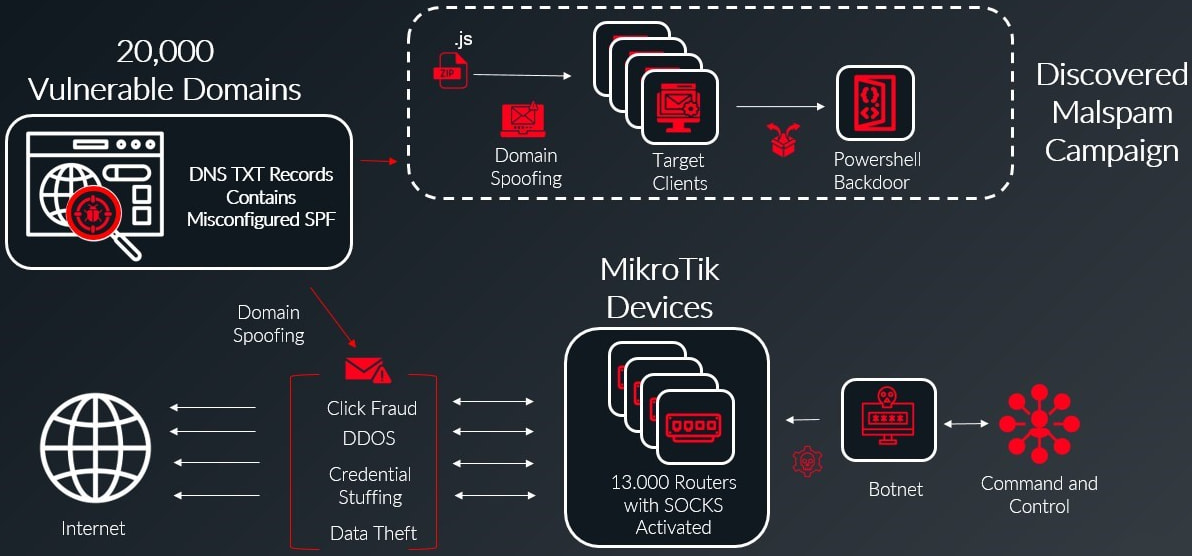
A newly discovered botnet of 13,000 MikroTik devices uses a misconfiguration in domain name server records to bypass email protections and deliver malware by spoofing roughly 20,000 web domains.
The threat actor takes advantage of an improperly configured DNS record for the sender policy framework (SPF) used for listing all the servers authorized to send emails on behalf of a domain.
Misconfigured SPF record
According to DNS security company Infoblox, the malspam campaign was active in late November 2024. Some of the emails impersonated DHL Express shipping company and delivered fake freight invoices with a ZIP archive containing a malicious payload.
Inside the ZIP attachment there was a JavaScript file that assembles and runs a PowerShell script. The script establishes a connection to the threat actor’s command and control (C2) server at a domain previously tied to Russian hackers.
“The headers of the many spam emails revealed a vast array of domains and SMTP server IP addresses, and we realized we had uncovered a sprawling network of approximately 13,000 hijacked MikroTik devices, all part of a sizeable botnet,” explains Infoblox.
Infoblox explains that SPF DNS records for about 20,000 domains were configured with the overly permissive “+all” option, which allows any server to send emails on behalf of those domains.
“This essentially defeats the purpose of having an SPF record, because it opens the door for spoofing and unauthorized email sending” – Infoblox
A safer choice is using the “-all” option, which limits email sending to the servers specified by the domain.
Source: Infoblox
MikroTik powering yet another botnet
The compromise method remains unclear but Infoblox says they “saw a variety of versions impacted, including recent [MikroTik] firmware releases.”
MikroTik routers are known for being powerful and threat actors targeted them to create botnets capable of very powerful attacks.
Just last summer, cloud services provider OVHcloud blamed a botnet of compromised MikroTik devices for a massive denial-of-service attack that peaked at a record 840 million packets per second.
Despite urging MikroTik device owners to update the systems, many of the routers remain vulnerable for extended periods of time because of a very slow patch rate.
The botnet in this case configured the devices as SOCKS4 proxies to launch DDoS attacks, send phishing emails, exfiltrate data, and generally help mask the origin of malicious traffic.
“Even though the botnet consists of 13,000 devices, their configuration as SOCKS proxies allows tens or even hundreds of thousands of compromised machines to use them for network access, significantly amplifying the potential scale and impact of the botnet’s operations,” comments Infoblox.
MikroTik device owners are advised to apply the latest firmware update for their model, change the default admin account credentials, and close remote access to control panels if not needed.
