Microsoft has released a PowerShell script to automate updating the Windows Recovery Environment (WinRE) partition in order to fix CVE-2024-20666, a vulnerability that allowed for BitLocker encryption bypass.
This security issue was resolved in the KB5034441 security update released earlier this week during this month’s Patch Tuesday.
The PowerShell script addresses a known issue causing KB5034441 install failures on Windows 10 systems, which leaves the devices vulnerable to the BitLocker encryption bypass flaw that allows access to encrypted data.
When trying to deploy the security update, users report seeing 0x80070643 errors, saying, “There were some problems installing updates, but we’ll try again later. If you keep seeing this and want to search the web or contact support for information, this may help: (0x80070643).”
As Microsoft explains, this happens because instead of displaying a CBS_E_INSUFFICIENT_DISK_SPACE error when the WinRE partition is not large enough, Windows Update incorrectly says the generic “0x80070643 – ERROR_INSTALL_FAILURE” error message instead.
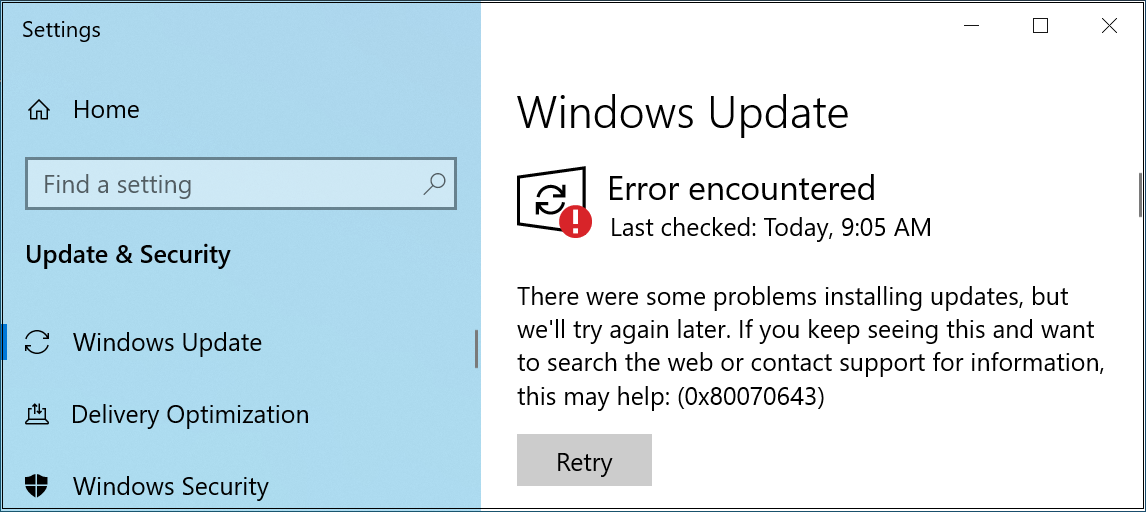
This happens because the WinRE image file (winre.wim) deployed when installing the KB5034441 security update is too large for the recovery partition.
To address the issue, Microsoft advised users to create a larger WinRE partition to have enough room for KB5034441 to install.
Automate BitLocker encryption bypass patching
While you can do this manually using detailed—and quite complex—instructions, the company now also provides a dedicated PowerShell script to help you automate updating the WinRE partition (without having to resize it first) and patching the CVE-2024-20666 BitLocker vulnerability.
“The sample PowerShell script was developed by the Microsoft product team to help automate the updating of WinRE images on supported Windows 10 and Windows 11 devices,” Microsoft said.
“Run the script with Administrator credentials in PowerShell on the affected devices. There are two scripts available—which script you should use depends on the version of Windows you are running.”
When running the script on your system, it mounts the WinRE image, applies an architecture-specific Safe OS Dynamic Update you have to download from the Windows Update Catalog before running the script, unmounts the image, and then reconfigures WinRE for BitLocker service if the BitLocker TPM protector is present.
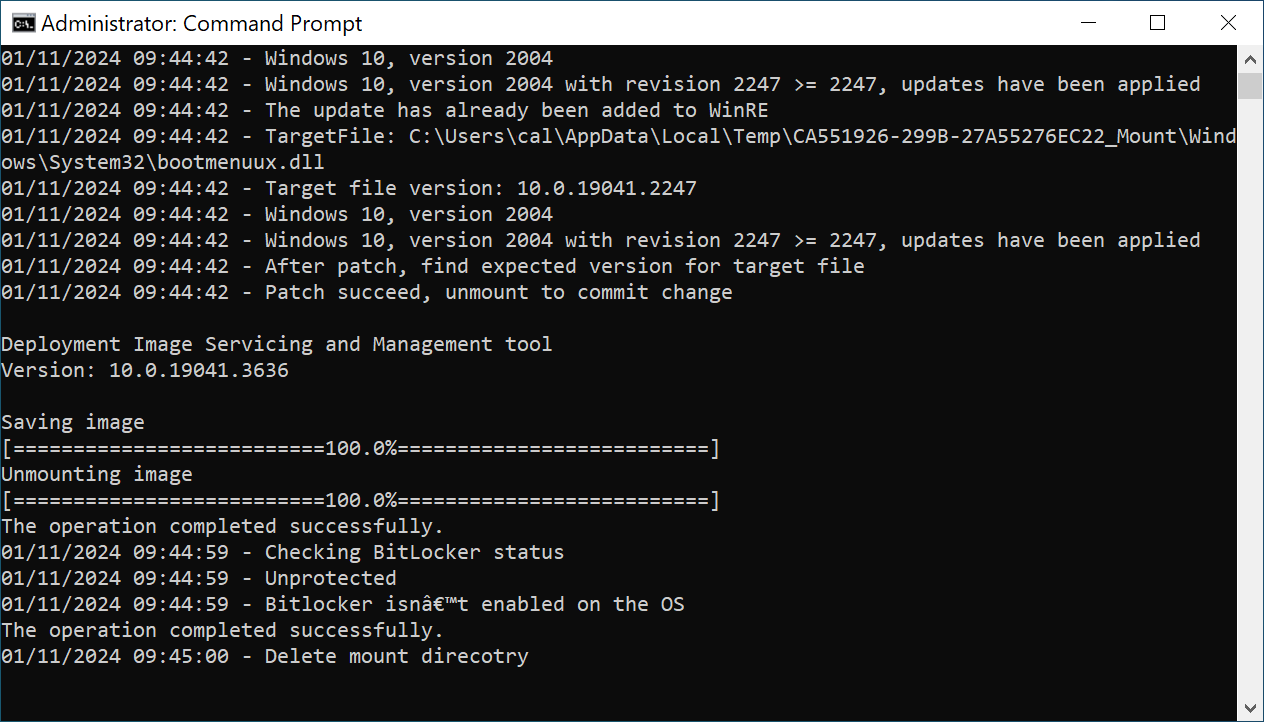
From BleepingComputer’s tests, you may also have to use Microsoft’s Show or Hide Tool to hide the KB5034441 update after running the script, so Windows Update won’t keep trying to install the buggy update and display an error.
Patch management company Action1 also released scripts that automate the resizing of the Windows Recovery Environment (WinRE) partition if you prefer to go that route.
If you choose to manually resize the WinRE partition or use Action1’s scripts, it’s strongly advised to back up your data since there’s always the risk of your system’s partitions getting damaged when adjusted.
Update: Added details on Action1 scripts.





