Microsoft will introduce improved protection against phishing attacks pushing malware via malicious Microsoft OneNote files.
In a new Microsoft 365 roadmap entry published today titled “Microsoft OneNote : improved protection against known high risk phishing file types,” the company revealed that this change would likely reach general availability sometime before the end of April 2023.
“We add enhanced protection when users open or download an embedded file in OneNote,” Redmond explained.
“Users will receive a notification when the files deem dangerous to improve the file protection experience in OneNote on Windows.”
This comes after a recent wave of phishing attacks where threat actors used maliciously crafted OneNote documents with ‘.one’ file extensions and embedded files hidden behind overlays asking the targets to click to view the document.
Double-clicking launches the embedded file, which might seem innocuous but can have severe consequences.
Sadly, even when receiving security warnings, users often ignore them and allow the file to run, potentially putting their entire corporate network at risk.
FYI, this is how malicious Microsoft OneNote documents are created.
Embed the same attachment multiple times in a row. Then overlay it with a call-to-action box to click here.
However, double-clicking on the “button” actually double-clicks on the embedded file, and launches it. pic.twitter.com/B4WbyJcVWr
— BleepingComputer (@BleepinComputer) March 6, 2023
This is a lesson that everyone should’ve learned by now from previous phishing attacks that took advantage of Microsoft Office macros.
Unfortunately, it only takes one user to accidentally run a malicious file to infect themselves with information-stealing malware or, even worse, trigger a ransomware attack.
To thwart phishing attacks using malicious Microsoft OneNote attachments, you can set up secure mail gateways or mail servers to automatically block OneNote documents with .one extensions.
Windows admins can also use Microsoft Office group policies to prevent embedded OneNote files from launching.
To do that, you must install the Microsoft 365/Microsoft Office group policy templates and enable the ‘Disable embedded files’ and ‘Embedded Files Blocked Extensions’ Microsoft OneNote policies.
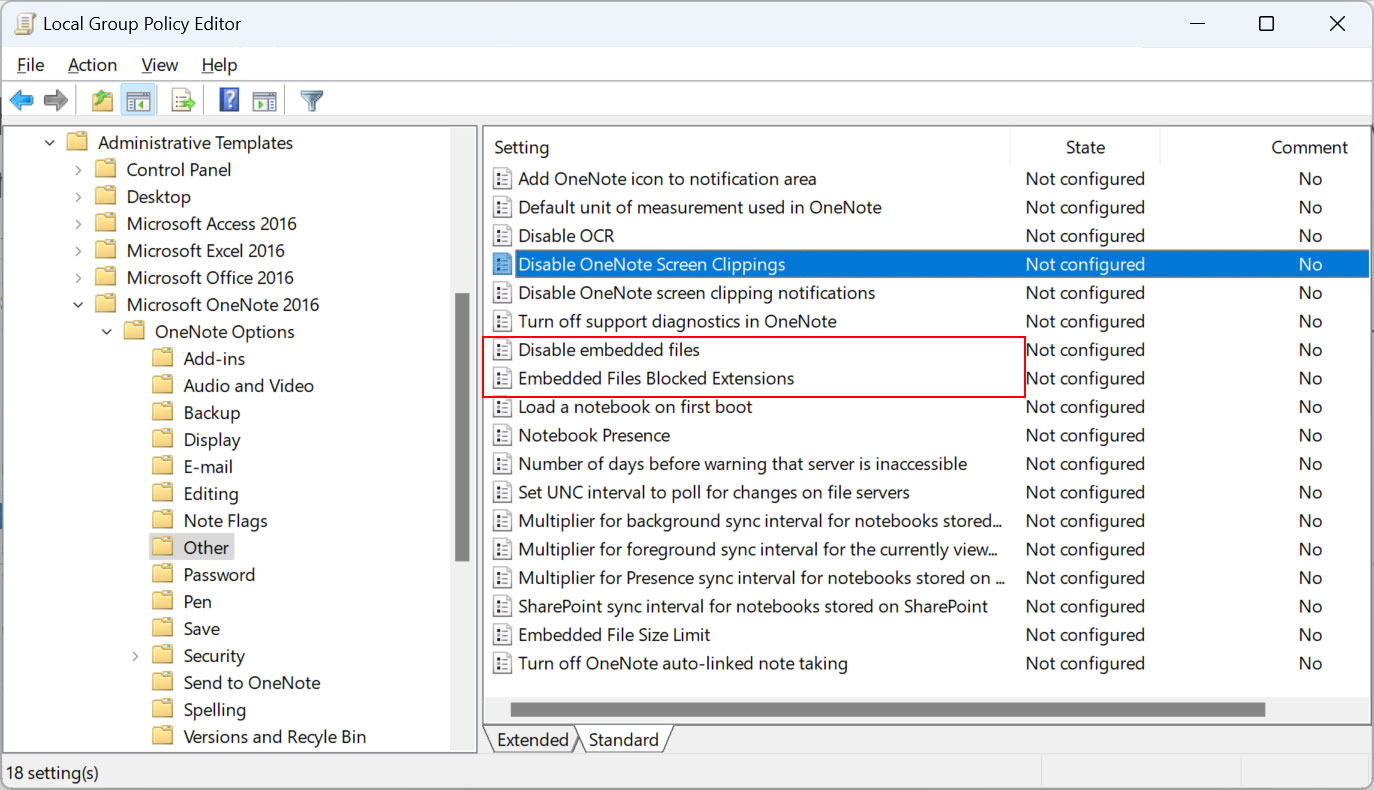
Threat actors have been using OneNote documents in spear phishing campaigns since mid-December 2022, as Trustwace also reported earlier this week.
Attackers have been spotted abusing OneNote files for various malicious purposes, including downloading and installing malware payloads like info stealers.
The switch to OneNote came after Microsoft finally disabled Word and Excel macros by default and patched a MoTW bypass zero-day used to deliver malware via ISO and ZIP files.
