Security researchers have discovered a critical vulnerability in Microsoft Teams that allows attackers to bypass all Defender for Office 365 protections by inviting users into malicious tenant environments.
The flaw exploits a fundamental architectural gap in how Teams handles cross-tenant collaboration and guest access.
The vulnerability centers on a critical misunderstanding held by most security teams. When employees accept guest invitations to external Teams tenants, they lose all security protections provided by their home organisation.
Instead, they fall under the security policies or lack thereof, of the hosting tenant, where attackers can turn off all defences.
The Perfect Attack Vector
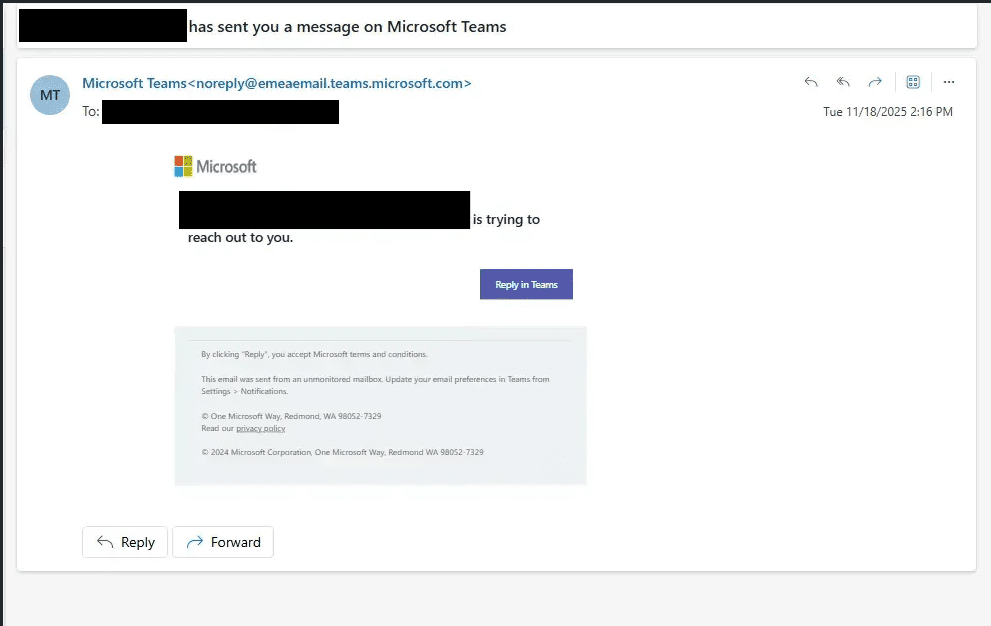
Microsoft’s November 2025 rollout of feature MC1182004, which allows Teams users to initiate chats with anyone using just an email address, has made this attack far more practical.
The feature is enabled by default across all tenants worldwide and requires no opt-in from organisations.
Here’s how the attack works: An attacker sets up a low-cost Microsoft 365 tenant such as a Teams Essentials trial or Business Basic subscription.
These budget licenses don’t include Defender for Office 365, leaving the tenant with no built-in protections. No Safe Links scanning. No malware detection. No Zero-hour Auto Purge. Nothing.
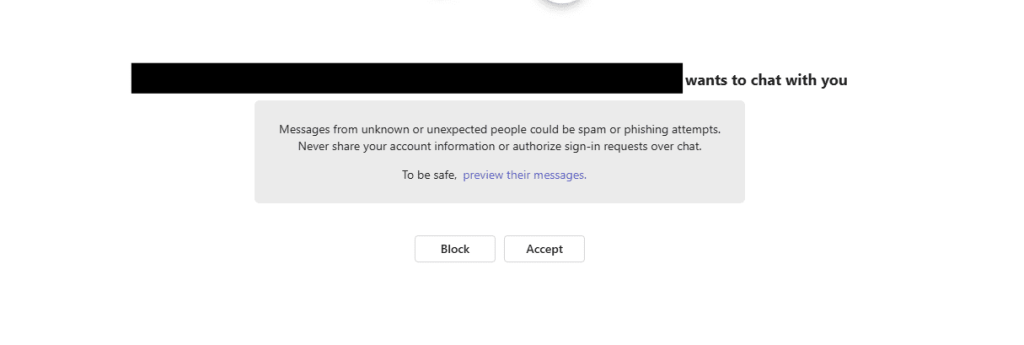
The attacker then uses MC1182004 to send Teams chat invitations to target employees at legitimate organisations, crafted with convincing pretexts like business partnerships or vendor discussions.
When victims accept these invitations, they enter the attacker’s unprotected environment.
Once inside, attackers can send phishing links without triggering Safe Links scanning, distribute malware without attachment analysis, and conduct social engineering at scale all while the victim’s organisation remains completely unaware.
Their expensive Defender for Office 365 investments never activate because the attack occurs outside their security boundary.
According to Ontinue, the vulnerability also highlights a dangerous default configuration: most organisations accept guest invitations from any Microsoft 365 tenant worldwide without restriction.
Security teams can mitigate this risk by implementing several controls. First, organisations can restrict B2B guest invitations to only trusted domains through Microsoft Entra ID’s External collaboration settings.
Second, they can configure granular cross-tenant access policies to block or restrict B2B collaboration by default.
Third, they can limit external Teams communication through the Teams Admin Center to only specific external domains.
Organisations can also turn off the MC1182004 feature using a PowerShell command, though this only prevents outbound invitations not inbound invitations from malicious tenants.
This flaw doesn’t represent a technical defect in Teams itself, but rather an architectural reality of cross-tenant collaboration that security teams haven’t fully grasped.
As Microsoft continues to expand external collaboration capabilities to support flexible work, organisations must proactively secure their guest access policies before attackers exploit the resulting protection gaps at scale.
The research underscores a critical principle: security protections follow the resource tenant, not the home tenant.
Until organisations understand and act on this distinction, their users remain vulnerable to sophisticated attacks operating in plain sight.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
