
Microsoft on Wednesday took the lid off a “novel and distinct Russian threat actor,” which it said is linked to the General Staff Main Intelligence Directorate (GRU) and has a “relatively low success rate.”
The tech giant’s Threat Intelligence team, which was previously tracking the group under its emerging moniker DEV-0586, has graduated it to a named actor dubbed Cadet Blizzard.
“Cadet Blizzard seeks to conduct disruption, destruction, and information collection, using whatever means are available and sometimes acting in a haphazard fashion,” the company said.
“While the group carries high risk due to their destructive activity, they appear to operate with a lower degree of operational security than that of longstanding and advanced Russian groups such as Seashell Blizzard and Forest Blizzard.”

Cadet Blizzard first came to light in January 2022 in connection with destructive cyber activity targeting Ukraine using a novel wiper malware called WhisperGate (aka PAYWIPE) in the weeks leading to Russia’s military invasion of the country.
The state-sponsored actor, per Microsoft, has a track record of orchestrating destructive attacks, espionage, and information operations aimed at entities located in Ukraine, Europe, Central Asia, and, periodically, Latin America.
Suspected to have been operational in some capacity since at least 2020, intrusions mounted by Cadet Blizzard have predominantly focused on government agencies, law enforcement, non-profit and non-governmental organizations, IT service providers, and emergency services.
“Cadet Blizzard is active seven days a week and has conducted its operations during its primary targets’ off-business hours when its activity is less likely to be detected,” Microsoft’s Tom Burt said. “In addition to Ukraine, it also focuses on NATO member states involved in providing military aid to Ukraine.”
It’s worth noting that Cadet Blizzard also overlaps with groups monitored by the broader cybersecurity community under the names Ember Bear (CrowdStrike), FROZENVISTA (Google TAG), Nodaria (Symantec), TA471 (Proofpoint), UAC-0056 (CERT-UA), and UNC2589 (Google Mandiant).
Besides WhisperGate, the hacking crew is known to leverage a raft of weapons for its arsenal, including SaintBot, OutSteel, GraphSteel, GrimPlant, and more recently, Graphiron. Microsoft has attributed SaintBot and OutSteel to a related activity cluster labeled Storm-0587.
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
Join the Session
“Cadet Blizzard is also linked to the defacements of several Ukrainian organization websites, as well as multiple operations, including the hack-and-leak forum known as ‘Free Civilian,'” Microsoft added.
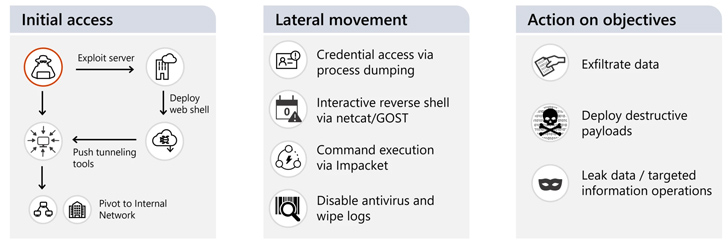
Other notable tradecraft entails the use of living-off-the-land (LotL) techniques post gaining initial access to achieve lateral movement, collect credentials and other information, and deploy tools to facilitate defense evasion and persistence.
The cyber assaults, for their part, are accomplished through the exploitation of known flaws in exposed web servers (e.g., Atlassian Confluence and Microsoft Exchange Server) and content management systems.
“As the war continues, Cadet Blizzard activity poses an increasing risk to the broader European community, specifically any successful attacks against governments and IT service providers, which may give the actor both tactical and strategic-level insight into Western operations and policy surrounding the conflict,” Microsoft noted.
