Microsoft released an emergency security update for the Windows 10 and Windows 11 Snipping tool to fix the Acropalypse privacy vulnerability.
Now tracked as CVE-2023-28303, the Acropalypse vulnerability is caused by image editors not properly removing cropped image data when overwriting the original file.
For example, if you take a screenshot and crop out sensitive information, such as account numbers, you should have reasonable expectations that this cropped data will be removed when saving the image.
However, with this bug, both the Google Pixel’s Markup Tool and the Windows Snipping Tool were found to be leaving the cropped data within the original file.
For example, in the image below, you can see how extra data is saved after the IEND file marker, which denotes the end of a PNG file. Normally, there should be no data after the IEND marker.
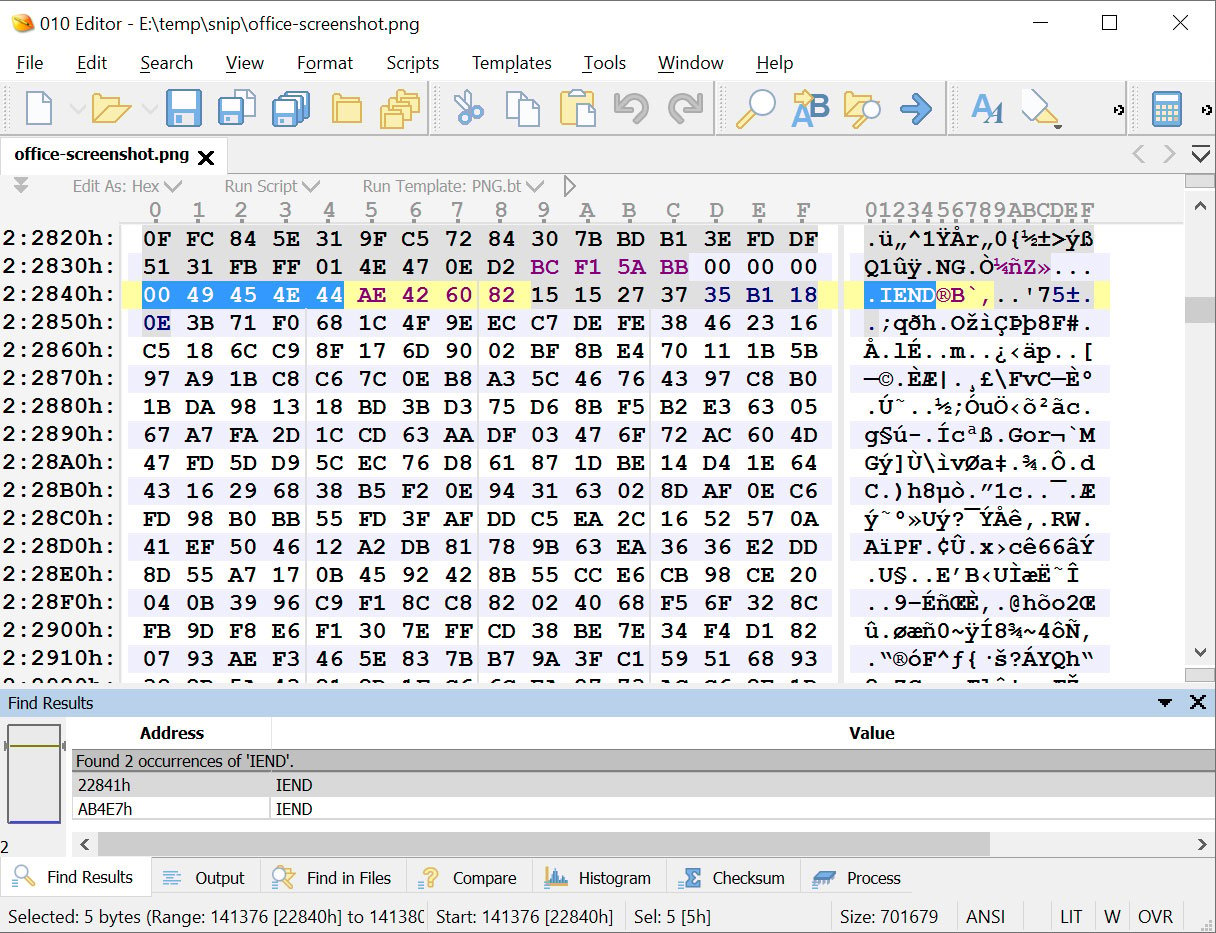
Source: BleepingComputer
This extra data could be used to partially recover the cropped image content, potentially exposing sensitive content that was never meant to be public.
Security researchers have told BleepingComputer that the number of public images impacted by this flaw may be high, with VirusTotal alone hosting over 4,000 images affected by the Acropalypse bug.
Therefore, on services catering to image hosting, the number of Acropalypse-impacted images is likely much higher.
Microsoft releases OOB security update
As BleepingComputer reported, Microsoft was testing a fix for the Windows 11 Snipping Tool bug in the Windows Insider Canary channel.
Last night, Microsoft publicly released security updates for both the Windows 10 Snip & Sketch and Windows 11 Snipping Tool program to resolve the Acropalypse flaw.
“We have released a security update for these tools via CVE-2023-28303. We recommend customers apply the update,” Microsoft told BleepingComputer.
After installing this security update, Windows 11 Snipping Tool will be version 10.2008.3001.0, and Windows 10 Snip & Sketch will be version 11.2302.20.0.
Microsoft is now tracking the vulnerability as CVE-2023-28303 and titled it “Windows Snipping Tool Information Disclosure Vulnerability.”
The vulnerability is classified as “Low” severity because it “requires uncommon user interaction and several factors outside of an attacker’s control.”
- The user must take a screenshot, save it to a file, modify the file (for example, crop it), and then save the modified file to the same location.
- The user must open an image in Snipping Tool, modify the file (for example, crop it), and then save the modified file to the same location.
With that said, in our experience, it is not uncommon to take a screenshot, save it, and then realize you need to crop something out and then overwrite the original image. This image would now have been affected by the bug.
The good news is regardless of how the image is created if you do not share an affected image publicly, you will have little risk of the flaw being exploited unless your device is compromised.
To install the security updates, open the Microsoft Store and go to Libary > Get Updates, and the latest version of the Windows Snipping Tool will be automatically installed.
