft’s legitimate blob.core.windows.net domain appears identical to authentic Microsoft services from a network perspective.
Recent analysis shows the problem is rapidly escalating. Within just one week, documented cases of Tycoon2FA phishing hosted on Microsoft Azure nearly doubled.
Security teams in the United States and Europe now encounter these attacks multiple times daily. The phishing pages perfectly mimic legitimate login flows, even returning “wrong password” error messages that match authentic Microsoft authentication responses.
Impact on Business Security
In observed Tycoon2FA campaigns, victims receive emails containing links that lead through multiple redirects and CAPTCHA challenges before reaching a fake login page.
The credential theft form appears on legitimate Microsoft Azure domains, making it indistinguishable from real Microsoft 365 login pages.
When victims enter their passwords, the data is transmitted via POST requests to attacker-controlled servers while the victim sees familiar Microsoft error messages.
Sneaky2FA campaigns specifically target large organizations by filtering out personal email accounts. The kit uses Base64-encoded domain lists to ensure only corporate email addresses can access the phishing pages.
These attacks commonly appear on Google Firebase Storage and AWS CloudFront infrastructure. EvilProxy follows similar patterns, hosting fake login pages on legitimate Google domains to compromise executive accounts.
The shift to cloud-hosted phishing creates measurable risks for enterprises. Traditional perimeter defenses cannot effectively block traffic from trusted cloud providers without disrupting legitimate business operations.
Static security indicators and domain reputation systems fail when attackers operate from Microsoft, Google, and Amazon infrastructure.
Many organizations experience data breaches because their security tools cannot detect these sophisticated attacks in time.
The multi-stage nature of modern phishing further complicates detection. Attacks include QR codes in emails, multiple redirect chains, CAPTCHA challenges, and anti-analysis techniques that specifically evade automated security systems.
By the time a victim reaches the actual credential theft page, the attack has already bypassed most traditional security layers.
Effective defense against cloud-hosted phishing requires fundamental changes in security approach.
Organizations must move beyond static indicators and implement behavioral analysis that identifies malicious activity regardless of hosting infrastructure.
Interactive malware analysis allows security teams to safely follow entire attack chains in isolated environments, revealing the final credential theft pages hidden behind evasion layers.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.