Microsoft will soon start rolling out Conditional Access policies requiring multifactor authentication (MFA) from administrators when signing into Microsoft admin portals such as Microsoft Entra, Microsoft 365, Exchange, and Azure.
The company will also roll out policies that will require MFA for per-user MFA users for all cloud apps and one that will require MFA for high-risk sign-ins (the latter only available to Microsoft Entra ID Premium Plan 2 customers).
These Microsoft-managed policies will gradually be added in report-only mode to eligible Microsoft Entra tenants starting next week. After the rollout reaches their tenant, admins will have 90 days to review them and choose if they want to enable them or not.
Redmond will automatically enable these Conditional Access policies only on tenants where they weren’t toggled off within 90 days after the rollout.
“Pay lots of attention to the first policy. It’s our strong recommendation—and a policy we’ll deploy your behalf—that multifactor authentication protect all user access to admin portals such as https://portal.azure.com, Microsoft 365 admin center, and Exchange admin center,” said Microsoft Vice President for Identity Security Alex Weinert.
“Please note that while you can opt out of these policies, teams at Microsoft will increasingly require multifactor authentication for specific interactions, as they already do for certain Azure subscription management scenarios, Partner Center, and Microsoft Intune device enrollment.”
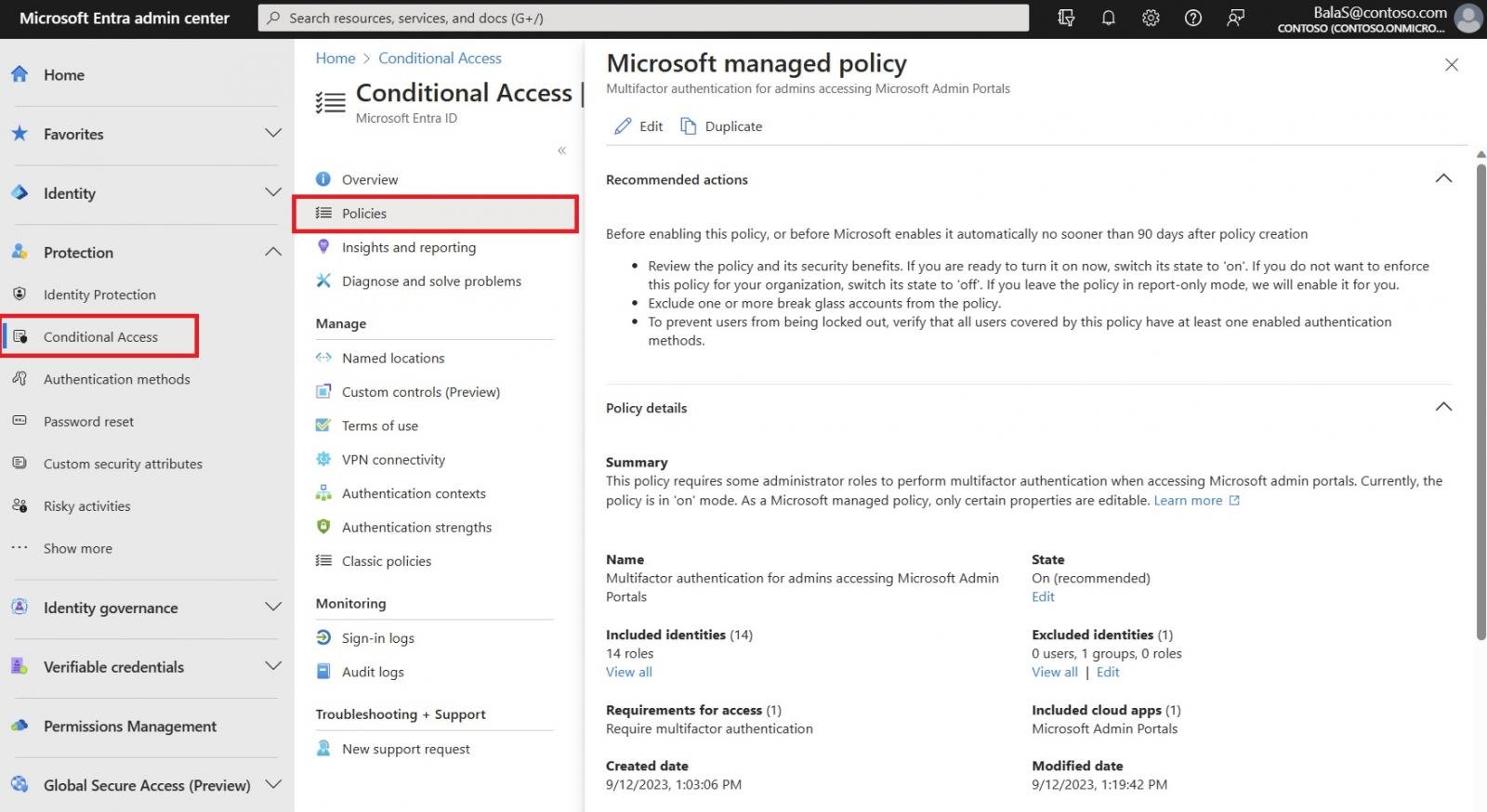
Once added, administrators with at least the Conditional Access Administrator role can find these policies in the Microsoft Entra admin center under Protection > Conditional Access > Policies.
They can also modify the state (On, Off, or Report-only) for all Microsoft-managed policies, as well as excluded identities (Users, Groups, and Roles) within the policy.
Redmond advises organizations to exclude emergency access or break-glass accounts from these policies, just as they would with other Conditional Access policies.
Microsoft also provides the option to modify these policies further by cloning them using the Duplicate button in the policy list view and tailoring them like any other Conditional Access policy, starting with Microsoft-recommended defaults.
“Our goal is 100 percent multifactor authentication. Given that formal studies show multifactor authentication reduces the risk of account takeover by over 99 percent, every user who authenticates should do so with modern strong authentication,” Weinert said.
“Our eventual goal is to combine machine learning-based policy insights and recommendations with automated policy rollout to strengthen your security posture on your behalf with the right controls.”
