Microsoft has silently “mitigated” a high-severity Windows LNK vulnerability exploited by multiple state-backed and cybercrime hacking groups in zero-day attacks.
Tracked as CVE-2025-9491, this security flaw allows attackers to hide malicious commands within Windows LNK files, which can be used to deploy malware and gain persistence on compromised devices. However, the attacks require user interaction to succeed, as they involve tricking potential victims into opening malicious Windows Shell Link (.lnk) files.
Threat actors distribute these files in ZIP or other archives because email platforms commonly block .lnk attachments due to their risky nature.
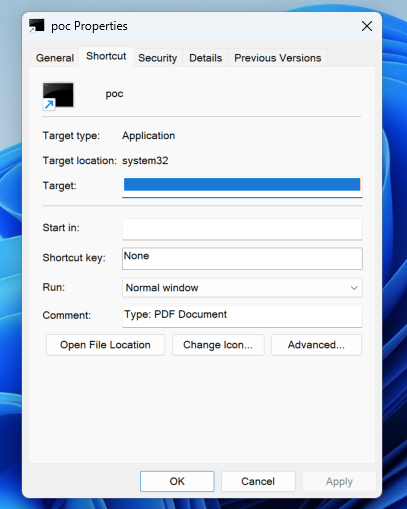
The vulnerability lies in how Windows handles .LNK files, allowing threat actors to exploit the way the operating system displays them to evade detection and execute code on vulnerable devices without the user’s knowledge by padding the Target field in Windows .LNK files with whitespaces to hide malicious command-line arguments.
This ensures that the file’s Target field properties display only the first 260 characters due to the added whitespaces, so users can’t see the actual command executed when the LNK file is double-clicked.
As Trend Micro threat analysts discovered in March 2025, the CVE-2025-9491 was already being widely exploited by 11 state-sponsored groups and cybercrime gangs, including Evil Corp, Bitter, APT37, APT43 (also known as Kimsuky), Mustang Panda, SideWinder, RedHotel, Konni, and others.
”Diverse malware payloads and loaders like Ursnif, Gh0st RAT, and Trickbot have been tracked in these campaigns, with malware-as-a-service (MaaS) platforms complicating the threat landscape,” Trend Micro said.
Arctic Wolf Labs also reported in October that the Chinese state-backed Mustang Panda hacking group was exploiting this Windows vulnerability in zero-day attacks targeting European diplomats in Hungary, Belgium, and other European nations to deploy the PlugX remote access trojan (RAT) malware.
Microsoft pushes silent “patch”
Microsoft told BleepingComputer in March that it would “consider addressing” this zero-day flaw, even though it didn’t “meet the bar for immediate servicing.”
It also added in a November advisory that it doesn’t consider this a vulnerability “due to the user interaction involved and the fact that the system already warns users that this format is untrusted,” even though threat actors could still exploit a Mark of the Web bypass vulnerability to circumvent these warnings and ensure their attacks’ success.
Despite this, as ACROS Security CEO and 0patch co-founder Mitja Kolsek found, Microsoft has silently changed LNK files in the November updates in an apparent effort to mitigate the CVE-2025-9491 flaw. After installing last month’s updates, users can now see all characters in the Target field when opening the Properties of LNK files, not just the first 260.
However, this isn’t necessarily a fix since malicious arguments added to LNK files will not be deleted, and the user receives no warning when opening LNK files with a Target string exceeding 260 characters
A Microsoft spokesperson was not immediately available for comment when contacted by BleepingComputer earlier today to confirm if this change is an attempt to mitigate the vulnerability.
Unofficial patches available
Until Microsoft adequately addresses this security flaw, ACROS Security has released an unofficial patch via its 0Patch micropatch platform, which limits all shortcut target strings to 260 characters and warns users about the potential danger of opening shortcuts with unusually long target strings.
“Our patch would break the 1000+ malicious shortcuts identified by Trend Micro for all targeted users, while Microsoft’s patch would only allow the most cautious among these users – who would probably not launch such shortcuts anyway – to see the entire malicious command string,” Kolsek said.
“Even though malicious shortcuts could be constructed with fewer than 260 characters, we believe disrupting actual attacks detected in the wild can make a big difference for those targeted.”
ACROS Security’s unofficial CVE-2025-9491 patch is available for 0patch users with PRO or Enterprise accounts who use Windows versions that have reached end of support (Windows 7 through Windows 11 22H2, and Windows Server 2008 R2 through Windows Server 2022).

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.
