A common adage among cybersecurity professionals is that when it comes to cyber-attacks, it’s not a matter of if but when. Despite this certainty, organizations are often caught off-guard when inevitable data breaches occur; rather than focusing on mitigating risks and preventing further harm to the organization, security teams find themselves tied up in tasks that they could have proactively prepared for in advance.
Organizations should therefore position themselves to react swiftly and comprehensively once security incidents occur—this includes equipping themselves with the capability of performing mass password resets. This article explores some of the common scenarios, challenges, and best practices for that scenario.
Common mass password reset scenarios
Cyber attackers rely on a myriad of threat vectors to gain unauthorized access to an organization’s systems and networks, usually starting with compromised user accounts as an entry point into privileged environments. Security teams may not know the extent to which attackers have infiltrated their systems, but upon detecting even a handful of compromised accounts, they may decide a mass password reset on all user accounts is needed.
This is likely to cause some degree of disruption and support overhead but is highly recommended in various security incidents. The following are a few common scenarios that may require a mass password reset:
- Many corporate email account credentials detected on the dark web
- Compromised cloud or third-party identity/access management service
- Compromised root, domain admin, or privileged accounts and groups
- Organization-wide ransomware attacks
- Cyber-attacks carried out by known nation state actors or advanced persistent threats (APT)
Implementing an organization-wide password reset is likely to disrupt critical work and create support issues that may overwhelm IT service desks.
IT and security staff should therefore prepare ahead of time for such incidents, with both policies and tools for streamlining mass password resets.
The Transport for London (TfL) cyber attack
Recently, Transport for London (TfL), the organization responsible for most of London’s transport network, suffered a massive cyber-attack that resulted in widespread operational disruption and havoc. The malicious actor succeeded in forcing TfL to shutter several operations in efforts to limit their further access; furthermore, general IT chaos ensued as TfL underwent a massive undertaking to secure its user accounts.
Unfortunately, both customers and employees were impacted by the incident. TfL disclosed that some customer data had been stolen, including names, addresses, contact details and bank details. And because of the compromised employee accounts, many of TfL’s staff had limited access to systems and were delayed in their ability to respond to online enquiries.
Part of the organization’s required response measures included the manual, in-person resetting of 30,000 employee passwords. Employees were required to attend in-person, password reset appointments—a herculean scheduling and processing effort centrally managed by TfL to enable workers to regain access to applications and data.
TfL’s recent cyber-attack serves to illustrate the importance of having robust security measures in place that include self-service password reset solutions. And while TfL’s incident was a targeted attack, organizations can just as easily fall victim to indiscriminate ransomware attacks and random phishing attempts that result in widespread account compromises.
For example, the University of Waterloo suffered a ransomware attack against their Microsoft Exchange email services that resulted in the resetting of password for 42,000 people, to include faculty/staff, employee/non-employee grad students, undergraduates, and all remaining students.
So what’s the alternative to everyone physically resetting their password with the IT team? By enabling users to reset their own passwords, security teams can avoid manual password resetting efforts and focus instead on investigating incidents and closing security gaps.
Self-service password reset solutions
Mass password resets not only required measures that follow cyber-attacks and data breaches, but they also serve as preventative measures for reducing the risk of compromises and security incidents to begin with, on an ongoing basis. As part of an organization’s password policy, there are a number of reasons why an end-user might need to change their password.
Self-service password reset tools like Specops uReset makes the process simple for end users, who can verify themselves remotely.
Your end-users will be able to safely and independently reset their passwords and modify their locally stored login information, without needing to use a VPN. It also greatly reduces the burden on IT team and service desks, who would otherwise have to spend time physically helping users reset their passwords or unlocking their accounts if something goes wrong.
Your organization can also choose from a variety of authentication methods such as biometric verification, SMS authentication, email verification, and third-party authenticators like Google Authenticator to add MFA to the self-service password reset process .
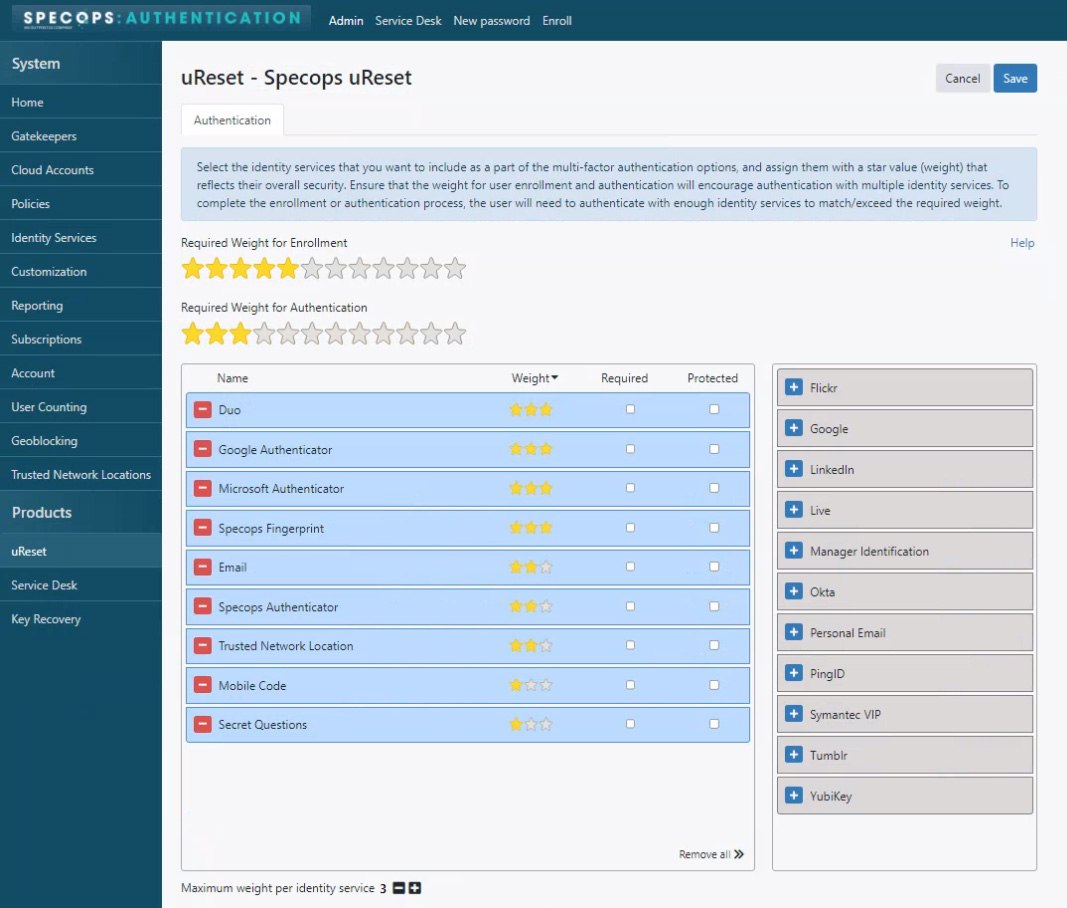
By providing users with the ability to self-service their password resets, organizations can significantly free up time and resources for security and IT teams—both during cyberattacks and as part of daily operations.
To learn more about how Specops uReset can mitigate your organization’s password risk exposure and lower IT support overhead, try it for free today or speak to an expert for more information.
Sponsored and written by Specops Software.
