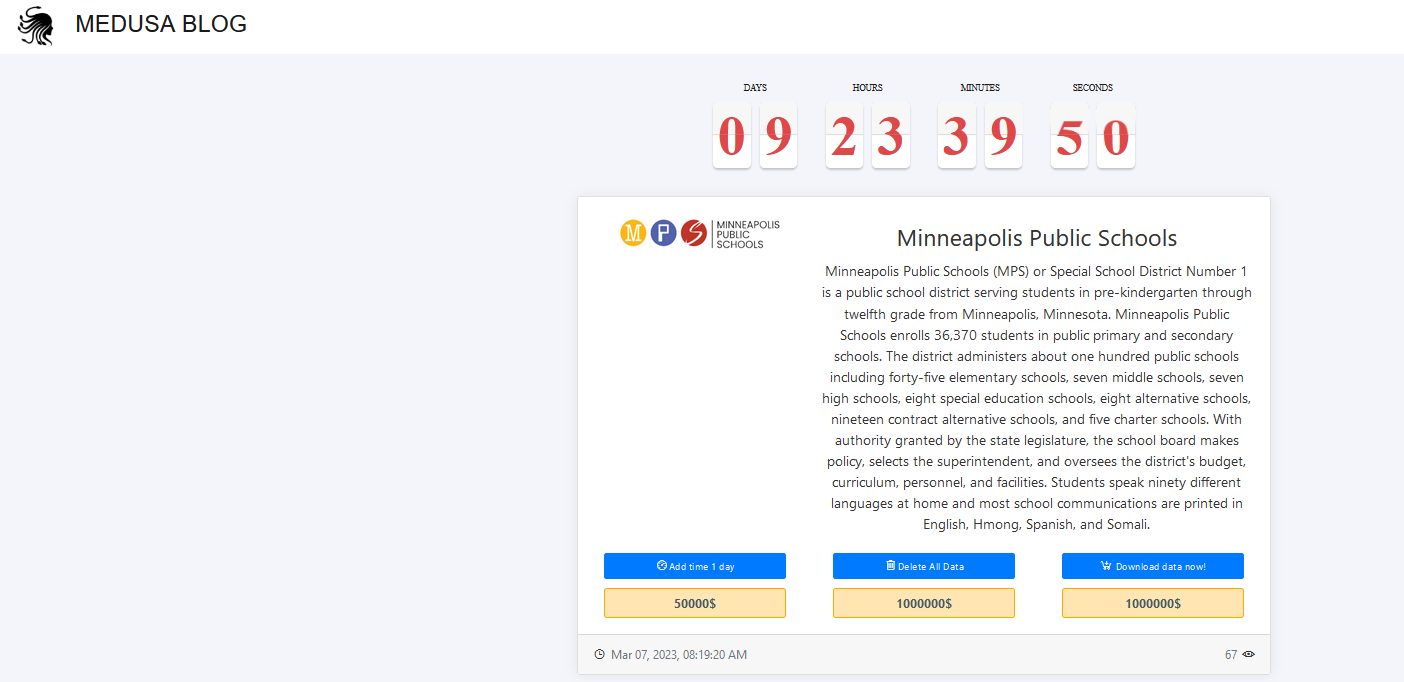
Medusa ransomware gang has slapped a million-dollar ransom note on the Minneapolis Public Schools District, days after the school district confirmed the ransomware attack.
The MPS administrators on February 7 alerted about a “threat actor” responsible for a recent hacking incident posted some of the stolen data, nearly two weeks after notifying parents of the “encryption event”.
The school district systems went down on February 20. The administration om March 1 confirmed that it was a ransomware attack and stakeholder information was at risk but assured that it has not paid any ransom.
Minneapolis Public Schools (MPS) is a large public school district in the US, serving 36,370 students from pre-kindergarten through twelfth grade across approximately 100 schools.
The district is overseen by a school board and serves a diverse student population with over 90 home languages.
MPS, Medusa ransomware, and US education institutions
Medusa ransomware leak site posted a ransom note on 7 February, naming the Minneapolis Public Schools District. The group has demanded a ransom of one million dollars.
The ransomware group has threatened to release the data pilfered in the ransomware attack by March 16 if the ransom is not paid. The gang would take $50,000 for extending the ransom deadline by a day.
Interestingly, the gang has also offered the data for sale for a million dollars. The samples listed on the leak site includes employee details, email, financial info etc.
The Minneapolis Public Schools District circulated an email among the stakeholders, stating that the incident has been reported to law enforcement and they are currently collaborating with IT experts to analyze the data and notify those affected.
“We want to caution you again about receiving, interacting with, or responding to any suspicious emails or phone calls from someone you do not know related to this event. Be aware of possible phishing events and other potential scams,” said the Minneapolis Public Schools District email.
“Additionally, we continue to recommend changing all passwords for any online personal accounts that you may have accessed on MPS devices.”
MPS and the ransomware attack timeline
February 21
The Minneapolis Public Schools District disclosed that it experienced technical difficulties affecting certain computer systems.
MPS staff, with the help of non-MPS IT specialists, are investigating the source and impact of this disruption and working to restore full functionality, the announcement said.
MPS claimed that the impacted data has been successfully restored from viable backups, meaning no data has been lost.
February 24
The Minneapolis Public Schools District administrators conceded that the technical difficulties disclosed was due to an “encryption event” affecting certain computer systems.
“To date, our investigation has found no evidence that personal information was compromised as a result of this event. If it is determined that personal information has been impacted, we will notify those specifically impacted individuals,” said the announcement.
March 1
The Minneapolis Public Schools District confirmed that the incident was indeed a ransomware attack. MPS urged the community to remain cautious regarding potential phishing events and scams.
“Please note, MPS has not paid a ransom and the investigation has not found any evidence that any data accessed has been used to commit fraud,” said the announcement.
“However, if the ongoing investigation indicates that personal information has been impacted, the impacted individuals will be notified immediately.”
Pandemic, US education, and cybersecurity
As students and teachers moved to online platforms due to the COVID-19 pandemic, the potential for hacking and data breaches at education institutions went up, wrote Nir Kshetri, Professor of Management, University of North Carolina – Greensboro.
US Senator Ron Wyden this week wrote to the Department of Education to provide better cybersecurity software for American schools.
He urged to facilitate pre-negotiated software contracts between schools and educational software providers, which would help lower the cybersecurity cost burden for US schools.
To alleviate the burden on schools and ensure the privacy of students and schools, pre-negotiated contracts with educational technology providers are crucial, he said.
According to him, this would allow educators to prioritize both student learning and privacy, while also levelling the playing field between under-resourced school administrators and big tech companies.
“Technology designed for use in education, or “edtech,” has proliferated in the past decade and accelerated as the COVID-19 pandemic necessitated a switch to remote schooling,” he wrote in the letter.
“While the Family Education Rights and Privacy Act (FERPA) affords some federal protections to student ‘education records,’ the bill’s authors, in 1974, could not have foreseen the high volume and new types of data generated by the digital tools used in schools today. Many edtech companies are taking advantage of these lagging standards.”
Federal agencies have warned educational institutions about growing ransomware threats to school networks, and CISA has released a formal guide to help improve cybersecurity for U.S. schools.