The Matanbuchus malware loader has been seen being distributed through social engineering over Microsoft Teams calls impersonating IT helpdesk.
Matanbuchus is a malware-as-a-service operation seen promoted on the dark web first in early 2021. It was advertised as a $2,500 Windows loader that executes malicious payloads directly in memory to evade detection.
In June 2022, threat analyst Brad Duncan reported that the malware loader was being used to deliver Cobalt Strike beacons in a large-scale malspam campaign.
Researchers at Morphisec endpoint threat prevention company found that the latest analyzed version of Matanbuchus includes enhanced evasion, obfuscation, and post-compromise capabilities.
Microsoft Teams abuse
Microsoft Teams has been abused over the past years to breach organizations using social engineering to deliver the first stage malware.
Typically, attackers infiltrate the chat and trick users into downloading a malicious file that then introduces the initial payload on system.
In 2023, a researcher created a specialized tool that exploited bugs in the software to allow malware delivery from external accounts.
Last year, DarkGate malware operators abused Microsoft Teams to deliver their loader onto targets who used lax ‘External Access’ settings.
According to Morphisec, operators of the latest Matanbuchus variant, 3.0, also show a preference for Microsoft Teams for initial access.
The attacker initiates an external Microsoft Teams call, posing as a legitimate IT helpdesk, convincing the target to launch Quick Assist, the remote support tool built into Windows.
Quick Assist enables the attacker to gain interactive remote access and follow up by instructing the user to execute a PowerShell script.
This script downloads and extracts a ZIP archive with three files that are used to launch the Matanbuchus loader on the device via DLL side-loading.
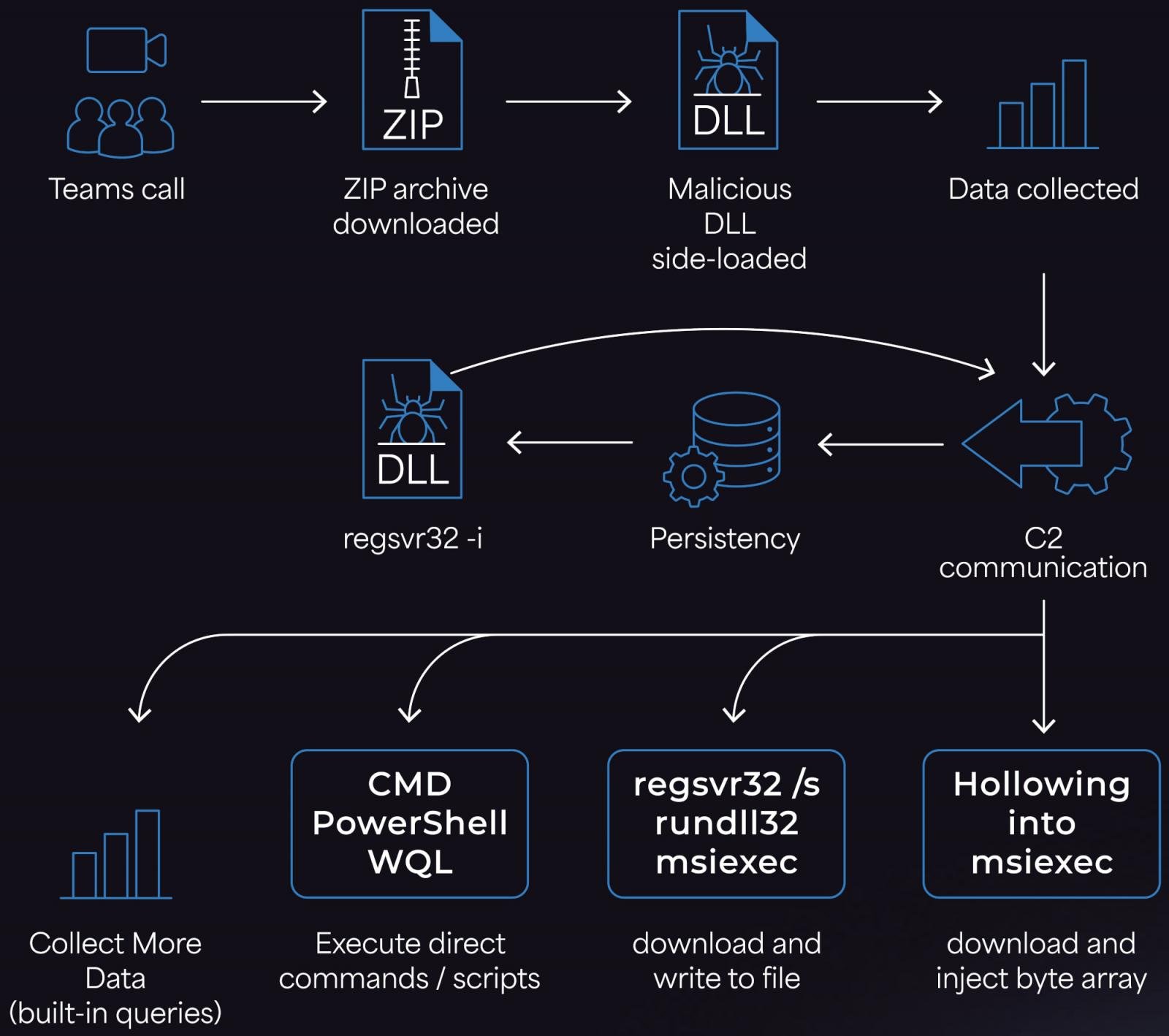
Source: Morphisec
Matanbuchus 3.0
Morphisec reports that Matanbuchus 3.0 introduces several new features and enhancements. The developers switched the command-and-control (C2) communication and string obfuscation from RC4 to Salsa20
The payloads are now launched in memory, and there is a new anti-sandbox verification routine to make sure that the malware runs only on the defined locales.
Instead of calling Windows API functions, the malware now executes syscalls via custom shellcode that bypasses Windows API wrappers and EDR hooks, hiding actions that are commonly monitored by security tools.
API calls are further obfuscated by using the ‘MurmurHash3’ non-cryptographic hash function, which makes reverse engineering and static analysis more difficult.
Regarding Matanbuchus 3.0 post-infection capabilities, it can execute CMD commands, PowerShell, or EXE, DLL, MSI, and shellcode payloads.
The malware collects details such as username, domain, OS build information, running EDR/AV processes, and the elevation status of its process (admin or regular user).
Morphisec’s anlysis found that the malware checks the running processes to identify security tools on the system, noting that the exection methods sent back from the C2 “are likely dependent on the current security stack of the victim.”
The researchers published a detailed technical analysis of the malware and say that Matanbuchus has developed “into a sophisticated threat.”
They also provide indicators of compromise that include malware samples and domains used by the malware.

Contain emerging threats in real time – before they impact your business.
Learn how cloud detection and response (CDR) gives security teams the edge they need in this practical, no-nonsense guide.




