Microsoft warns that attackers are deploying malware in ViewState code injection attacks using static ASP. NET machine keys found online.
As Microsoft Threat Intelligence experts recently discovered, some developers use ASP.NET validationKey and decryptionKey keys (designed to protect ViewState from tampering and information disclosure) found on code documentation and repository platforms in their own software.
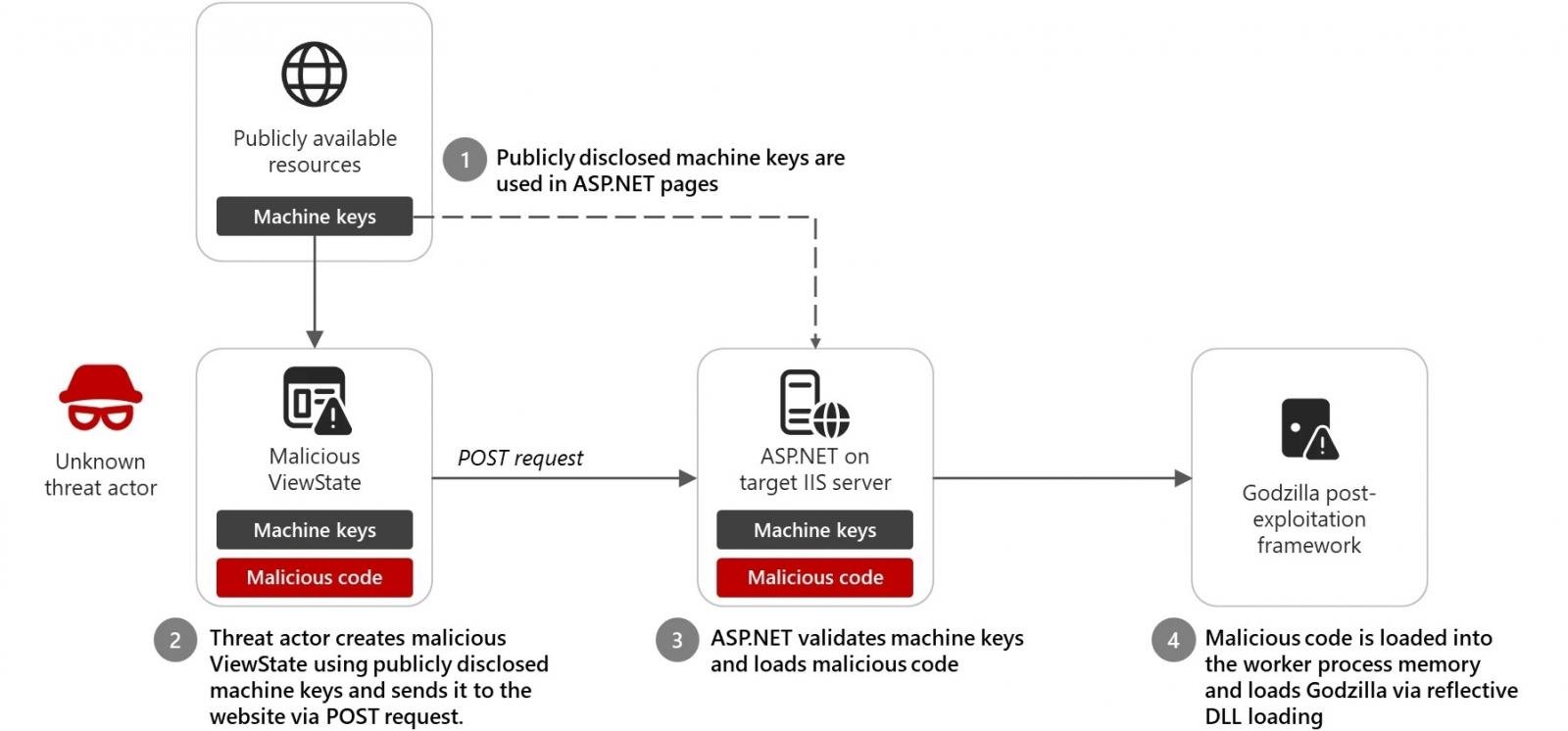
However, threat actors also use machine keys from publicly available sources in code injection attacks to create malicious ViewStates (used by ASP.NET Web Forms to control state and preserve pages) by attaching crafted message authentication code (MAC).
When loading the ViewStates sent via POST requests, the ASP.NET Runtime on the targeted server decrypts and validates the attackers’ maliciously crafted ViewState data because it uses the right keys, loads it into the worker process memory, and executes it.
This allows them to execute code remotely on the IIS server and deploy additional malicious payloads.
In one instance observed in December 2024, an unattributed attacker used a publicly known machine key to deliver the Godzilla post-exploitation framework, which comes with malicious command execution and shellcode injection capabilities, to a targeted Internet Information Services (IIS) web server.
“Microsoft has since identified over 3,000 publicly disclosed keys that could be used for these types of attacks, which are called ViewState code injection attacks,” the company said on Thursday.
“Whereas many previously known ViewState code injection attacks used compromised or stolen keys that are often sold on dark web forums, these publicly disclosed keys could pose a higher risk because they are available in multiple code repositories and could have been pushed into development code without modification.”
To block such attacks, Microsoft recommends developers securely generate machine keys, not use default keys or keys found online, encrypt machineKey and connectionStrings elements to block access to plaintext secrets, upgrade apps to use ASP.NET 4.8 to enable Antimalware Scan Interface (AMSI) capabilities, and harden Windows Servers by using attack surface reduction rules such as Block Webshell creation for Servers.
Microsoft also shared detailed steps for removing or replacing ASP.NET keys in the web.config configuration file using either PowerShell or the IIS manager console and removed key samples from its public documentation to further discourage this insecure practice.
“If successful exploitation of publicly disclosed keys has occurred, rotating machine keys will not sufficiently address possible backdoors or persistence methods established by a threat actor or other post-exploitation activity, and additional investigation may be warranted,” Redmond warned.
“In particular, web-facing servers should be fully investigated and strongly considered for re-formatting and re-installation in an offline medium in cases where publicly disclosed keys have been identified, as these servers are most at risk of possible exploitation.”
